Activate trusted access for StackSets with Amazon Organizations
This topic provides instructions on how to activate trusted access with Amazon Organizations, which is required by StackSets to deploy across accounts and Amazon Web Services Regions using service-managed permissions. To use self-managed permissions, see Grant self-managed permissions instead.
Before you create a StackSet with service-managed permissions, you must first complete the following tasks:
-
Enable all features in Amazon Organizations. With only consolidated billing features enabled, you can't create a StackSet with service-managed permissions.
-
Activate trusted access with Amazon Organizations. This action allows CloudFormation to create a service-linked role in the management account. After trusted access is activated, when you create a StackSet with service-managed permissions, CloudFormation creates both the necessary service-linked role and a service role named
stacksets-exec-*in the target (member) accounts.With trusted access activated, the management account and delegated administrator accounts can create and manage service-managed StackSets for their organization.
To activate trusted access, you must be an administrator user in the management account. An administrator user is a user with full permissions to your Amazon Web Services account. For more information, Create an administrator user in the Amazon Account Management Reference Guide. For recommendations for protecting the security of the management account, see Best practices for the management account in the Amazon Organizations User Guide.
To activate trusted access
-
Sign in to Amazon as an administrator of the management account and open the CloudFormation console at https://console.amazonaws.cn/cloudformation
. -
From the navigation pane, choose StackSets. If trusted access is deactivated, a banner displays that prompts you to activate trusted access.
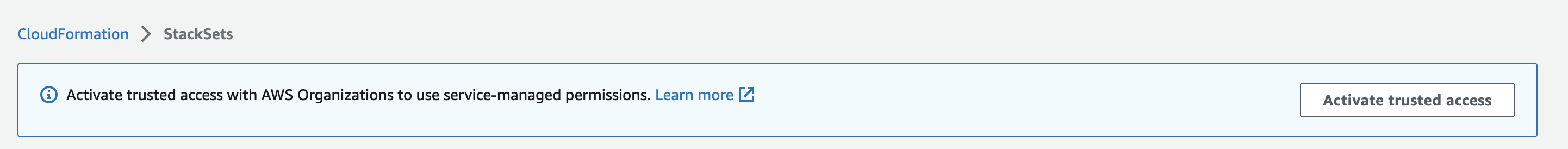
-
Choose Activate trusted access.
Trusted access is successfully activated when the following banner displays.

Note
Activate Organizations Access is the same as Enable Organizations Access, and Deactivate Organizations Access is the same as Disable Organizations Access. These terms have been updated based on marketing guidelines.
To deactivate trusted access
See Amazon CloudFormation StackSets and Amazon Organizations in the Amazon Organizations User Guide.
Before you can deactivate trusted access with Amazon Organizations, you must deregister all delegated administrators. For more information, see Register a delegated administrator.
Note
For information about using API operations instead of the console to activate or deactivate trusted access, see:
Service-linked roles
The management account uses the AWSServiceRoleForCloudFormationStackSetsOrgAdmin service-linked role. You can modify or delete this role only if trusted access with Amazon Organizations is deactivated.
Each target account uses a AWSServiceRoleForCloudFormationStackSetsOrgMember service-linked role. You can modify or delete this role only under two conditions: if trusted access with Amazon Organizations is deactivated, or if the account is removed from the target organization or organizational unit (OU).
For more information, see Amazon CloudFormation StackSets and Amazon Organizations in the Amazon Organizations User Guide.