Tutorial: Install a LAMP server on AL2023
The following procedures help you install an Apache web server with PHP and MariaDB
Important
These procedures are intended for use with AL2023. If you are trying to set up a
LAMP web server on a different distribution, such as Ubuntu or Red Hat Enterprise Linux,
this tutorial will not work. For Ubuntu, see the following
Ubuntu community documentation: ApacheMySQLPHP
Tasks
Step 1: Prepare the LAMP server
Prerequisites
-
This tutorial assumes that you have already launched a new instance using AL2023, with a public DNS name that is reachable from the internet. For more information, see AL2023 on Amazon EC2. You must also have configured your security group to allow SSH (port 22), HTTP (port 80), and HTTPS (port 443) connections. For more information about these prerequisites, see Authorize inbound traffic for your Linux instances in the Amazon EC2 User Guide.
-
The following procedure installs the latest PHP version available on AL2023, currently 8.1. If you plan to use PHP applications other than those described in this tutorial, you should check their compatibility with 8.1.
To prepare the LAMP server
-
Connect to your instance. For more information, see Connecting to AL2023 instances.
-
To ensure that all of your software packages are up to date, perform a quick software update on your instance. This process might take a few minutes, but it is important to make sure that you have the latest security updates and bug fixes.
The
-yoption installs the updates without asking for confirmation. If you would like to examine the updates before installing, you can omit this option.[ec2-user ~]$sudo dnf upgrade -y -
Install the latest versions of Apache web server and PHP packages for AL2023.
[ec2-user ~]$sudo dnf install -y httpd wget php-fpm php-mysqli php-json php php-devel -
Install the MariaDB software packages. Use the dnf install command to install multiple software packages and all related dependencies at the same time.
[ec2-user ~]$sudo dnf install mariadb105-serverYou can view the current versions of these packages using the following command:
[ec2-user ~]$sudo dnf infopackage_nameExample:
[root@ip-172-31-25-170 ec2-user]# dnf info mariadb105 Last metadata expiration check: 0:00:16 ago on Tue Feb 14 21:35:13 2023. Installed Packages Name : mariadb105 Epoch : 3 Version : 10.5.16 Release : 1.amzn2023.0.6 Architecture : x86_64 Size : 18 M Source : mariadb105-10.5.16-1.amzn2023.0.6.src.rpm Repository : @System From repo : amazonlinux Summary : A very fast and robust SQL database server URL : http://mariadb.org License : GPLv2 and LGPLv2 Description : MariaDB is a community developed fork from MySQL - a multi-user, multi-threaded : SQL database server. It is a client/server implementation consisting of : a server daemon (mariadbd) and many different client programs and libraries. : The base package contains the standard MariaDB/MySQL client programs and : utilities. -
Start the Apache web server.
[ec2-user ~]$sudo systemctl start httpd -
Use the systemctl command to configure the Apache web server to start at each system boot.
[ec2-user ~]$sudo systemctl enable httpdYou can verify that httpd is on by running the following command:
[ec2-user ~]$sudo systemctl is-enabled httpd -
Add a security rule to allow inbound HTTP (port 80) connections to your instance if you have not already done so. By default, a launch-wizard-
Nsecurity group was created for your instance during launch. If you did not add additional security group rules, this group contains only a single rule to allow SSH connections.Open the Amazon EC2 console at https://console.amazonaws.cn/ec2/
. In the left navigator, choose Instances, and select your instance.
-
On the Security tab, view the inbound rules. You should see the following rule:
Port range Protocol Source 22 tcp 0.0.0.0/0Warning
Using
0.0.0.0/0allows all IPv4 addresses to access your instance using SSH. This is acceptable for a short time in a test environment, but it's unsafe for production environments. In production, you authorize only a specific IP address or range of addresses to access your instance. -
If there is no inbound rule to allow HTTP (port 80) connections, you must the add rule now. Choose the link for the security group. Using the procedures in see Authorize inbound traffic for your Linux instances, add a new inbound security rule with the following values:
-
Type: HTTP
-
Protocol: TCP
-
Port Range: 80
-
Source: Custom
-
-
Test your web server. In a web browser, type the public DNS address (or the public IP address) of your instance. If there is no content in
/var/www/html, you should see the Apache test page, which will display the message "It works!".You can get the public DNS for your instance using the Amazon EC2 console (check the Public IPv4 DNS column; if this column is hidden, choose Preferences (the gear-shaped icon) and toggle on Public IPv4 DNS).
Verify that the security group for the instance contains a rule to allow HTTP traffic on port 80. For more information, see Add rules to security group.
Important
If you are not using Amazon Linux, you might also need to configure the firewall on your instance to allow these connections. For more information about how to configure the firewall, see the documentation for your specific distribution.
Apache httpd serves files that are kept in a directory called the
Apache document root. The Amazon Linux Apache document root is /var/www/html,
which by default is owned by root.
To allow the ec2-user account to manipulate files in this directory, you
must modify the ownership and permissions of the directory. There are many ways to
accomplish this task. In this tutorial, you add ec2-user to the
apache group to give the apache group ownership of the
/var/www directory and assign write permissions to the
group.
To set file permissions
-
Add your user (in this case,
ec2-user) to theapachegroup.[ec2-user ~]$sudo usermod -a -G apacheec2-user -
Log out and then log back in again to pick up the new group, and then verify your membership.
-
Log out (use the exit command or close the terminal window):
[ec2-user ~]$exit -
To verify your membership in the
apachegroup, reconnect to your instance, and then run the following command:[ec2-user ~]$groupsec2-user adm wheel apache systemd-journal
-
-
Change the group ownership of
/var/wwwand its contents to theapachegroup.[ec2-user ~]$sudo chown -R ec2-user:apache /var/www -
To add group write permissions and to set the group ID on future subdirectories, change the directory permissions of
/var/wwwand its subdirectories.[ec2-user ~]$sudo chmod 2775 /var/www && find /var/www -type d -exec sudo chmod 2775 {} \; -
To add group write permissions, recursively change the file permissions of
/var/wwwand its subdirectories:[ec2-user ~]$find /var/www -type f -exec sudo chmod 0664 {} \;
Now, ec2-user (and any future members of the apache group) can add,
delete, and edit files in the Apache document root, enabling you to add content, such
as a static website or a PHP application.
To secure your web server (Optional)
A web server running the HTTP protocol provides no transport security for the data that it sends or receives. When you connect to an HTTP server using a web browser, the URLs that you visit, the content of webpages that you receive, and the contents (including passwords) of any HTML forms that you submit are all visible to eavesdroppers anywhere along the network pathway. The best practice for securing your web server is to install support for HTTPS (HTTP Secure), which protects your data with SSL/TLS encryption.
For information about enabling HTTPS on your server, see Tutorial: Configure SSL/TLS on AL2023.
Step 2: Test your LAMP server
If your server is installed and running, and your file permissions are set correctly,
your ec2-user account should be able to create a PHP file in the
/var/www/html directory that is available from the
internet.
To test your LAMP server
-
Create a PHP file in the Apache document root.
[ec2-user ~]$echo "<?php phpinfo(); ?>" > /var/www/html/phpinfo.phpIf you get a "Permission denied" error when trying to run this command, try logging out and logging back in again to pick up the proper group permissions that you configured in To set file permissions.
-
In a web browser, type the URL of the file that you just created. This URL is the public DNS address of your instance followed by a forward slash and the file name. For example:
http://my.public.dns.amazonaws.com/phpinfo.phpYou should see the PHP information page:

If you do not see this page, verify that the
/var/www/html/phpinfo.phpfile was created properly in the previous step. You can also verify that all of the required packages were installed with the following command.[ec2-user ~]$sudo dnf list installed httpd mariadb-server php-mysqlndIf any of the required packages are not listed in your output, install them with the sudo yum install
packagecommand. -
Delete the
phpinfo.phpfile. Although this can be useful information, it should not be broadcast to the internet for security reasons.[ec2-user ~]$rm /var/www/html/phpinfo.php
You should now have a fully functional LAMP web server. If you add content to the Apache
document root at /var/www/html, you should be able to view that content
at the public DNS address for your instance.
Step 3: Secure the database server
The default installation of the MariaDB server has several features that are great for testing and development, but they should be disabled or removed for production servers. The mysql_secure_installation command walks you through the process of setting a root password and removing the insecure features from your installation. Even if you are not planning on using the MariaDB server, we recommend performing this procedure.
To secure the MariaDB server
-
Start the MariaDB server.
[ec2-user ~]$sudo systemctl start mariadb -
Run mysql_secure_installation.
[ec2-user ~]$sudo mysql_secure_installation-
When prompted, type a password for the root account.
-
Type the current root password. By default, the root account does not have a password set. Press Enter.
-
Type
Yto set a password, and type a secure password twice. For more information about creating a secure password, see https://identitysafe.norton.com/password-generator/. Make sure to store this password in a safe place. Setting a root password for MariaDB is only the most basic measure for securing your database. When you build or install a database-driven application, you typically create a database service user for that application and avoid using the root account for anything but database administration.
-
-
Type
Yto remove the anonymous user accounts. -
Type
Yto disable the remote root login. -
Type
Yto remove the test database. -
Type
Yto reload the privilege tables and save your changes.
-
-
(Optional) If you do not plan to use the MariaDB server right away, stop it. You can restart it when you need it again.
[ec2-user ~]$sudo systemctl stop mariadb -
(Optional) If you want the MariaDB server to start at every boot, type the following command.
[ec2-user ~]$sudo systemctl enable mariadb
Step 4: (Optional) Install phpMyAdmin
phpMyAdminphpMyAdmin on
your Amazon Linux instance.
Important
We do not recommend using phpMyAdmin to access a LAMP server unless
you have enabled SSL/TLS in Apache; otherwise, your database administrator password
and other data are transmitted insecurely across the internet. For security
recommendations from the developers, see Securing your phpMyAdmin installation
To install phpMyAdmin
-
Install the required dependencies.
[ec2-user ~]$sudo dnf install php-mbstring php-xml -y -
Restart Apache.
[ec2-user ~]$sudo systemctl restart httpd -
Restart
php-fpm.[ec2-user ~]$sudo systemctl restart php-fpm -
Navigate to the Apache document root at
/var/www/html.[ec2-user ~]$cd /var/www/html -
Select a source package for the latest phpMyAdmin release from https://www.phpmyadmin.net/downloads
. To download the file directly to your instance, copy the link and paste it into a wget command, as in this example: [ec2-user html]$wgethttps://www.phpmyadmin.net/downloads/phpMyAdmin-latest-all-languages.tar.gz -
Create a
phpMyAdminfolder and extract the package into it with the following command.[ec2-user html]$mkdir phpMyAdmin && tar -xvzfphpMyAdmin-latest-all-languages.tar.gz-C phpMyAdmin --strip-components 1 -
Delete the
phpMyAdmin-latest-all-languages.tar.gztarball.[ec2-user html]$rmphpMyAdmin-latest-all-languages.tar.gz -
(Optional) If the MySQL server is not running, start it now.
[ec2-user ~]$sudo systemctl start mariadb -
In a web browser, type the URL of your phpMyAdmin installation. This URL is the public DNS address (or the public IP address) of your instance followed by a forward slash and the name of your installation directory. For example:
http://my.public.dns.amazonaws.com/phpMyAdminYou should see the phpMyAdmin login page:
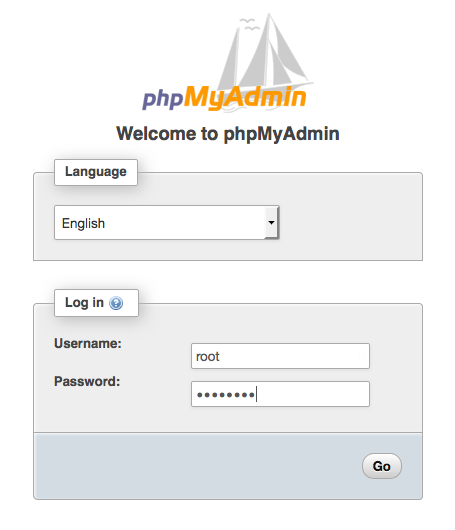
-
Log in to your phpMyAdmin installation with the
rootuser name and the MySQL root password you created earlier.Your installation must still be configured before you put it into service. We suggest that you begin by manually creating the configuration file, as follows:
-
To start with a minimal configuration file, use your favorite text editor to create a new file, and then copy the contents of
config.sample.inc.phpinto it. -
Save the file as
config.inc.phpin the phpMyAdmin directory that containsindex.php. -
Refer to post-file creation instructions in the Using the Setup script
section of the phpMyAdmin installation instructions for any additional setup.
For information about using phpMyAdmin, see the phpMyAdmin User Guide
. -
Troubleshoot
This section offers suggestions for resolving common problems you might encounter while setting up a new LAMP server.
I can't connect to my server using a web browser
Perform the following checks to see if your Apache web server is running and accessible.
-
Is the web server running?
You can verify that httpd is on by running the following command:
[ec2-user ~]$sudo systemctl is-enabled httpdIf the httpd process is not running, repeat the steps described in To prepare the LAMP server.
-
Is the firewall correctly configured?
Verify that the security group for the instance contains a rule to allow HTTP traffic on port 80. For more information, see Add rules to security group.
I can't connect to my server using HTTPS
Perform the following checks to see if your Apache web server is configured to support HTTPS.
-
Is the web server correctly configured?
After you install Apache, the server is configured for HTTP traffic. To support HTTPS, enable TLS on the server and install an SSL certificate. For information, see Tutorial: Configure SSL/TLS on AL2023.
-
Is the firewall correctly configured?
Verify that the security group for the instance contains a rule to allow HTTPS traffic on port 443. For more information, see Authorize inbound traffic for your Linux instances.
Related topics
For more information about transferring files to your instance or installing a WordPress blog on your web server, see the following documentation:
-
Transfer files to your Linux instance using WinSCP in the Amazon EC2 User Guide.
-
Transfer files to Linux instances using an SCP client in the Amazon EC2 User Guide.
For more information about the commands and software used in this tutorial, see the following webpages:
-
Apache web server: http://httpd.apache.org/
-
MariaDB database server: https://mariadb.org/
-
PHP programming language: http://php.net/
For more information about registering a domain name for your web server, or transferring an existing domain name to this host, see Creating and Migrating Domains and Subdomains to Amazon Route 53 in the Amazon Route 53 Developer Guide.