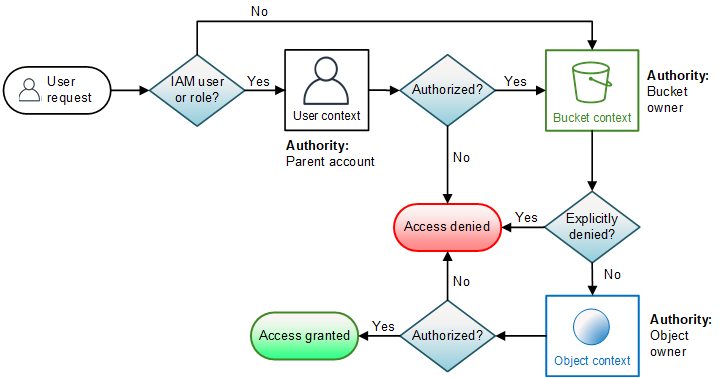
How Amazon S3 authorizes a request for an object operation
When Amazon S3 receives a request for an object operation, it converts all the relevant permissions— resource-based permissions (object access control list (ACL), bucket policy, bucket ACL) and IAM user policies—into a set of policies to be evaluated at run time. It then evaluates the resulting set of policies in a series of steps. In each step, it evaluates a subset of policies in three specific contexts—user context, bucket context, and object context:
-
User context – If the requester is an IAM principal, the principal must have permission from the parent Amazon Web Services account to which it belongs. In this step, Amazon S3 evaluates a subset of policies owned by the parent account (also referred as the context authority). This subset of policies includes the user policy that the parent attaches to the principal. If the parent also owns the resource in the request (bucket or object), Amazon S3 evaluates the corresponding resource policies (bucket policy, bucket ACL, and object ACL) at the same time.
Note
If the parent Amazon Web Services account owns the resource (bucket or object), it can grant resource permissions to its IAM principal by using either the user policy or the resource policy.
-
Bucket context – In this context, Amazon S3 evaluates policies owned by the Amazon Web Services account that owns the bucket.
If the Amazon Web Services account that owns the object in the request is not same as the bucket owner, Amazon S3 checks the policies if the bucket owner has explicitly denied access to the object. If there is an explicit deny set on the object, Amazon S3 does not authorize the request.
-
Object context – The requester must have permissions from the object owner to perform a specific object operation. In this step, Amazon S3 evaluates the object ACL.
Note
If bucket and object owners are the same, access to the object can be granted in the bucket policy, which is evaluated at the bucket context. If the owners are different, the object owners must use an object ACL to grant permissions. If the Amazon Web Services account that owns the object is also the parent account to which the IAM principal belongs, it can configure object permissions in a user policy, which is evaluated at the user context. For more information about using these access policy alternatives, see Walkthroughs that use policies to manage access to your Amazon S3 resources.
If you as the bucket owner want to own all the objects in your bucket and use bucket policies or policies based on IAMto manage access to these objects, you can apply the bucket owner enforced setting for Object Ownership. With this setting, you as the bucket owner automatically own and have full control over every object in your bucket. Bucket and object ACLs can’t be edited and are no longer considered for access. For more information, see Controlling ownership of objects and disabling ACLs for your bucket.
The following is an illustration of the context-based evaluation for an object operation.
Example of an object operation request
In this example, IAM user Jill, whose parent Amazon Web Services account is 1111-1111-1111, sends an
object operation request (for example, GetObject) for an object owned
by Amazon Web Services account 3333-3333-3333 in a bucket owned by Amazon Web Services account 2222-2222-2222.
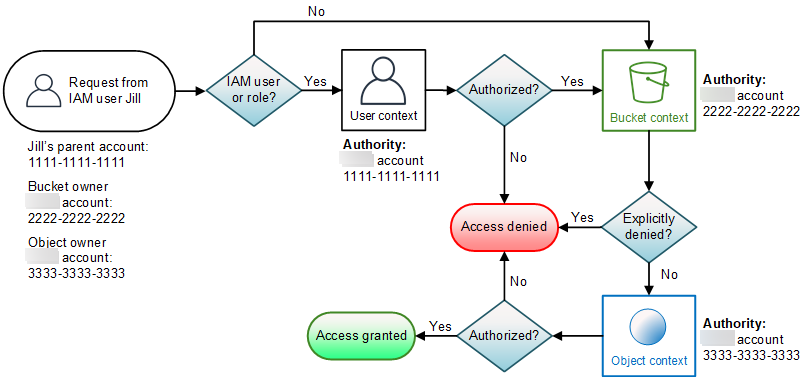
Jill will need permission from the parent Amazon Web Services account, the bucket owner, and the object owner. Amazon S3 evaluates the context as follows:
-
Because the request is from an IAM principal, Amazon S3 evaluates the user context to verify that the parent Amazon Web Services account 1111-1111-1111 has given Jill permission to perform the requested operation. If she has that permission, Amazon S3 evaluates the bucket context. Otherwise, Amazon S3 denies the request.
-
In the bucket context, the bucket owner, Amazon Web Services account 2222-2222-2222, is the context authority. Amazon S3 evaluates the bucket policy to determine if the bucket owner has explicitly denied Jill access to the object.
-
In the object context, the context authority is Amazon Web Services account 3333-3333-3333, the object owner. Amazon S3 evaluates the object ACL to determine if Jill has permission to access the object. If she does, Amazon S3 authorizes the request.