View last accessed information for Amazon Organizations
You can view service last accessed information for Amazon Organizations using the IAM console, Amazon CLI, or Amazon API. For important information about the data, permissions required, troubleshooting, and supported Regions, see Refine permissions in Amazon using last accessed information.
When you sign in to the IAM console using Amazon Organizations management account credentials, you can view information for any entity in your organization. Amazon Organizations entities include the organization root, organizational units (OUs), and accounts. You can also use the IAM console to view information for any service control policies (SCPs) in your organization. IAM shows a list of services that are allowed by any SCPs that apply to the entity. For each service, you can view the most recent account activity information for the chosen Amazon Organizations entity or the entity's children.
When you use the Amazon CLI or Amazon API with management account credentials, you can generate a report for any entities or policies in your organization. A programmatic report for an entity includes a list of services that are allowed by any SCPs that apply to the entity. For each service, the report includes the most recent activity for accounts in the specified Amazon Organizations entity or the entity's subtree.
When you generate a programmatic report for a policy, you must specify an Amazon Organizations entity. This report includes a list of services that are allowed by the specified SCP. For each service, it includes the most recent account activity in the entity or entity's children that are granted permission by that policy. For more information, see aws iam generate-organizations-access-report or GenerateOrganizationsAccessReport.
Before you view the report, make sure that you understand the management account requirements and information, reporting period, reported entities, and the evaluated policy types. For more details, see Things to know about last accessed information.
Understand the Amazon Organizations entity path
When you use the Amazon CLI or Amazon API to generate an Amazon Organizations access report, you must specify an entity path. A path is a text representation of the structure of an Amazon Organizations entity.
You can build an entity path using the known structure of your organization. For example, assume that you have the following organizational structure in Amazon Organizations.
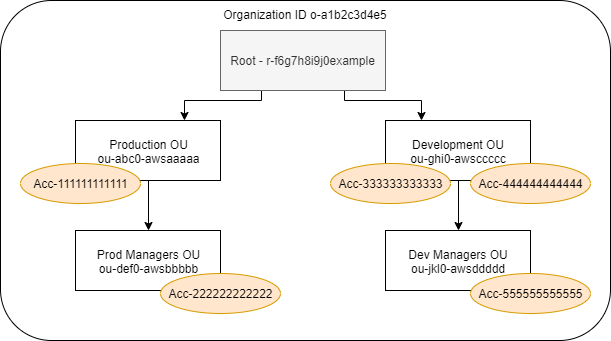
The path for the Dev Managers OU is built using the IDs of the organization, root, and all OUs in the path down to and including the OU.
o-a1b2c3d4e5/r-f6g7h8i9j0example/ou-ghi0-awsccccc/ou-jkl0-awsddddd/
The path for the account in the Production OU is built using the IDs of the organization, root, the OU, and the account number.
o-a1b2c3d4e5/r-f6g7h8i9j0example/ou-abc0-awsaaaaa/111111111111/
Note
Organization IDs are globally unique but OU IDs and root IDs are unique only within an organization. This means that no two organizations share the same organization ID. However, another organization might have an OU or root with the same ID as yours. We recommend that you always include the organization ID when you specify an OU or root.
Viewing information for Amazon Organizations (console)
You can use the IAM console to view service last accessed information for your root, OU, account, or policy.
To view information for the root (console)
-
Sign in to the Amazon Web Services Management Console using Amazon Organizations management account credentials, and open the IAM console at https://console.amazonaws.cn/iam/
. -
In the navigation pane below the Access reports section, choose Organization activity.
-
On the Organization activity page, choose Root.
-
On the Details and activity tab, view the Service access report section. The information includes a list of services that are allowed by the policies that are attached directly to the root. The information shows you from which account the service was last accessed and when. For more details about which principal accessed the service, sign in as an administrator in that account and view the IAM service last accessed information.
-
Choose the Attached SCPs tab to view the list of the service control policies (SCPs) that are attached to the root. IAM shows you the number of target entities to which each policy is attached. You can use this information to decide which SCP to review.
-
Choose the name of an SCP to view all of the services that the policy allows. For each service, view from which account the service was last accessed, and when.
-
Choose Edit in Amazon Organizations to view additional details and edit the SCP in the Amazon Organizations console. For more information, see Updating an SCP in the Amazon Organizations User Guide.
To view information for an OU or account (console)
-
Sign in to the Amazon Web Services Management Console using Amazon Organizations management account credentials, and open the IAM console at https://console.amazonaws.cn/iam/
. -
In the navigation pane below the Access reports section, choose Organization activity.
-
On the Organization activity page, expand the structure of your organization. Then choose the name of the OU or any account that you want to view except the management account.
-
On the Details and activity tab, view the Service access report section. The information includes a list of services that are allowed by the SCPs attached to the OU or account and all of its parents. The information shows you from which account the service was last accessed and when. For more details about which principal accessed the service, sign in as an administrator in that account and view the IAM service last accessed information.
-
Choose the Attached SCPs tab to view the list of the service control policies (SCPs) that are attached directly to the OU or account. IAM shows you the number of target entities to which each policy is attached. You can use this information to decide which SCP to review.
-
Choose the name of an SCP to view all of the services that the policy allows. For each service, view from which account the service was last accessed, and when.
-
Choose Edit in Amazon Organizations to view additional details and edit the SCP in the Amazon Organizations console. For more information, see Updating an SCP in the Amazon Organizations User Guide.
To view information for the management account (console)
-
Sign in to the Amazon Web Services Management Console using Amazon Organizations management account credentials, and open the IAM console at https://console.amazonaws.cn/iam/
. -
In the navigation pane below the Access reports section, choose Organization activity.
-
On the Organization activity page, expand the structure of your organization and choose the name your management account.
-
On the Details and activity tab, view the Service access report section. The information includes a list of all Amazon services. The management account is not limited by SCPs. The information shows you whether the account last accessed the service and when. For more details about which principal accessed the service, sign in as an administrator in that account and view the IAM service last accessed information.
-
Choose the Attached SCPs tab to confirm that there are no attached SCPs because the account is the management account.
To view information for a policy (console)
-
Sign in to the Amazon Web Services Management Console using Amazon Organizations management account credentials, and open the IAM console at https://console.amazonaws.cn/iam/
. -
In the navigation pane below the Access reports section, choose Service control policies (SCPs).
-
On the Service control policies (SCPs) page, view a list of the policies in your organization. You can view the number of target entities to which each policy is attached.
-
Choose the name of an SCP to view all of the services that the policy allows. For each service, view from which account the service was last accessed, and when.
-
Choose Edit in Amazon Organizations to view additional details and edit the SCP in the Amazon Organizations console. For more information, see Updating an SCP in the Amazon Organizations User Guide.
Viewing information for Amazon Organizations (Amazon CLI)
You can use the Amazon CLI to retrieve service last accessed information for your Amazon Organizations root, OU, account, or policy.
To view Amazon Organizations service last accessed information (Amazon CLI)
-
Use your Amazon Organizations management account credentials with the required IAM and Amazon Organizations permissions, and confirm that SCPs are enabled for your root. For more information, see Things to know about last accessed information.
-
Generate a report. The request must include the path of the Amazon Organizations entity (root, OU, or account) for which you want a report. You can optionally include an
organization-policy-idparameter to view a report for a specific policy. The command returns ajob-idthat you can then use in theget-organizations-access-reportcommand to monitor thejob-statusuntil the job is complete. -
Retrieve details about the report using the
job-idparameter from the previous step.This command returns a list of services that entity members can access. For each service, the command returns the date and time of an account member's last attempt and the entity path of the account. It also returns the total number of services that are available to access and the number of services that were not accessed. If you specified the optional
organizations-policy-idparameter, then the services that are available to access are those that are allowed by the specified policy.
Viewing information for Amazon Organizations (Amazon API)
You can use the Amazon API to retrieve service last accessed information for your Amazon Organizations root, OU, account, or policy.
To view Amazon Organizations service last accessed information (Amazon API)
-
Use your Amazon Organizations management account credentials with the required IAM and Amazon Organizations permissions, and confirm that SCPs are enabled for your root. For more information, see Things to know about last accessed information.
-
Generate a report. The request must include the path of the Amazon Organizations entity (root, OU, or account) for which you want a report. You can optionally include an
OrganizationsPolicyIdparameter to view a report for a specific policy. The operation returns aJobIdthat you can then use in theGetOrganizationsAccessReportoperation to monitor theJobStatusuntil the job is complete. -
Retrieve details about the report using the
JobIdparameter from the previous step.This operation returns a list of services that entity members can access. For each service, the operation returns the date and time of an account member's last attempt and the entity path of the account. It also returns the total number of services that are available to access, and the number of services that were not accessed. If you specified the optional
OrganizationsPolicyIdparameter, then the services that are available to access are those that are allowed by the specified policy.