Step 1: Set up your Amazon environment for Amazon Managed Microsoft AD Active Directory
Before you can create Amazon Managed Microsoft AD in your Amazon test lab, you first need to set up your Amazon EC2 key pair so that all login data is encrypted.
Create a key pair
If you already have a key pair, you can skip this step. For more information about Amazon EC2 key pairs, see Create key pairs.
To create a key pair
Sign in to the Amazon Web Services Management Console and open the Amazon EC2 console at https://console.amazonaws.cn/ec2/
. -
In the navigation pane, under Network & Security, choose Key Pairs, and then choose Create Key Pair.
-
For Key pair name, type
Amazon-DS-KP. For Key pair file format, select pem, and then choose Create. -
The private key file is automatically downloaded by your browser. The file name is the name you specified when you created your key pair with an extension of
.pem. Save the private key file in a safe place.Important
This is the only chance for you to save the private key file. You need to provide the name of your key pair when you launch an instance and the corresponding private key each time you decrypt the password for the instance.
Create, configure, and peer two Amazon VPCs
As shown in the following illustration, by the time you finish this multi-step process
you will have created and configured two public VPCs, two public subnets per VPC, one
Internet Gateway per VPC, and one VPC Peering connection between the VPCs. We chose to use
public VPCs and subnets for the purpose of simplicity and cost. For production workloads, we
recommend that you use private VPCs. For more information about improving VPC Security, see
Security in
Amazon Virtual Private Cloud
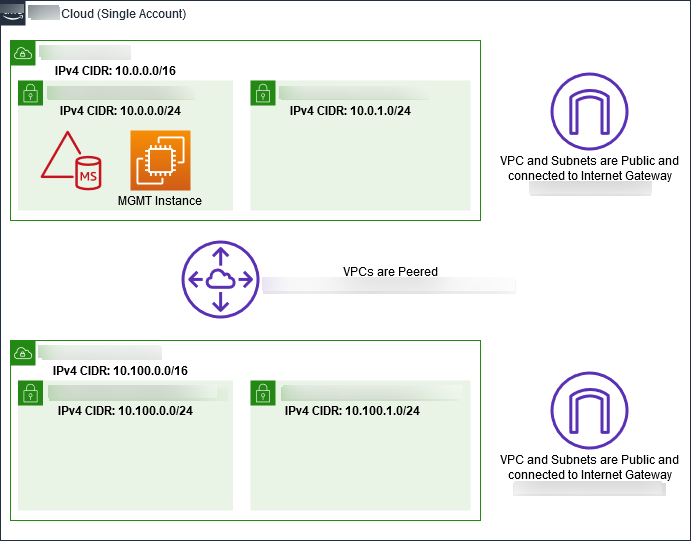
All of the Amazon CLI and PowerShell examples use the VPC information from below and are
built in us-west-2. You may choose any supported Region
Step 1: Create two VPCs
In this step, you need to create two VPCs in the same account using the specified parameters in the following table. Amazon Managed Microsoft AD supports the use of separate accounts with the Share your Amazon Managed Microsoft AD feature. The first VPC will be used for Amazon Managed Microsoft AD. The second VPC will be used for resources that can be used later in Tutorial: Creating a trust from Amazon Managed Microsoft AD to a self-managed Active Directory installation on Amazon EC2.
|
Managed Active Directory VPC information |
On-premises VPC information |
|---|---|
|
Name tag: Amazon-DS-VPC01 IPv4 CIDR block: 10.0.0.0/16 IPv6 CIDR block: No IPv6 CIDR Block Tenancy: Default |
Name tag: Amazon-OnPrem-VPC01 IPv4 CIDR block: 10.100.0.0/16 IPv6 CIDR block: No IPv6 CIDR Block Tenancy: Default |
For detailed instructions, see Creating a VPC
Step 2: Create two subnets per VPC
After you have created the VPCs you will need to create two subnets per VPC using the specified parameters in the following table. For this test lab each subnet will be a /24. This will allows up to 256 addresses to be issued per subnet. Each subnet must be a in a separate AZ. Putting each subnet in a separate in AZ is one of the Prerequisites for creating a Amazon Managed Microsoft AD.
|
Amazon-DS-VPC01 subnet Information: |
Amazon-OnPrem-VPC01 subnet information |
|---|---|
|
Name tag: Amazon-DS-VPC01-Subnet01 VPC: vpc-xxxxxxxxxxxxxxxxx Amazon-DS-VPC01 Availability Zone: us-west-2a IPv4 CIDR block: 10.0.0.0/24 |
Name tag: Amazon-OnPrem-VPC01-Subnet01 VPC: vpc-xxxxxxxxxxxxxxxxx Amazon-OnPrem-VPC01 Availability Zone: us-west-2a IPv4 CIDR block: 10.100.0.0/24 |
|
Name tag: Amazon-DS-VPC01-Subnet02 VPC: vpc-xxxxxxxxxxxxxxxxx Amazon-DS-VPC01 Availability Zone: us-west-2b IPv4 CIDR block: 10.0.1.0/24 |
Name tag: Amazon-OnPrem-VPC01-Subnet02 VPC: vpc-xxxxxxxxxxxxxxxxx Amazon-OnPrem-VPC01 Availability Zone: us-west-2b IPv4 CIDR block: 10.100.1.0/24 |
For detailed instructions, see Creating a subnet in your VPC
Step 3: Create and attach an Internet Gateway to your VPCs
Since we are using public VPCs you will need to create and attach an Internet gateway to your VPCs using the specified parameters in the following table. This will allow you to be able to connect to and manage your EC2 instances.
|
Amazon-DS-VPC01 Internet Gateway information |
Amazon-OnPrem-VPC01 Internet Gateway information |
|---|---|
|
Name tag: Amazon-DS-VPC01-IGW VPC: vpc-xxxxxxxxxxxxxxxxx Amazon-DS-VPC01 |
Name tag: Amazon-OnPrem-VPC01-IGW VPC: vpc-xxxxxxxxxxxxxxxxx Amazon-OnPrem-VPC01 |
For detailed instructions, see Internet
gateways
Step 4: Configure a VPC peering connection between Amazon-DS-VPC01 and Amazon-OnPrem-VPC01
Since you already created two VPCs earlier, you will need to network them together using
VPC peering using the specified parameters in the following table. While there are many ways
to connect your VPCs, this tutorial will use VPC Peering. Amazon Managed Microsoft AD supports many
solutions to connect your VPCs, some of these include VPC
peering
|
Peering connection name tag: Amazon-DS-VPC01&Amazon-OnPrem-VPC01-Peer VPC (Requester): vpc-xxxxxxxxxxxxxxxxx Amazon-DS-VPC01 Account: My Account Region: This Region VPC (Accepter): vpc-xxxxxxxxxxxxxxxxx Amazon-OnPrem-VPC01 |
For instructions on how to create a VPC Peering Connection with another VPC from with in
your account, see Creating a VPC peering connection with another VPC in your account
Step 5: Add two routes to each VPC's main route table
In order for the Internet Gateways and VPC Peering Connection created in the previous steps to be functional you will need to update the main route table of both VPCs using the specified parameters in the following table. You will be adding two routes; 0.0.0.0/0 which will route to all destinations not explicitly known to the route table and 10.0.0.0/16 or 10.100.0.0/16 which will route to each VPC over the VPC Peering Connection established above.
You can easily find the correct route table for each VPC by filtering on the VPC name tag (Amazon-DS-VPC01 or Amazon-OnPrem-VPC01).
|
Amazon-DS-VPC01 route 1 information |
Amazon-DS-VPC01 route 2 information |
Amazon-OnPrem-VPC01 route 1 Information |
Amazon-OnPrem-VPC01 route 2 Information |
|---|---|---|---|
|
Destination: 0.0.0.0/0 Target: igw-xxxxxxxxxxxxxxxxx Amazon-DS-VPC01-IGW |
Destination: 10.100.0.0/16 Target: pcx-xxxxxxxxxxxxxxxxx Amazon-DS-VPC01&Amazon-OnPrem-VPC01-Peer |
Destination: 0.0.0.0/0 Target: igw-xxxxxxxxxxxxxxxxx Amazon-Onprem-VPC01 |
Destination: 10.0.0.0/16 Target: pcx-xxxxxxxxxxxxxxxxx Amazon-DS-VPC01&Amazon-OnPrem-VPC01-Peer |
For instructions on how to add routes to a VPC route table, see Adding and removing routes from a route table
Create security groups for Amazon EC2 instances
By default, Amazon Managed Microsoft AD creates a security group to manage traffic between its domain controllers. In this section, you will need to create 2 security groups (one for each VPC) which will be used to manage traffic within your VPC for your EC2 instances using the specified parameters in the following tables. You also add a rule that allows RDP (3389) inbound from anywhere and for all traffic types inbound from the local VPC. For more information, see Amazon EC2 security groups for Windows instances.
|
Amazon-DS-VPC01 security group information: |
|---|
|
Security group name: Amazon DS Test Lab Security Group Description: Amazon DS Test Lab Security Group VPC: vpc-xxxxxxxxxxxxxxxxx Amazon-DS-VPC01 |
Security Group Inbound Rules for Amazon-DS-VPC01
| Type | Protocol | Port range | Source | Type of traffic |
|---|---|---|---|---|
| Custom TCP Rule | TCP | 3389 | My IP | Remote Desktop |
| All Traffic | All | All | 10.0.0.0/16 | All local VPC traffic |
Security Group Outbound Rules for Amazon-DS-VPC01
| Type | Protocol | Port range | Destination | Type of traffic |
|---|---|---|---|---|
| All Traffic | All | All | 0.0.0.0/0 | All traffic |
| Amazon-OnPrem-VPC01 security group information: |
|---|
|
Security group name: Amazon OnPrem Test Lab Security Group. Description: Amazon OnPrem Test Lab Security Group. VPC: vpc-xxxxxxxxxxxxxxxxx Amazon-OnPrem-VPC01 |
Security Group Inbound Rules for Amazon-OnPrem-VPC01
| Type | Protocol | Port range | Source | Type of traffic |
|---|---|---|---|---|
| Custom TCP Rule | TCP | 3389 | My IP | Remote Desktop |
| Custom TCP Rule | TCP | 53 | 10.0.0.0/16 | DNS |
| Custom TCP Rule | TCP | 88 | 10.0.0.0/16 | Kerberos |
| Custom TCP Rule | TCP | 389 | 10.0.0.0/16 | LDAP |
| Custom TCP Rule | TCP | 464 | 10.0.0.0/16 | Kerberos change / set password |
| Custom TCP Rule | TCP | 445 | 10.0.0.0/16 | SMB / CIFS |
| Custom TCP Rule | TCP | 135 | 10.0.0.0/16 | Replication |
| Custom TCP Rule | TCP | 636 | 10.0.0.0/16 | LDAP SSL |
| Custom TCP Rule | TCP | 49152 - 65535 | 10.0.0.0/16 | RPC |
| Custom TCP Rule | TCP | 3268 - 3269 | 10.0.0.0/16 | LDAP GC & LDAP GC SSL |
| Custom UDP Rule | UDP | 53 | 10.0.0.0/16 | DNS |
| Custom UDP Rule | UDP | 88 | 10.0.0.0/16 | Kerberos |
| Custom UDP Rule | UDP | 123 | 10.0.0.0/16 | Windows Time |
| Custom UDP Rule | UDP | 389 | 10.0.0.0/16 | LDAP |
| Custom UDP Rule | UDP | 464 | 10.0.0.0/16 | Kerberos change / set password |
| All Traffic | All | All | 10.100.0.0/16 | All local VPC traffic |
Security Group Outbound Rules for Amazon-OnPrem-VPC01
| Type | Protocol | Port range | Destination | Type of traffic |
|---|---|---|---|---|
| All Traffic | All | All | 0.0.0.0/0 | All traffic |
For detailed instructions on how to create and add rules to your security groups, see
Working with security groups