Sharing Amazon DocumentDB cluster snapshots
Using Amazon DocumentDB, you can share a manual cluster snapshot in the following ways:
Sharing a manual cluster snapshot, whether encrypted or unencrypted, enables authorized Amazon accounts to copy the snapshot.
Sharing a manual cluster snapshot, whether encrypted or unencrypted, enables authorized Amazon accounts to directly restore a cluster from the snapshot instead of taking a copy of it and restoring from that.
Note
To share an automated cluster snapshot, create a manual cluster snapshot by copying the automated snapshot, and then share that copy. This process also applies to Amazon Backup–generated resources.
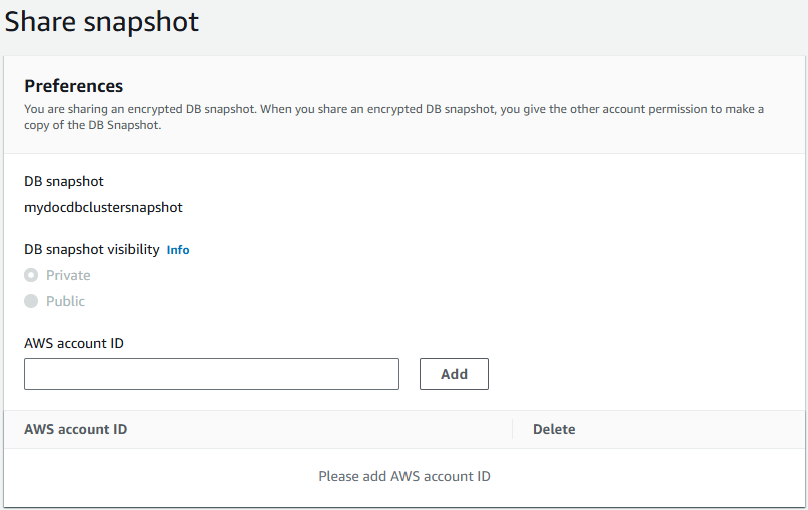
You can share a manual snapshot with up to 20 other Amazon Web Services accounts. You can also share an unencrypted manual snapshot as public, which makes the snapshot available to all accounts. When sharing a snapshot as public, ensure that none of your private information is included in any of your public snapshots.
When sharing manual snapshots with other Amazon Web Services accounts, and you restore a cluster from a shared snapshot using the Amazon CLI or the Amazon DocumentDB API, you must specify the Amazon Resource Name (ARN) of the shared snapshot as the snapshot identifier.
Sharing an encrypted snapshot
The following restrictions apply to sharing encrypted snapshots:
-
You can't share encrypted snapshots as public.
-
You can't share a snapshot that has been encrypted using the default Amazon KMS encryption key of the account that shared the snapshot.
Follow these steps to share encrypted snapshots.
-
Share the Amazon Key Management Service (Amazon KMS) encryption key that was used to encrypt the snapshot with any accounts that you want to be able to access the snapshot.
You can share Amazon KMS encryption keys with another Amazon accounts by adding the other accounts to the Amazon KMS key policy. For details on updating a key policy, see Using Key Policies in Amazon KMS in the Amazon Key Management Service Developer Guide. For an example of creating a key policy, see Creating an IAM policy to enable copying of the encrypted snapshot later in this topic.
-
Use the Amazon CLI, as shown below, to share the encrypted snapshot with the other accounts.
Allowing access to an Amazon KMS encryption key
For another Amazon Web Services account to copy an encrypted snapshot shared
from your account, the account that you share your snapshot with
must have access to the Amazon KMS key that encrypted the snapshot. To
allow another account access to an Amazon KMS key, update the key
policy for the Amazon KMS key with the ARN of the account that you are
sharing to as a principal in the Amazon KMS key policy. Then allow the
kms:CreateGrant action.
After you give an account access to your Amazon KMS encryption key, to copy your encrypted snapshot, that account must create an Amazon Identity and Access Management (IAM) user if it doesn’t already have one. In addition, that account must also attach an IAM policy to that IAM user that allows the user to copy an encrypted snapshot using your Amazon KMS key. The account must be an IAM user and cannot be a root Amazon Web Services account identity due to Amazon KMS security restrictions.
In the following key policy example, user 123451234512 is the
owner of the Amazon KMS encryption key. User 123456789012 is the
account that the key is being shared with. This updated key
policy gives the account access to the Amazon KMS key. It does this by
including the ARN for the root Amazon Web Services account identity for user
123456789012 as a principal for the policy, and by allowing the
kms:CreateGrant action.
Creating an IAM policy to enable copying of the encrypted snapshot
When the external Amazon Web Services account has access to your Amazon KMS key, the owner of that account can create a policy to allow an IAM user that is created for the account to copy an encrypted snapshot that is encrypted with that Amazon KMS key.
The following example shows a policy that can be attached to
an IAM user for Amazon Web Services account 123456789012. The policy enables
the IAM user to copy a shared snapshot from account
123451234512 that has been encrypted with the Amazon KMS key
c989c1dd-a3f2-4a5d-8d96-e793d082ab26 in the
us-west-2 Region.
For details on updating a key policy, see Using Key Policies in Amazon KMS in the Amazon Key Management Service Developer Guide.
Sharing a snapshot
You can share an Amazon DocumentDB manual cluster snapshot (or a copy of an automated snapshot) using the Amazon Web Services Management Console or the Amazon CLI: