Configure IAM runtime roles for Amazon EMR cluster access in Studio
When you connect to an Amazon EMR cluster from your Studio or Studio Classic notebooks, you can visually browse a list of IAM roles, known as runtime roles, and select one on the fly. Subsequently, all your Apache Spark, Apache Hive, or Presto jobs created from your notebook access only the data and resources permitted by policies attached to the runtime role. Also, when data is accessed from data lakes managed with Amazon Lake Formation, you can enforce table-level and column-level access using policies attached to the runtime role.
With this capability, you and your teammates can connect to the same cluster, each using a runtime role scoped with permissions matching your individual level of access to data. Your sessions are also isolated from one another on the shared cluster.
To try out this feature using Studio Classic, see Apply fine-grained data access controls with Amazon Lake Formation and Amazon EMR from Amazon SageMaker Studio Classic
Prerequisites
Before you get started, make sure you meet the following prerequisites:
-
Use Amazon EMR version 6.9 or above.
-
For Studio Classic users: Use JupyterLab version 3 in the Studio Classic Jupyter server application configuration. This version supports Studio Classic connection to Amazon EMR clusters using runtime roles.
For Studio users: Use a SageMaker distribution image version
1.10or above. -
Allow the use of runtime roles in your cluster's security configuration. For more information, see Runtime roles for Amazon EMR steps.
-
Create a notebook with any of the kernels listed in Supported images and kernels to connect to an Amazon EMR cluster from Studio or Studio Classic.
-
Make sure you review the instructions in Set up Studio to use runtime IAM roles to configure your runtime roles.
Cross-account connection scenarios
Runtime role authentication supports a variety of cross-account connection scenarios when your data resides outside of your Studio account. The following image shows three different ways you can assign your Amazon EMR cluster, data, and even Amazon EMR runtime execution role between your Studio and data accounts:
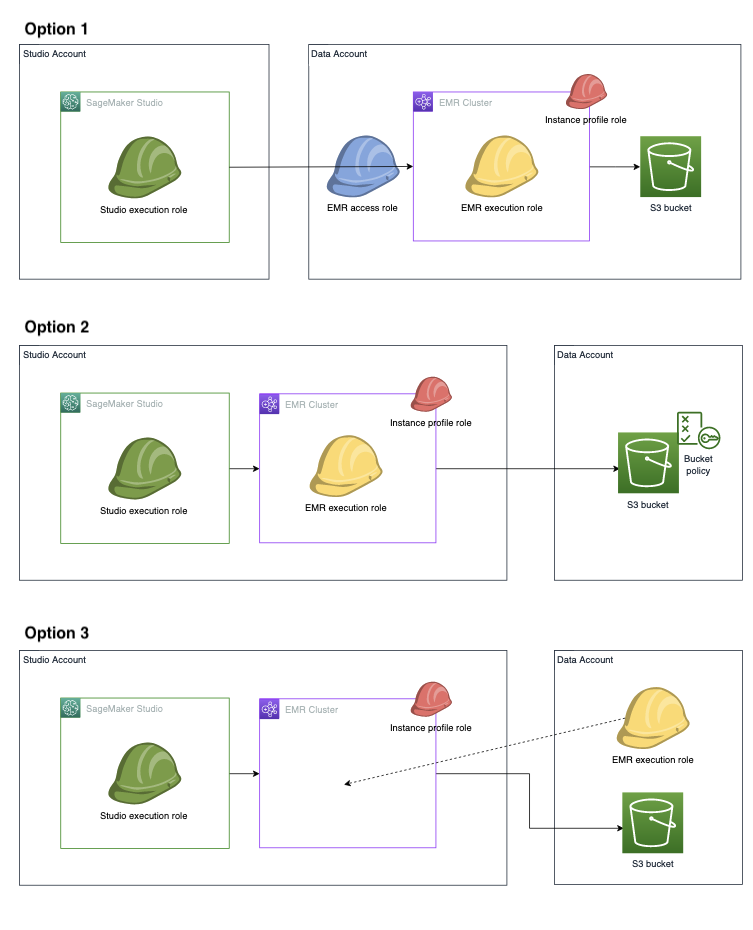
In option 1, your Amazon EMR cluster and Amazon EMR runtime execution role are in a separate data
account from the Studio account. You define a separate Amazon EMR access role (also referred
to as Assumable role) permission policy which grants permission to Studio or
Studio Classic execution role to assume the Amazon EMR access role. The Amazon EMR access role then calls
the Amazon EMR API GetClusterSessionCredentials on behalf of your Studio or
Studio Classic execution role, giving you access to the cluster.
In option 2, your Amazon EMR cluster and Amazon EMR runtime execution role are in your Studio
account. Your Studio execution role has permission to use the Amazon EMR API
GetClusterSessionCredentials to gain access to your cluster. To access the Amazon S3
bucket, give the Amazon EMR runtime execution role cross-account Amazon S3 bucket access permissions
— you grant these permissions within your Amazon S3 bucket policy.
In option 3, your Amazon EMR clusters are in your Studio account, and the Amazon EMR runtime
execution role is in the data account. Your Studio or Studio Classic execution role has
permission to use the Amazon EMR API GetClusterSessionCredentials to gain access to
your cluster. Add the Amazon EMR runtime execution role into the execution role configuration JSON.
Then you can select the role in the UI when you choose your cluster. For details about how to
set up your execution role configuration JSON file, see Preload your execution roles into
Studio or Studio Classic.
Set up Studio to use runtime IAM roles
To establish runtime role authentication for your Amazon EMR clusters, configure the required IAM policies, network, and usability enhancements. Your setup depends on whether you handle any cross-account arrangements if your Amazon EMR clusters, Amazon EMR runtime execution role, or both, reside outside of your Studio account. The following section guides you through the policies to install, how to configure the network to allow traffic between cross-accounts, and the local configuration file to set up to automate your Amazon EMR connection.
Configure runtime role authentication when your Amazon EMR cluster and Studio are in the same account
If your Amazon EMR cluster resides in your Studio account, complete the following steps to add necessary permissions to your Studio execution policy:
-
Add the required IAM policy to connect to Amazon EMR clusters. For details, see Configure listing Amazon EMR clusters.
-
Grant permission to call the Amazon EMR API
GetClusterSessionCredentialswhen you pass one or more permitted Amazon EMR runtime execution roles specified in the policy. -
(Optional) Grant permission to pass IAM roles that follow any user-defined naming conventions.
-
(Optional) Grant permission to access Amazon EMR clusters that are tagged with specific user-defined strings.
-
Preload your IAM roles so you can select the role to use when you connect to your Amazon EMR cluster. For details about how to preload your IAM roles, see Preload your execution roles into Studio or Studio Classic.
The following example policy permits Amazon EMR runtime execution roles belonging to the
modeling and training groups to call GetClusterSessionCredentials. In addition,
the policyholder can access Amazon EMR clusters tagged with the strings modeling or
training.
Configure runtime role authentication when your cluster and Studio are in different accounts
If your Amazon EMR cluster is not in your Studio account, allow your SageMaker AI execution role to assume the cross-account Amazon EMR access role so you can connect to the cluster. Complete the following steps to set up your cross-account configuration:
-
Create your SageMaker AI execution role permission policy so that the execution role can assume the Amazon EMR access role. The following policy is an example:
-
Create the trust policy to specify which Studio account IDs are trusted to assume the Amazon EMR access role. The following policy is an example:
-
Create the Amazon EMR access role permission policy, which grants the Amazon EMR runtime execution role the needed permissions to carry out the intended tasks on the cluster. Configure the Amazon EMR access role to call the API
GetClusterSessionCredentialswith the Amazon EMR runtime execution roles specified in the access role permission policy. The following policy is an example: -
Set up the cross-account network so that traffic can move back and forth between your accounts. For guided instruction, see Configure network access for your Amazon EMR clusterSet up the . The steps in this section help you complete the following tasks:
-
VPC-peer your Studio account and your Amazon EMR account to establish a connection.
-
Manually add routes to the private subnet route tables in both accounts. This permits creation and connection of Amazon EMR clusters from the Studio account to the remote account's private subnet.
-
Set up the security group attached to your Studio domain to allow outbound traffic and the security group of the Amazon EMR primary node to allow inbound TCP traffic from the Studio instance security group.
-
-
Preload your IAM runtime roles so you can select the role to use when you connect to your Amazon EMR cluster. For details about how to preload your IAM roles, see Preload your execution roles into Studio or Studio Classic.
Configure Lake Formation access
When you access data from data lakes managed by Amazon Lake Formation, you can enforce table-level and column-level access using policies attached to your runtime role. To configure permission for Lake Formation access, see Integrate Amazon EMR with Amazon Lake Formation.
Preload your execution roles into Studio or Studio Classic
You can preload your IAM runtime roles so you can select the role to use when you connect to your Amazon EMR cluster. Users of JupyterLab in Studio can use the SageMaker AI console or the provided script.