Connectivity
You must establish connectivity between Amazon cloud where your RISE with SAP solution is running and on-premises data centers. You also need a connection for direct data transfer (to avoid routing data via your on-premises locations) and communication between SAP systems and your applications running on Amazon cloud. The following image provides an example overview of connectivity to RISE with SAP VPC.
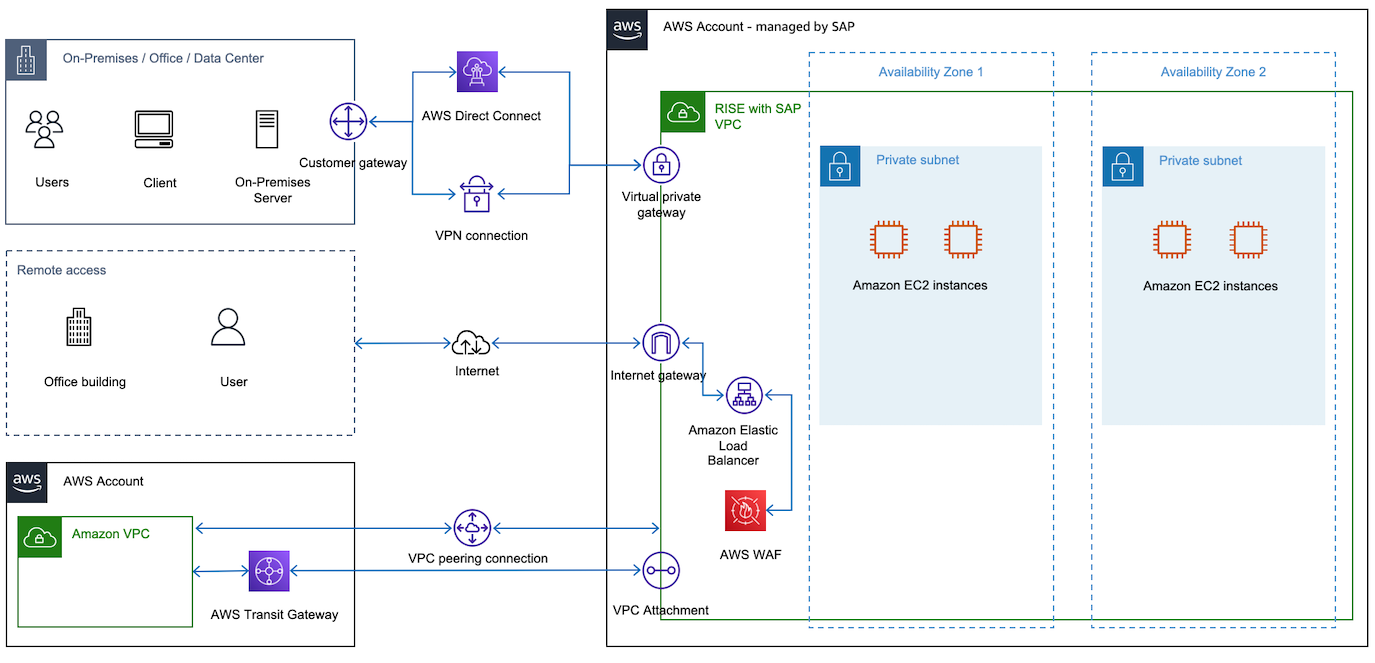
See the following topics for further details: