Technical Requirements
Before creating an SAP instance, ensure that the following technical requirements are met.
Amazon VPC Network Topologies
You need to deploy SAP systems that receive information from the Amazon Data Provider for SAP within an Amazon Virtual Private Cloud
-
The first topology configures routes and traffic directly to the Amazon Cloud through a NAT gateway within an Amazon VPC. For more information about internet gateways, see the Amazon documentation.
Connection to the Amazon Cloud via an internet gateway
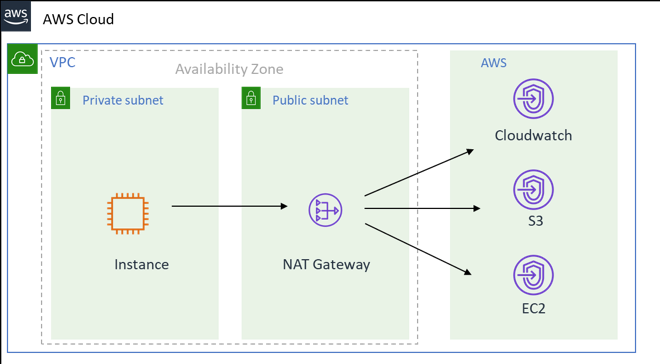
-
A second topology routes traffic from the Amazon VPC, through your organization’s on-premises data center, and back to Amazon Cloud. For more information about this topology, see the What is Amazon Site-to-Site VPN?
Connection to the Amazon Web Services Cloud via an on-premises data center
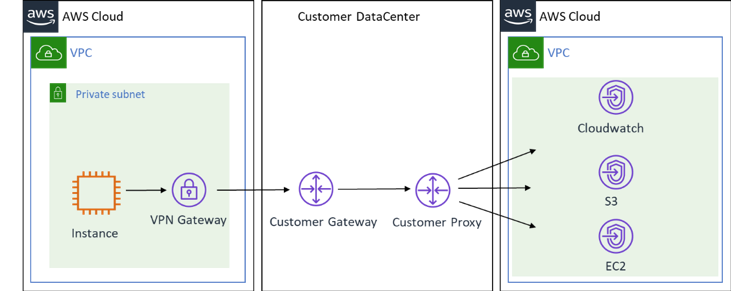
Amazon VPC Endpoints
Create endpoints for the following services that the DataProvider uses:
-
Monitoring
-
Amazon EC2
To create data endpoints in the Amazon console, use the following procedure for each of the two endpoints:
-
Sign in to the Amazon VPC console
, navigate to Endpoints, and select Create Endpoint. -
On the next screen, search for the service name, then select the appropriate VPC and route table, and select Create Endpoint.
-
After creating all three endpoints you should see them in your list of endpoints as shown below:
IAM Roles
You need to grant the Amazon Data Provider for SAP read-only access to the Amazon CloudWatch, Amazon Simple Storage Service (Amazon S3), and Amazon EC2 services so that you can use their APIs. You can do this by creating an Amazon Identity and Access Management (IAM) role for your Amazon EC2 instance and attaching a permissions policy.
Use the following procedure to create an IAM role and grant permissions to your Amazon EC2 instance:
-
Sign in to the Amazon Management Console
and open the IAM console . -
In the navigation pane, select Roles, and select Create role.
-
Choose the Amazon service role type, and select EC2.
-
Select EC2 as the use case, and select Next Permissions.
-
Select Create Policy, and select JSON.
-
Copy and paste the following policy into the input field, replace all existing text, and select Review Policy.
Note
If your Amazon EC2 instances are running in Beijing and Ningxia, you must update the Resource line with the correct region.
See the following example policies based on your Amazon Region.
Amazon Regions (except Amazon GovCloud (US-East), Amazon GovCloud (US-West), Beijing and Ningxia)
{ "Version":"2012-10-17", "Statement": [ { "Sid": "VisualEditor0", "Effect": "Allow", "Action": [ "EC2:DescribeInstances", "cloudwatch:GetMetricStatistics", "EC2:DescribeVolumes" ], "Resource": "*" }, { "Sid": "VisualEditor1", "Effect": "Allow", "Action": "s3:GetObject", "Resource": [ "arn:aws:s3:::aws-sap-dataprovider-us-east-1/config.properties" ] } ] }Beijing and Ningxia
{ "Version":"2012-10-17", "Statement": [ { "Sid": "VisualEditor0", "Effect": "Allow", "Action": [ "EC2:DescribeInstances", "cloudwatch:GetMetricStatistics", "EC2:DescribeVolumes" ], "Resource": "*" }, { "Sid": "VisualEditor1", "Effect": "Allow", "Action": "s3:GetObject", "Resource": [ "arn:aws-cn:s3:::aws-sap-dataprovider-cn-north-1/config.properties" ] } ] }Amazon GovCloud (US-East) and Amazon GovCloud (US-West)
{ "Version":"2012-10-17", "Statement": [ { "Sid": "VisualEditor0", "Effect": "Allow", "Action": [ "EC2:DescribeInstances", "cloudwatch:GetMetricStatistics", "EC2:DescribeVolumes" ], "Resource": "*" }, { "Sid": "VisualEditor1", "Effect": "Allow", "Action": "s3:GetObject", "Resource": [ "arn:aws-us-gov:s3:::aws-sap-dataprovider-us-gov-west-1/config.properties" ] } ] } -
Provide a Name and Description for the role, and select Create Policy.
-
Select Create Policy. The IAM console confirms the new policy with a message similar to the following.
-
Navigate to the Create Role page, refresh the screen, search for the newly created role, and select the policy.
-
Select Next:Tags.
-
Add any tags if needed, otherwise select Next:Review.
-
Provide a name for the Role and select Create Role.