Performance
Enhance SAP Fiori performance with Amazon CloudFront
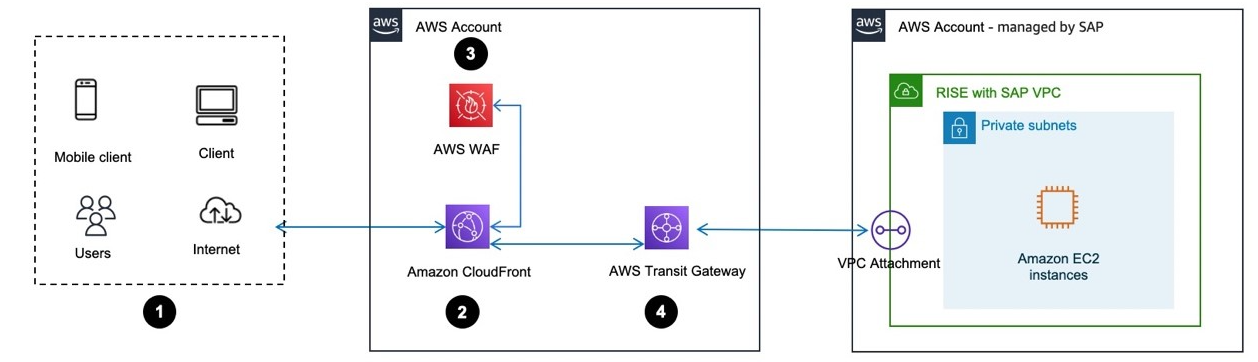
Amazon CloudFront is a Content Delivery Network service to increase performance and reduce latency of SAP Fiori launchpad in RISE with SAP. CloudFront creates a cache for the static content and accelerates dynamic content through edge computing.
Global SAP systems accessed by users from across multiple geographical regions, can use Amazon CloudFront VPC (Virtual Private Cloud) Origins to reduce network latency and improve the SAP end-user experience.
CloudFront VPC Origins is a feature that enhances security and streamlines operations for web applications such as SAP Fiori, hosted in private subnets within the Amazon VPC. This architecture allows CloudFront to serve as the single entry point for SAP Fiori, eliminating the need for public exposure of the SAP servers.
CloudFront VPC Origins is deployed in the customer-managed Amazon account, directing SAP users coming through the CloudFront to an internal, Amazon Application Load Balancer (ALB). The ALB routes Fiori traffic directly to the SAP systems hosted in the SAP RISE Amazon account through the Amazon Transit Gateway. The Amazon Web Application Firewall (WAF) is optional but recommended to improve security posture.
Data flow
-
User accesses SAP Fiori launchpad via Internet browser or mobile device
-
The request is routed to Amazon CloudFront to the closest edge compute of the user location
-
Optionally, Amazon Web Application Firewall (WAF) evaluates the request based on the customer’s configured rules to block malicious traffic. Additionally, Distributed Denial of Service (DDOS) protection
is also provided by Amazon Shield Standard which is automatically included at no extra cost when you use CloudFront with Amazon WAF -
The request is then parsed to the Amazon ALB which forwards the traffic to the SAP system hosted in the SAP managed RISE account.
This improves the security posture of SAP systems by:
-
Eliminating direct exposure of SAP servers to the public internet
-
Reducing the attack surface as CloudFront becomes the only ingress point
-
Simplified security management with centralized control through CloudFront
-
Easy integration with Amazon WAF & Amazon Shield Standard for additional protection
Integrating CloudFront VPC Origins with SAP can lead to performance improvements:
-
Global users benefit from CloudFront’s worldwide edge locations
-
Traffic is optimized using the Amazon global network backbone
. CloudFront traffic stays on the high-throughput Amazon global network backbone all the way to your SAP servers, providing optimized performance and low latency -
Static SAP Fiori content is cached at CloudFront edge locations and dynamic SAP Fiori content is accelerated through CloudFront’s global edge network
To implement CloudFront VPC Origins for SAP:
-
The applications in RISE with SAP are by default hosted in private VPC subnets, in an Amazon account – managed by SAP
-
In the Amazon account – managed by customer, create an Amazon ALB pointing to the SAP system in the RISE account
-
Create a CloudFront distribution with VPC Origins pointing to the Amazon ALB
-
Update the security group for your VPC private origin (Amazon ALB in this case) to explicitly allow the CloudFront managed prefix list. This restricts traffic coming to the VPC origin
-
Ensure the same fully qualified domain name is used by CloudFront, ALB, and SAP
-
Configure CloudFront to handle both static and dynamic content from SAP systems
-
Optionally, implement Amazon WAF for additional security at the edge
Refer to Amazon documentation Restrict access with VPC origins for more information.
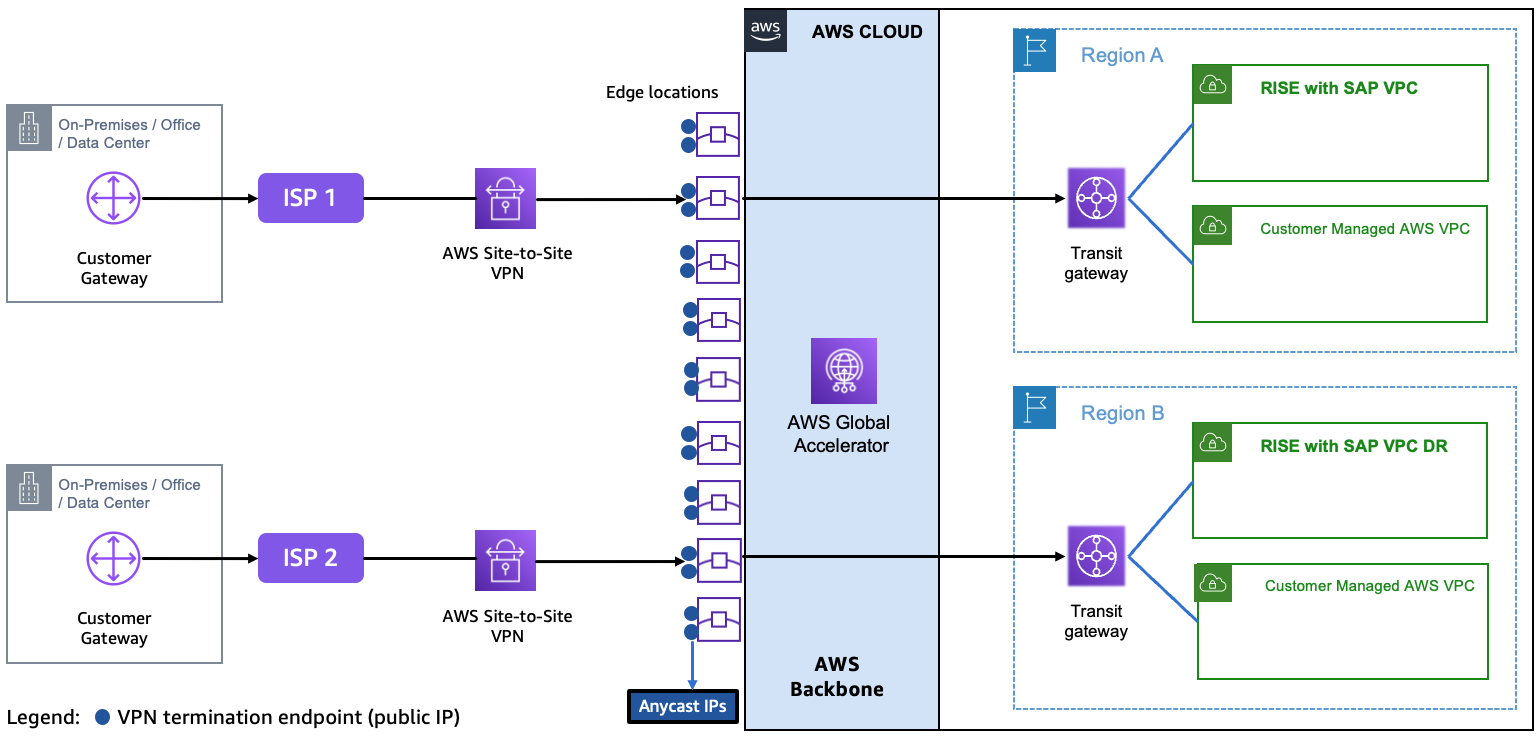
Optimize performance with Accelerated Site-to-Site VPN connections
When you deploy RISE with SAP on Amazon for a global roll-out, you can reduce the network latency by leveraging Amazon Global Accelerator
Amazon Global Accelerator
Accelerated Site-to-Site VPN connections combines traditional Amazon Site-to-Site VPN with Amazon Global Accelerator to optimize traffic routing. It routes the traffic from on-premises network to an Amazon edge location that is closest to customer gateway device, leveraging the Amazon backbone. This will reduce latency by up to ~30%-60% compared to standard VPNs.
Enhancing observability of RISE with SAP using Amazon Internet Monitor
Amazon Internet Monitor continuously analyses internet traffic between end users and Amazon-hosted applications, detecting network anomalies that may impact RISE with SAP performance. It provides insights into issues like increased latency, packet loss, or regional connectivity disruptions, allowing organizations to proactively address potential outages before they affect SAP workloads.
RISE with SAP relies on stable and predictable network performance, Amazon Internet Monitor helps by:
-
Identifying ISP or regional network disruptions that impact SAP response times.
-
Providing early warnings and actionable recommendations to mitigate network-related service degradation.
-
Distinguishing between Amazon infrastructure issues and external internet disruptions and streamlining troubleshooting.
-
Improving observability of Internet routing, which is dynamic and lacks predictable service-level agreements (SLAs).
-
Proactive management of external ISPs and transit providers which may introduce unpredictable latency, packet loss, and congestion issues.
To implement you can refer to the Getting started with Internet Monitor.