AWSSupport-TroubleshootS3EventNotifications
Description
The AWSSupport-TroubleshootS3EventNotifications Amazon Systems Manager automation runbook
helps troubleshoot Amazon Simple Storage Service (Amazon S3) Bucket Event Notifications configured with Amazon Lambda
Functions, Amazon Simple Notification Service (Amazon SNS) Topics, or Amazon Simple Queue Service (Amazon SQS) Queues. It provides a
configuration settings report of the different resources configured with the the Amazon S3 Bucket
as a destination event notification.
How does it work?
The runbook performs the following steps:
-
Checks if the Amazon S3 Bucket exists in the same account where
AWSSupport-TroubleshootS3EventNotificationsis executed. -
Fetches the destination resources (Amazon Lambda Function, or Amazon SNS Topic or Amazon SQS queue) configured as Event Notifications for the Amazon S3 Bucket using the GetBucketNotificationConfiguration API.
-
Validates that the destination resource exists, then reviews the resource-based policy of the destination resources to determine if Amazon S3 is allowed to publish to the destination.
-
If you encrypted the destination with an Amazon Key Management Service (Amazon KMS) key, the key policy is checked to determine if Amazon S3 access is allowed.
-
Generates a report of all the destination resource checks.
Important
-
This runbook can only evaluate event notification configurations if the Amazon S3 bucket owner is the same as the Amazon Web Services account owner where the automation runbook is being executed.
-
Additionally, this runbook cannot evaluate policies on destination resources that are hosted in another Amazon Web Services account.
Document type
Automation
Owner
Amazon
Platforms
Linux, macOS, Windows
Parameters
-
AutomationAssumeRole
Type: String
Description: (Optional) The Amazon Resource Name (ARN) of the Amazon Identity and Access Management (IAM) role that allows Systems Manager Automation to perform the actions on your behalf. If no role is specified, Systems Manager Automation uses the permissions of the user that starts this runbook.
-
S3BucketName
Type:
AWS::S3::Bucket::NameDescription: (Required) The name of the Amazon S3 bucket configured with event notification(s).
Required IAM permissions
The AutomationAssumeRole parameter requires the following actions to
use the runbook successfully.
-
s3:GetBucketLocation -
s3:ListAllMyBuckets -
s3:GetBucketNotification -
sqs:GetQueueAttributes -
sqs:GetQueueUrl -
sns:GetTopicAttributes -
kms:GetKeyPolicy -
kms:DescribeKey -
kms:ListAliases -
lambda:GetPolicy -
lambda:GetFunction -
iam:GetContextKeysForCustomPolicy -
iam:SimulateCustomPolicy -
iam:ListRoles -
ssm:DescribeAutomationStepExecutions
Example IAM Policy for the Automation Assume Role
Instructions
Follow these steps to configure the automation:
-
Navigate to
AWSSupport-TroubleshootS3EventNotificationsin Systems Manager under Documents. -
Select Execute automation.
-
For the input parameters, enter the following:
-
AutomationAssumeRole (Optional):
The Amazon Resource Name (ARN) of the Amazon Amazon Identity and Access Management (IAM) role that allows Systems Manager Automation to perform the actions on your behalf. If no role is specified, Systems Manager Automation uses the permissions of the user who starts this runbook.
-
S3BucketName (Required):
The name of the Amazon S3 bucket configured with event notification(s).
-
-
Select Execute.
-
The automation initiates.
-
The document performs the following steps:
-
ValidateInputs
Validates Amazon S3 bucket provided belongs to the same account where the automation is executed and fetch the region the bucket is hosted.
-
GetBucketNotificationConfiguration
Calls
GetBucketNotificationConfigurationAPI to review Event Notifications configured with the Amazon S3 bucket and formats output. -
BranchOnSQSResourcePolicy
Branches on whether there are Amazon SQS resources in event notifications.
-
ValidateSQSResourcePolicy
Validates resource policy on Amazon SQS Queue attributes has
sqs:SendMessagepermission for Amazon S3. If the Amazon SQS resource is encrypted, checks that encryption is not using default Amazon KMS key i.e.aws/sqsand checks that Amazon KMS key policy has permissions for Amazon S3. -
BranchOnSNSResourcePolicy
Branches on whether there are Amazon SNS resources in event notifications.
-
ValidateSNSResourcePolicy
Validates resource policy on Amazon SNS Topic attributes has
sns:Publishpermission for Amazon S3. If the Amazon SNS resource is encrypted, checks that encryption is not using default Amazon KMS key i.e.aws/snsand checks that Amazon KMS key policy has permissions for Amazon S3. -
BranchOnLambdaFunctionResourcePolicy
Branches on whether there are Amazon Lambda functions in event notifications.
-
ValidateLambdaFunctionResourcePolicy
Validates resource policy on Amazon Lambda function has
lambda:InvokeFunctionpermission for Amazon S3. -
GenerateReport
Returns details of the runbook steps outputs, and recommendations to resolve any issue with the event notifications configured with the Amazon S3 bucket.
-
-
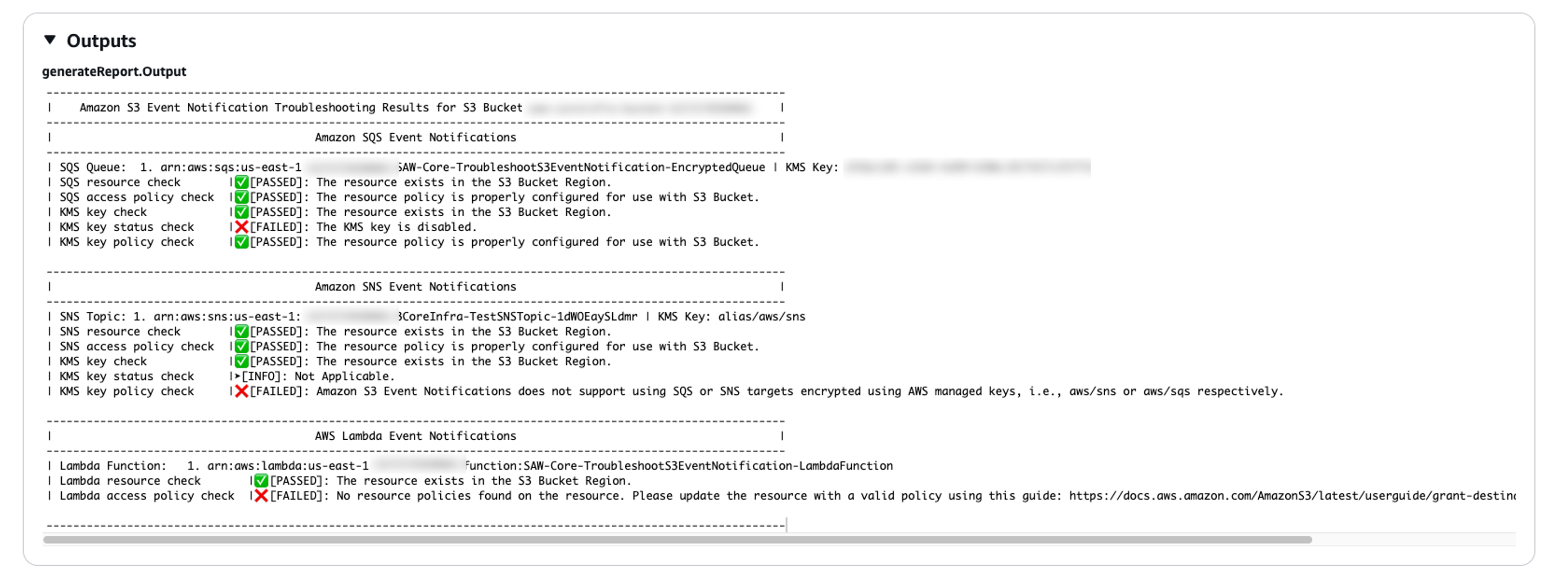
After completed, review the Outputs section for the detailed results of the execution:
-
Amazon SQS Event Notifications
If there are Amazon SQS destination notifications configured with the Amazon S3 bucket, a list of the Amazon SQS Queues is displayed alongside the results of the checks. The report includes Amazon SQS resource check, Amazon SQS access policy check, Amazon KMS key check, Amazon KMS key status check, and Amazon KMS key policy check.
-
Amazon SNS Event Notifications
If there are Amazon SNS destination notifications configured with the Amazon S3 bucket, a list of the Amazon SNS Topics is displayed alongside the results of the checks. The report includes Amazon SNS resource check, Amazon SNS access policy check, Amazon KMS key check, Amazon KMS key status check, and Amazon KMS key policy check.
-
Amazon Lambda Event Notifications
If there are Amazon Lambda destination notifications configured with the Amazon S3 bucket, a list of the Lambda functions is displayed alongside the results of the checks. The report includes Lambda resource check and Lambda access policy check.
-
References
Systems Manager Automation