Introducing a new console experience for Amazon WAF
You can now use the updated experience to access Amazon WAF functionality anywhere in the console. For more details, see Working with the console.
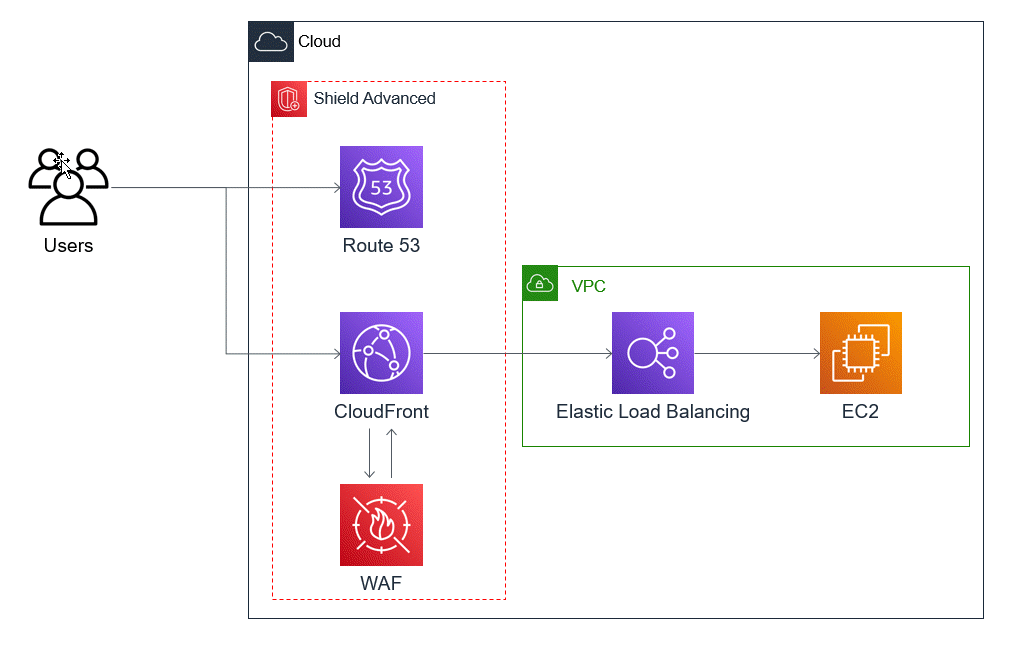
Example Shield Advanced DDoS resiliency architecture for common web applications
This page provides an example architecture for maximizing resiliency against DDoS attacks with Amazon web applications.
You can build a web application in any Amazon Region and receive automatic DDoS protection from the detection and mitigation capabilities that Amazon provides in the Region.
This example is for architectures that route users to a web application using resources like Classic Load Balancers, Application Load Balancers, Network Load Balancers, Amazon Marketplace solutions, or your own proxy layer. You can improve DDoS resiliency by inserting Amazon Route 53 hosted zones, Amazon CloudFront distributions, and Amazon WAF web ACLs between these web application resources and your users. These insertions can obfuscate the application origin, serve requests closer to your end users, and detect and mitigate application layer request floods. Applications that serve static or dynamic content to your users with CloudFront and Route 53 are protected by an integrated, fully inline DDoS mitigation system that mitigates infrastructure layer attacks in real time.
With these architectural improvements in place, you can then protect your Route 53 hosted zones and your CloudFront distributions with Shield Advanced. When you protect CloudFront distributions, Shield Advanced prompts you to associate Amazon WAF web ACLs and create rate-based rules for them, and gives you the option of enabling automatic application layer DDoS mitigation or proactive engagement. Proactive engagement and automatic application layer DDoS mitigation use Route 53 health checks that you associate with the resource. To learn more about these options, see Resource protections in Amazon Shield Advanced.
The following reference diagram depicts this DDoS resilient architecture for a web application.
The benefits that this approach provides to your web application include the following:
-
Protection against frequently used infrastructure layer (layer 3 and layer 4) DDoS attacks, without detection delay. In addition, if a resource is frequently targeted, Shield Advanced places mitigations for longer periods of time. Shield Advanced also uses application context inferred from Network ACLs (NACLs) to block unwanted traffic further upstream. This isolates failures closer to their source, minimizing the effect on legitimate users.
-
Protection against TCP SYN floods. The DDoS mitigation systems that are integrated with CloudFront, Route 53, and Amazon Global Accelerator provide a TCP SYN proxy capability that challenges new connection attempts and only serves legitimate users.
-
Protection against DNS application layer attacks, because Route 53 is responsible for serving authoritative DNS responses.
-
Protection against web application layer request floods. The rate-based rule that you configure in your Amazon WAF web ACL blocks source IPs when they are sending more requests than the rule allows.
-
Automatic application layer DDoS mitigation for your CloudFront distributions, if you choose to enable this option. With automatic DDoS mitigation, Shield Advanced maintains a rate-based rule in the distribution's associated Amazon WAF web ACL that limits the volume of requests from known DDoS sources. Additionally, when Shield Advanced detects an event that affects the health of your application, it automatically creates, tests, and manages mitigating rules in web ACL.
-
Proactive engagement with the Shield Response Team (SRT), if you choose to enable this option. When Shield Advanced detects an event that affects the health of your application, the SRT responds and proactively engages with your security or operations teams using the contact information that you provide. The SRT analyzes patterns in your traffic and can update your Amazon WAF rules to block the attack.