What is Amazon Cognito?
Amazon Cognito is an identity platform for web and mobile apps. It’s a user directory, an authentication server, and an authorization service for OAuth 2.0 access tokens and Amazon credentials. With Amazon Cognito, you can authenticate and authorize users from the built-in user directory, from your enterprise directory, and from consumer identity providers like Google and Facebook.
Topics
The two components that follow make up Amazon Cognito. They operate independently or in tandem, based on your access needs for your users.
User pools
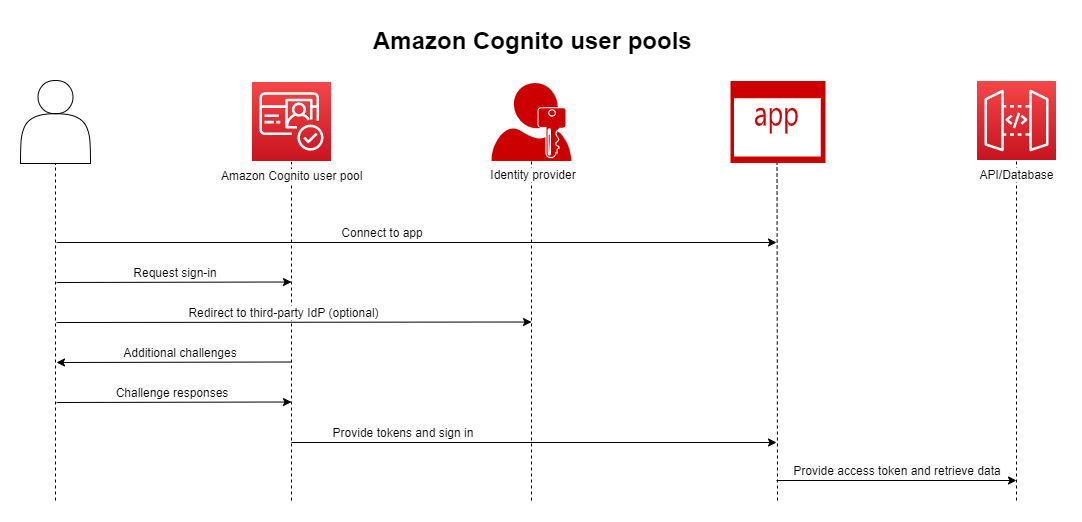
Create a user pool when you want to authenticate and authorize users to your app or API.
User pools are a user directory with both self-service and administrator-driven user creation,
management, and authentication. Your user pool can be an independent directory and OIDC
identity provider (IdP), and an intermediate service provider (SP) to third-party providers of
workforce and customer identities. You can provide single sign-on (SSO) in your app for your
organization's workforce identities in SAML 2.0 and OIDC IdPs with user pools. You can also
provide SSO in your app for your organization's customer identities in the public OAuth 2.0
identity stores Amazon, Google, Apple and Facebook. For more information about customer
identity and access management (CIAM), see What is CIAM?
User pools don’t require integration with an identity pool. From a user pool, you can issue authenticated JSON web tokens (JWTs) directly to an app, a web server, or an API.
Identity pools

Set up an Amazon Cognito identity pool when you want to authorize authenticated or anonymous users to access your Amazon resources. An identity pool issues Amazon credentials for your app to serve resources to users. You can authenticate users with a trusted identity provider, like a user pool or a SAML 2.0 service. It can also optionally issue credentials for guest users. Identity pools use both role-based and attribute-based access control to manage your users’ authorization to access your Amazon resources.
Identity pools don’t require integration with a user pool. An identity pool can accept authenticated claims directly from both workforce and consumer identity providers.
An Amazon Cognito user pool and identity pool used together
In the diagram that begins this topic, you use Amazon Cognito to authenticate your user and then grant them access to an Amazon Web Services service.
-
Your app user signs in through a user pool and receives OAuth 2.0 tokens.
-
Your app exchanges a user pool token with an identity pool for temporary Amazon credentials that you can use with Amazon APIs and the Amazon Command Line Interface (Amazon CLI).
-
Your app assigns the credentials session to your user, and delivers authorized access to Amazon Web Services services like Amazon S3 and Amazon DynamoDB.
For more examples that use identity pools and user pools, see Common Amazon Cognito scenarios
In Amazon Cognito, the security of the cloud obligation of the
shared
responsibility model
Features of Amazon Cognito
User pools
An Amazon Cognito user pool is a user directory. With a user pool, your users can sign in to your web or mobile app through Amazon Cognito, or federate through a third-party IdP. Federated and local users have a user profile in your user pool.
Local users are those who signed up or you created directly in your user pool. You can manage and customize these user profiles in the Amazon Web Services Management Console, an Amazon SDK, or the Amazon Command Line Interface (Amazon CLI).
Amazon Cognito user pools accept tokens and assertions from third-party IdPs, and collect the user attributes into a JWT that it issues to your app. You can standardize your app on one set of JWTs while Amazon Cognito handles the interactions with IdPs, mapping their claims to a central token format.
An Amazon Cognito user pool can be a standalone IdP. Amazon Cognito draws from the OpenID Connect (OIDC) standard to generate JWTs for authentication and authorization. When you sign in local users, your user pool is authoritative for those users. You have access to the following features when you authenticate local users.
-
Implement your own web front-end that calls the Amazon Cognito user pools API to authenticate, authorize, and manage your users.
-
Set up multi-factor authentication (MFA) for your users. Amazon Cognito supports time-based one-time password (TOTP) and SMS message MFA.
-
Secure against access from user accounts that are under malicious control.
-
Create your own custom multi-step authentication flows.
-
Look up users in another directory and migrate them to Amazon Cognito.
An Amazon Cognito user pool can also fulfill a dual role as a service provider (SP) to your IdPs, and an IdP to your app. Amazon Cognito user pools can connect to consumer IdPs like Facebook and Google, or workforce IdPs like Okta and Active Directory Federation Services (ADFS).
With the OAuth 2.0 and OpenID Connect (OIDC) tokens that an Amazon Cognito user pool issues, you can
-
Accept an ID token in your app that authenticates a user, and provides the information that you need to set up the user’s profile
-
Accept an access token in your API with the OIDC scopes that authorize your users’ API calls.
-
Retrieve Amazon credentials from an Amazon Cognito identity pool.
| Feature | Description |
|---|---|
| OIDC identity provider | Issue ID tokens to authenticate users |
| Authorization server | Issue access tokens to authorize user access to APIs |
| SAML 2.0 service provider | Transform SAML assertions into ID and access tokens |
| OIDC relying party | Transform OIDC tokens into ID and access tokens |
| Social provider relying party | Transform ID tokens from Apple, Facebook, Amazon, or Google to your own ID and access tokens |
| Authentication frontend service | Sign up, manage, and authenticate users with managed login |
| API support for your own UI | Create, manage and authenticate users through authentication API requests in supported Amazon SDKs¹ |
| Multi-factor authentication | Use SMS messages, TOTPs, or your user's device as an additional authentication factor¹ |
| Security monitoring & response | Secure against malicious activity and insecure passwords¹ |
| Customize authentication flows | Build your own authentication mechanism, or add custom steps to existing flows² |
| Groups | Create logical groupings of users, and a hierarchy of IAM role claims when you pass tokens to identity pools |
| Customize tokens | Customize your ID and access tokens with new, modified, and suppressed claims |
| Customize user attributes | Assign values to user attributes and add your own custom attributes |
¹ Feature is unavailable to federated users.
² Feature is unavailable to federated and managed login users.
For more information about user pools, see Getting started with user pools and the Amazon Cognito user pools API reference.
Identity pools
An identity pool is a collection of unique identifiers, or identities, that you assign to your users or guests and authorize to receive temporary Amazon credentials. When you present proof of authentication to an identity pool in the form of the trusted claims from a SAML 2.0, OpenID Connect (OIDC), or OAuth 2.0 social identity provider (IdP), you associate your user with an identity in the identity pool. The token that your identity pool creates for the identity can retrieve temporary session credentials from Amazon Security Token Service (Amazon STS).
To complement authenticated identities, you can also configure an identity pool to authorize Amazon access without IdP authentication. You can offer custom proof of authentication with Developer-authenticated identities. You can also grant temporary Amazon credentials to guest users, with unauthenticated identities.
With identity pools, you have two ways to integrate with IAM policies in your Amazon Web Services account. You can use these two features together or individually.
Role-based access control
When your user passes claims to your identity pool, Amazon Cognito chooses the IAM role that it requests. To customize the role’s permissions to your needs, you apply IAM policies to each role. For example, if your user demonstrates that they are in the marketing department, they receive credentials for a role with policies tailored to marketing department access needs. Amazon Cognito can request a default role, a role based on rules that query your user’s claims, or a role based on your user’s group membership in a user pool. You can also configure the role trust policy so that IAM trusts only your identity pool to generate temporary sessions.
Attributes for access control
Your identity pool reads attributes from your user’s claims, and maps them to
principal tags in your user’s temporary session. You can then configure your IAM
resource-based policies to allow or deny access to resources based on IAM principals
that carry the session tags from your identity pool. For example, if your user
demonstrates that they are in the marketing department, Amazon STS tags their session
Department: marketing. Your Amazon S3 bucket permits read operations based on an
aws:PrincipalTag condition that requires a value of
marketing for the Department tag.
| Feature | Description |
|---|---|
| Amazon Cognito user pool relying party | Exchange an ID token from your user pool for web identity credentials from Amazon STS |
| SAML 2.0 service provider | Exchange SAML assertions for web identity credentials from Amazon STS |
| OIDC relying party | Exchange OIDC tokens for web identity credentials from Amazon STS |
| Social provider relying party | Exchange OAuth tokens from Amazon, Facebook, Google, Apple, and Twitter for web identity credentials from Amazon STS |
| Custom relying party | With Amazon credentials, exchange claims in any format for web identity credentials from Amazon STS |
| Unauthenticated access | Issue limited-access web identity credentials from Amazon STS without authentication |
| Role-based access control | Choose an IAM role for your authenticated user based on their claims, and configure your roles to only be assumed in the context of your identity pool |
| Attribute-based access control | Convert claims into principal tags for your Amazon STS temporary session, and use IAM policies to filter resource access based on principal tags |
For more information about identity pools, see Getting started with Amazon Cognito identity pools and the Amazon Cognito identity pools API reference.
Amazon Cognito user pools and identity pools comparison
| Feature | Description | User pools | Identity pools |
|---|---|---|---|
| OIDC identity provider | Issue OIDC ID tokens to authenticate app users | ✓ | |
| User directory | Store user profiles for authentication | ✓ | |
| Authorize API access | Issue access tokens to authorize user access to APIs (including user profile self-service API operations), databases, and other resources that accept OAuth scopes | ✓ | |
| IAM web identity authorization | Generate tokens that you can exchange with Amazon STS for temporary Amazon credentials | ✓ | |
| SAML 2.0 service provider & OIDC identity provider | Issue customized OIDC tokens based on claims from a SAML 2.0 identity provider | ✓ | |
| OIDC relying party & OIDC identity provider | Issue customized OIDC tokens based on claims from an OIDC identity provider | ✓ | |
| OAuth 2.0 relying party & OIDC identity provider | Issue customized OIDC tokens based on scopes from OAuth 2.0 social providers like Apple and Google | ✓ | |
| SAML 2.0 service provider & credentials broker | Issue temporary Amazon credentials based on claims from a SAML 2.0 identity provider | ✓ | |
| OIDC relying party & credentials broker | Issue temporary Amazon credentials based on claims from an OIDC identity provider | ✓ | |
| Social provider relying party & credentials broker | Issue temporary Amazon credentials based on JSON web tokens from developer applications with social providers like Apple and Google | ✓ | |
| Amazon Cognito user pool relying party & credentials broker | Issue temporary Amazon credentials based on JSON web tokens from Amazon Cognito user pools | ✓ | |
| Custom relying party & credentials broker | Issue temporary Amazon credentials to arbitrary identities, authorized by developer IAM credentials | ✓ | |
| Authentication frontend service | Sign up, manage, and authenticate users with managed login | ✓ | |
| API support for your own authentication UI | Create, manage and authenticate users through API requests in supported Amazon SDKs¹ | ✓ | |
| MFA | Use SMS messages, TOTPs, or your user's device as an additional authentication factor¹ | ✓ | |
| Security monitoring & response | Protect against malicious activity and insecure passwords¹ | ✓ | |
| Customize authentication flows | Build your own authentication mechanism, or add custom steps to existing flows¹ | ✓ | |
| User groups | Create logical groupings of users, and a hierarchy of IAM role claims when you pass tokens to identity pools | ✓ | |
| Customize tokens | Customize your ID and access tokens with new, modified, and suppressed claims and scopes | ✓ | |
| Amazon WAF web ACLs | Monitor and control requests to your authentication front end with Amazon WAF | ✓ | |
| Customize user attributes | Assign values to user attributes and add your own custom attributes | ✓ | |
| Unauthenticated access | Issue limited-access web identity credentials from Amazon STS without authentication | ✓ | |
| Role-based access control | Choose an IAM role for your authenticated user based on their claims, and configure your role trust to limit access to web identity users | ✓ | |
| Attribute-based access control | Transform user claims into principal tags for your Amazon STS temporary session, and use IAM policies to filter resource access based on principal tags | ✓ |
¹ Feature is not available to federated users.
Getting started with Amazon Cognito
For example user pool applications, see Getting started with user pools.
For an introduction to identity pools, see Getting started with Amazon Cognito identity pools.
For links to guided setup experiences with user pools and identity pools, see Guided setup options for Amazon Cognito.
To get started with an Amazon SDK, see Amazon Developer Tools
To use Amazon Cognito, you need an Amazon Web Services account. For more information, see Getting started with Amazon.
Regional availability
Amazon Cognito is available in multiple Amazon Regions worldwide. In each Region, Amazon Cognito is distributed across multiple Availability Zones. These Availability Zones are physically isolated from each other, but are united by private, low-latency, high-throughput, and highly redundant network connections. These Availability Zones enable Amazon to provide services, including Amazon Cognito, with very high levels of availability and redundancy, while also minimizing latency.
To see if Amazon Cognito is currently available in any Amazon Web Services Region, see Amazon Services by
Region
To learn about regional API service endpoints, see Amazon regions and endpoints in the Amazon Web Services General Reference.
To learn more about the number of Availability Zones that are available in each Region,
see Amazon global
infrastructure
Pricing for Amazon Cognito
For information about Amazon Cognito pricing, see Amazon Cognito pricing