Associating an IAM role with an Amazon Aurora MySQL DB cluster
To permit database users in an Amazon Aurora DB cluster to access other Amazon services, you associate the IAM role that you created in Creating an IAM role to allow Amazon Aurora to access Amazon services with that DB cluster. You can also have Amazon create a new IAM role by associating the service directly.
Note
You can't associate an IAM role with an Aurora Serverless v1 DB cluster. For more information, see Using Amazon Aurora Serverless v1.
You can associate an IAM role with an Aurora Serverless v2 DB cluster.
To associate an IAM role with a DB cluster you do two things:
-
Add the role to the list of associated roles for a DB cluster by using the RDS console, the add-role-to-db-cluster Amazon CLI command, or the AddRoleToDBCluster RDS API operation.
You can add a maximum of five IAM roles for each Aurora DB cluster.
-
Set the cluster-level parameter for the related Amazon service to the ARN for the associated IAM role.
The following table describes the cluster-level parameter names for the IAM roles used to access other Amazon services.
Cluster-level parameter Description aws_default_lambda_roleUsed when invoking a Lambda function from your DB cluster.
aws_default_logs_roleThis parameter is no longer required for exporting log data from your DB cluster to Amazon CloudWatch Logs. Aurora MySQL now uses a service-linked role for the required permissions. For more information about service-linked roles, see Using service-linked roles for Amazon Aurora.
aws_default_s3_roleUsed when invoking the
LOAD DATA FROM S3,LOAD XML FROM S3, orSELECT INTO OUTFILE S3statement from your DB cluster.In Aurora MySQL version 2, the IAM role specified in this parameter is used if an IAM role isn't specified for
aurora_load_from_s3_roleoraurora_select_into_s3_rolefor the appropriate statement.In Aurora MySQL version 3, the IAM role specified for this parameter is always used.
aurora_load_from_s3_roleUsed when invoking the
LOAD DATA FROM S3orLOAD XML FROM S3statement from your DB cluster. If an IAM role is not specified for this parameter, the IAM role specified inaws_default_s3_roleis used.In Aurora MySQL version 3, this parameter isn't available.
aurora_select_into_s3_roleUsed when invoking the
SELECT INTO OUTFILE S3statement from your DB cluster. If an IAM role is not specified for this parameter, the IAM role specified inaws_default_s3_roleis used.In Aurora MySQL version 3, this parameter isn't available.
To associate an IAM role to permit your Amazon RDS cluster to communicate with other Amazon services on your behalf, take the following steps.
To associate an IAM role with an Aurora DB cluster using the console
-
Open the RDS console at https://console.amazonaws.cn/rds/
. -
Choose Databases.
-
Choose the name of the Aurora DB cluster that you want to associate an IAM role with to show its details.
-
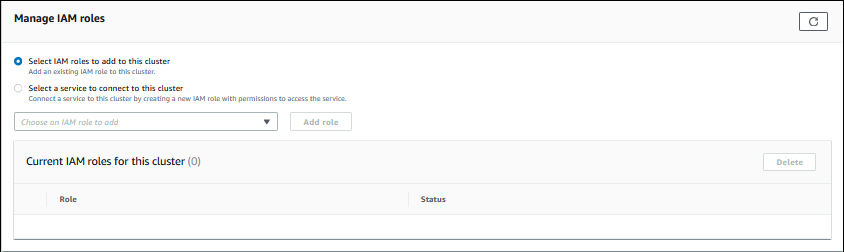
On the Connectivity & security tab, in the Manage IAM roles section, do one of the following:
-
Select IAM roles to add to this cluster (default)
-
Select a service to connect to this cluster
-
-
To use an existing IAM role, choose it from the menu, then choose Add role.
If adding the role is successful, its status shows as
Pending, thenAvailable. -
To connect a service directly:
-
Choose Select a service to connect to this cluster.
-
Choose the service from the menu, then choose Connect service.
-
For Connect cluster to
Service Name, enter the Amazon Resource Name (ARN) to use to connect to the service, then choose Connect service.
Amazon creates a new IAM role for connecting to the service. Its status shows as
Pending, thenAvailable. -
-
(Optional) To stop associating an IAM role with a DB cluster and remove the related permission, choose the role and then choose Delete.
To set the cluster-level parameter for the associated IAM role
-
In the RDS console, choose Parameter groups in the navigation pane.
-
If you are already using a custom DB parameter group, you can select that group to use instead of creating a new DB cluster parameter group. If you are using the default DB cluster parameter group, create a new DB cluster parameter group, as described in the following steps:
-
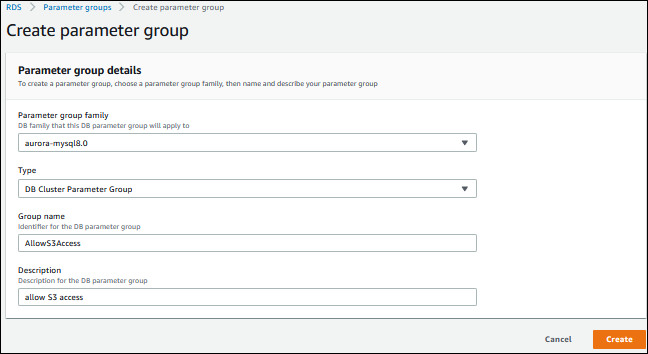
Choose Create parameter group.
-
For Parameter group family, choose
aurora-mysql8.0for an Aurora MySQL 8.0-compatible DB cluster, oraurora-mysql5.7for an Aurora MySQL 5.7-compatible DB cluster. -
For Type, choose DB Cluster Parameter Group.
-
For Group name, type the name of your new DB cluster parameter group.
-
For Description, type a description for your new DB cluster parameter group.
-
Choose Create.
-
-
On the Parameter groups page, select your DB cluster parameter group and choose Edit for Parameter group actions.
-
Set the appropriate cluster-level parameters to the related IAM role ARN values.
For example, you can set just the
aws_default_s3_roleparameter toarn:aws-cn:iam::123456789012:role/AllowS3Access. -
Choose Save changes.
-
To change the DB cluster parameter group for your DB cluster, complete the following steps:
-
Choose Databases, and then choose your Aurora DB cluster.
-
Choose Modify.
-
Scroll to Database options and set DB cluster parameter group to the DB cluster parameter group.
-
Choose Continue.
-
Verify your changes and then choose Apply immediately.
-
Choose Modify cluster.
-
Choose Databases, and then choose the primary instance for your DB cluster.
-
For Actions, choose Reboot.
When the instance has rebooted, your IAM role is associated with your DB cluster.
For more information about cluster parameter groups, see Aurora MySQL configuration parameters.
-
To associate an IAM role with a DB cluster by using the Amazon CLI
-
Call the
add-role-to-db-clustercommand from the Amazon CLI to add the ARNs for your IAM roles to the DB cluster, as shown following.PROMPT> aws rds add-role-to-db-cluster --db-cluster-identifier my-cluster --role-arn arn:aws-cn:iam::123456789012:role/AllowAuroraS3Role PROMPT> aws rds add-role-to-db-cluster --db-cluster-identifier my-cluster --role-arn arn:aws-cn:iam::123456789012:role/AllowAuroraLambdaRole -
If you are using the default DB cluster parameter group, create a new DB cluster parameter group. If you are already using a custom DB parameter group, you can use that group instead of creating a new DB cluster parameter group.
To create a new DB cluster parameter group, call the
create-db-cluster-parameter-groupcommand from the Amazon CLI, as shown following.PROMPT> aws rds create-db-cluster-parameter-group --db-cluster-parameter-group-name AllowAWSAccess \ --db-parameter-group-family aurora5.7 --description "Allow access to Amazon S3 and Amazon Lambda"For an Aurora MySQL 5.7-compatible DB cluster, specify
aurora-mysql5.7for--db-parameter-group-family. For an Aurora MySQL 8.0-compatible DB cluster, specifyaurora-mysql8.0for--db-parameter-group-family. -
Set the appropriate cluster-level parameter or parameters and the related IAM role ARN values in your DB cluster parameter group, as shown following.
PROMPT> aws rds modify-db-cluster-parameter-group --db-cluster-parameter-group-name AllowAWSAccess \ --parameters "ParameterName=aws_default_s3_role,ParameterValue=arn:aws-cn:iam::123456789012:role/AllowAuroraS3Role,method=pending-reboot" \ --parameters "ParameterName=aws_default_lambda_role,ParameterValue=arn:aws-cn:iam::123456789012:role/AllowAuroraLambdaRole,method=pending-reboot" -
Modify the DB cluster to use the new DB cluster parameter group and then reboot the cluster, as shown following.
PROMPT> aws rds modify-db-cluster --db-cluster-identifier my-cluster --db-cluster-parameter-group-name AllowAWSAccess PROMPT> aws rds reboot-db-instance --db-instance-identifier my-cluster-primaryWhen the instance has rebooted, your IAM roles are associated with your DB cluster.
For more information about cluster parameter groups, see Aurora MySQL configuration parameters.