Sharing a DB cluster snapshot
Using Amazon RDS, you can share a manual DB cluster snapshot in the following ways:
-
Sharing a manual DB cluster snapshot, whether encrypted or unencrypted, enables authorized Amazon accounts to copy the snapshot.
-
Sharing a manual DB cluster snapshot, whether encrypted or unencrypted, enables authorized Amazon accounts to directly restore a DB cluster from the snapshot instead of taking a copy of it and restoring from that.
Note
To share an automated DB cluster snapshot, create a manual DB cluster snapshot by copying the automated snapshot, and then share that copy. This process also applies to Amazon Backup–generated resources.
For more information on copying a snapshot, see DB cluster snapshot copying. For more information on restoring a DB instance from a DB cluster snapshot, see Restoring from a DB cluster snapshot.
For more information on restoring a DB cluster from a DB cluster snapshot, see Overview of backing up and restoring an Aurora DB cluster.
You can share a manual snapshot with up to 20 other Amazon Web Services accounts.
The following limitation applies when sharing manual snapshots with other Amazon Web Services accounts:
-
When you restore a DB cluster from a shared snapshot using the Amazon Command Line Interface (Amazon CLI) or Amazon RDS API, you must specify the Amazon Resource Name (ARN) of the shared snapshot as the snapshot identifier.
Learn to share snapshots, public snapshots, and encrypted snapshots in the following sections. You can also learn how to stop sharing snapshots.
Topics
Sharing a snapshot
You can share a DB cluster snapshot using the Amazon Web Services Management Console, the Amazon CLI, or the RDS API.
Using the Amazon RDS console, you can share a manual DB cluster snapshot with up to 20 Amazon Web Services accounts. You can also use the console to stop sharing a manual snapshot with one or more accounts.
To share a manual DB cluster snapshot by using the Amazon RDS console
-
Sign in to the Amazon Web Services Management Console and open the Amazon RDS console at https://console.amazonaws.cn/rds/
. -
In the navigation pane, choose Snapshots.
-
Select the manual snapshot that you want to share.
-
For Actions, choose Share snapshot.
-
Choose one of the following options for DB snapshot visibility.
If the source is unencrypted, choose Public to permit all Amazon Web Services accounts to restore a DB cluster from your manual DB cluster snapshot, or choose Private to permit only Amazon Web Services accounts that you specify to restore a DB cluster from your manual DB cluster snapshot.
Warning
If you set DB snapshot visibility to Public, all Amazon Web Services accounts can restore a DB cluster from your manual DB cluster snapshot and have access to your data. Do not share any manual DB cluster snapshots that contain private information as Public.
For more information, see Sharing public snapshots.
-
If the source is encrypted, DB snapshot visibility is set as Private because encrypted snapshots can't be shared as public.
Note
Snapshots that have been encrypted with the default Amazon KMS key can't be shared. For information on how to work around this issue, see Sharing encrypted snapshots.
-
For Amazon Account ID, enter the Amazon Web Services account identifier for an account that you want to permit to restore a DB cluster from your manual snapshot, and then choose Add. Repeat to include additional Amazon Web Services account identifiers, up to 20 Amazon Web Services accounts.
If you make an error when adding an Amazon Web Services account identifier to the list of permitted accounts, you can delete it from the list by choosing Delete at the right of the incorrect Amazon Web Services account identifier.
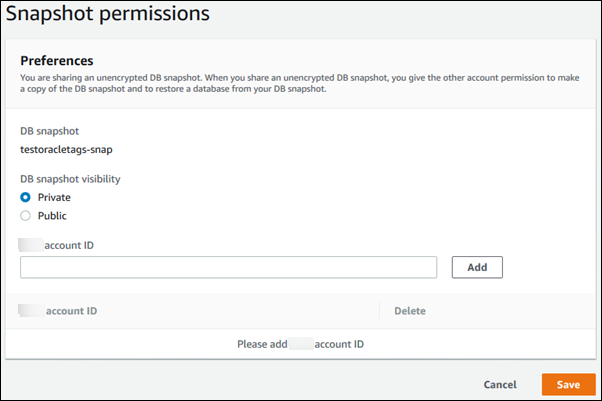
-
After you have added identifiers for all of the Amazon Web Services accounts that you want to permit to restore the manual snapshot, choose Save to save your changes.
To share a DB cluster snapshot, use the aws rds modify-db-cluster-snapshot-attribute
command. Use the --values-to-add parameter to add a list of the IDs for the Amazon Web Services accounts
that are authorized to restore the manual snapshot.
Example of sharing a snapshot with a single account
The following example enables Amazon Web Services account identifier 123456789012 to restore the DB cluster snapshot
named cluster-3-snapshot.
For Linux, macOS, or Unix:
aws rds modify-db-cluster-snapshot-attribute \ --db-cluster-snapshot-identifier cluster-3-snapshot \ --attribute-name restore \ --values-to-add 123456789012
For Windows:
aws rds modify-db-cluster-snapshot-attribute ^ --db-cluster-snapshot-identifier cluster-3-snapshot ^ --attribute-name restore ^ --values-to-add 123456789012
Example of sharing a snapshot with multiple accounts
The following example enables two Amazon Web Services account identifiers, 111122223333 and
444455556666, to restore the DB cluster snapshot named
manual-cluster-snapshot1.
For Linux, macOS, or Unix:
aws rds modify-db-cluster-snapshot-attribute \ --db-cluster-snapshot-identifier manual-cluster-snapshot1 \ --attribute-name restore \ --values-to-add {"111122223333","444455556666"}
For Windows:
aws rds modify-db-cluster-snapshot-attribute ^ --db-cluster-snapshot-identifier manual-cluster-snapshot1 ^ --attribute-name restore ^ --values-to-add "[\"111122223333\",\"444455556666\"]"
Note
When using the Windows command prompt, you must escape double quotes (") in JSON code by prefixing them with a backslash (\).
To list the Amazon Web Services accounts enabled to restore a snapshot, use the
describe-db-cluster-snapshot-attributes
Amazon CLI command.
You can also share a manual DB cluster snapshot with other Amazon Web Services accounts by
using the Amazon RDS API. To do so, call the
ModifyDBClusterSnapshotAttribute
operation. Specify restore for AttributeName, and
use the ValuesToAdd parameter to add a list of the IDs for the Amazon Web Services accounts
that are authorized to restore the manual snapshot.
To make a manual snapshot public and restorable by all Amazon Web Services accounts, use the value
all. However, take care not to add the all value for any
manual snapshots that contain private information that you don't want to be available to
all Amazon Web Services accounts. Also, don't specify all for encrypted snapshots, because
making such snapshots public isn't supported.
To list all of the Amazon Web Services accounts permitted to restore a snapshot, use the
DescribeDBClusterSnapshotAttributes
API operation.