Automatically connecting an EC2 instance and an Aurora DB cluster
You can use the Amazon RDS console to simplify setting up a connection between an Amazon Elastic Compute Cloud (Amazon EC2) instance and an Aurora DB cluster. Often, your DB cluster is in a private subnet and your EC2 instance is in a public subnet within a VPC. You can use a SQL client on your EC2 instance to connect to your DB cluster. The EC2 instance can also run web servers or applications that access your private DB cluster.
If you want to connect to an EC2 instance that isn't in the same VPC as the Aurora DB cluster, see the scenarios in Scenarios for accessing a DB cluster in a VPC.
Topics
Overview of automatic connectivity with an EC2 instance
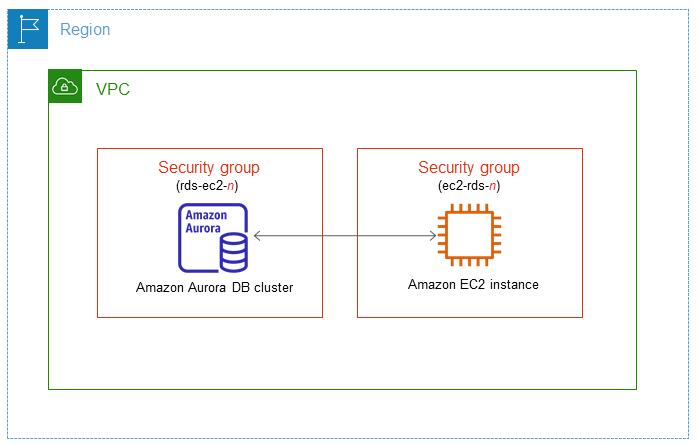
When you set up a connection between an EC2 instance and an Aurora DB cluster, Amazon RDSautomatically configures the VPC security group for your EC2 instance and for your DB cluster.
The following are requirements for connecting an EC2 instance with an Aurora DB cluster:
-
The EC2 instance must exist in the same VPC as the DB cluster.
If no EC2 instances exist in the same VPC, then the console provides a link to create one.
-
Currently, the DB cluster can't be an Aurora Serverless DB cluster or part of an Aurora global database.
-
The user who sets up connectivity must have permissions to perform the following Amazon EC2 operations:
-
ec2:AuthorizeSecurityGroupEgress -
ec2:AuthorizeSecurityGroupIngress -
ec2:CreateSecurityGroup -
ec2:DescribeInstances -
ec2:DescribeNetworkInterfaces -
ec2:DescribeSecurityGroups -
ec2:ModifyNetworkInterfaceAttribute -
ec2:RevokeSecurityGroupEgress
-
If the DB instance and EC2 instance are in different Availability Zones, your account may incur cross-Availability Zone costs.
When you set up a connection to an EC2 instance, Amazon RDS acts according to the current configuration of the security groups associated with the DB cluster and EC2 instance, as described in the following table.
| Current RDS security group configuration | Current EC2 security group configuration | RDS action |
|---|---|---|
|
There are one or more security groups associated with the DB cluster with a name that matches the pattern
|
There are one or more security groups associated with the EC2 instance with a name
that matches the pattern |
RDS takes no action. A connection was already configured automatically between the EC2 instance and DB cluster. Because a connection already exists between the EC2 instance and the RDS database, the security groups aren't modified. |
|
Either of the following conditions apply:
|
Either of the following conditions apply:
|
RDS action: create new security groups |
|
There are one or more security groups associated with the DB cluster with a name that matches the pattern
|
There are one or more security groups associated with the EC2 instance with a name that matches the
pattern |
RDS action: create new security groups |
|
There are one or more security groups associated with the DB cluster with a name that matches the pattern
|
A valid EC2 security group for the connection exists, but it is not associated
with the EC2 instance. This security group has a name that matches the pattern
|
RDS action: associate EC2 security group |
|
Either of the following conditions apply:
|
There are one or more security groups associated with the EC2 instance with a name
that matches the pattern |
RDS action: create new security groups |
RDS action: create new security groups
Amazon RDS takes the following actions:
-
Creates a new security group that matches the pattern
rds-ec2-. This security group has an inbound rule with the VPC security group of the EC2 instance as the source. This security group is associated with the DB cluster and allows the EC2 instance to access the DB cluster.n -
Creates a new security group that matches the pattern
ec2-rds-. This security group has an outbound rule with the VPC security group of the DB cluster as the target. This security group is associated with the EC2 instance and allows the EC2 instance to send traffic to the DB cluster.n
RDS action: associate EC2 security group
Amazon RDS associates the valid, existing EC2 security group with the EC2 instance. This security group allows the EC2 instance to send traffic to the DB cluster.
Automatically connecting an EC2 instance and an Aurora DB cluster
Before setting up a connection between an EC2 instance and an Aurora DB cluster, make sure you meet the requirements described in Overview of automatic connectivity with an EC2 instance.
If you make changes to security groups after you configure connectivity, the changes might affect the connection between the EC2 instance and the Aurora DB cluster.
Note
You can only set up a connection between an EC2 instance and an Aurora DB cluster automatically by using the Amazon Web Services Management Console. You can't set up a connection automatically with the Amazon CLI or RDS API.
To connect an EC2 instance and an Aurora DB cluster automatically
Sign in to the Amazon Web Services Management Console and open the Amazon RDS console at https://console.amazonaws.cn/rds/
. -
In the navigation pane, choose Databases, and then choose the DB cluster.
-
From Actions, choose Set up EC2 connection.
The Set up EC2 connection page appears.
-
On the Set up EC2 connection page, choose the EC2 instance.
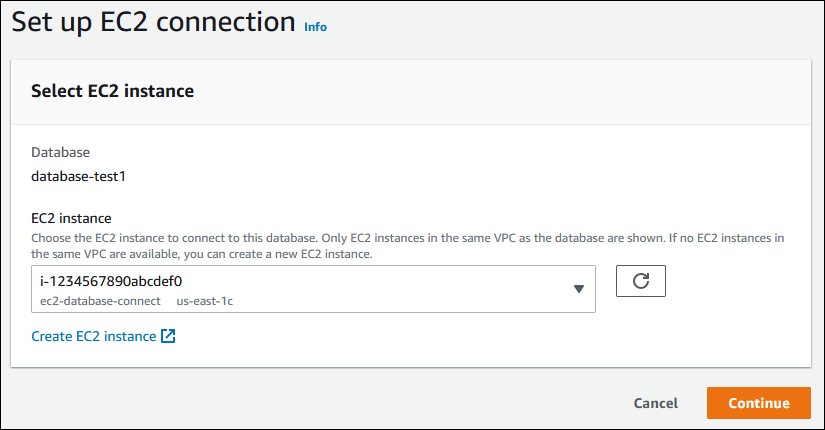
If no EC2 instances exist in the same VPC, choose Create EC2 instance to create one. In this case, make sure the new EC2 instance is in the same VPC as the DB cluster.
-
Choose Continue.
The Review and confirm page appears.
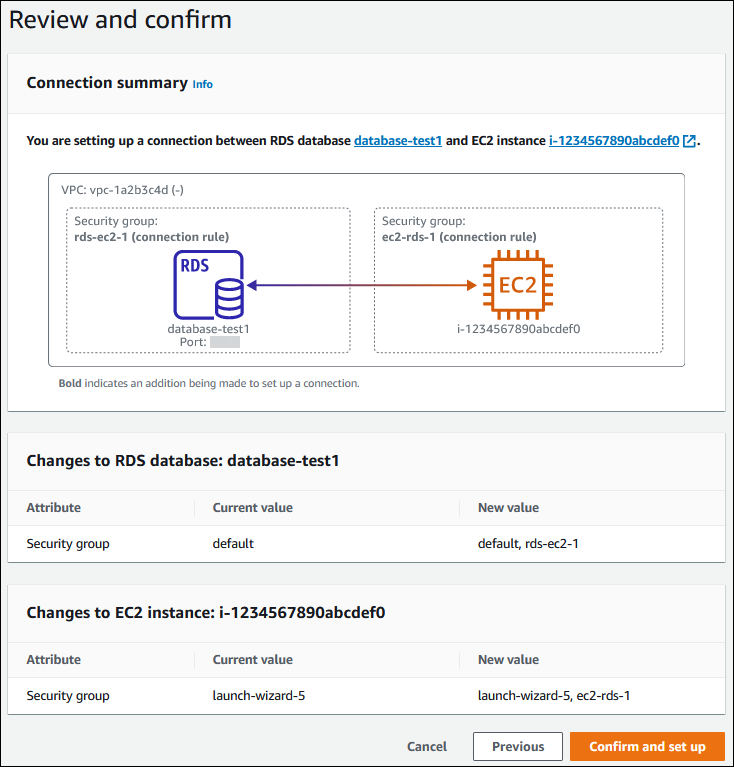
-
On the Review and confirm page, review the changes that RDS will make to set up connectivity with the EC2 instance.
If the changes are correct, choose Confirm and set up.
If the changes aren't correct, choose Previous or Cancel.
Viewing connected compute resources
You can use the Amazon Web Services Management Console to view the compute resources that are connected to an Aurora DB cluster. The resources shown include compute resource connections that were set up automatically. You can set up connectivity with compute resources automatically in the following ways:
-
You can select the compute resource when you create the database.
For more information, see Creating an Amazon Aurora DB cluster.
-
You can set up connectivity between an existing database and a compute resource.
For more information, see Automatically connecting an EC2 instance and an Aurora DB cluster.
The listed compute resources don't include ones that were connected to the database manually. For example, you can allow a compute resource to access a database manually by adding a rule to the VPC security group associated with the database.
For a compute resource to be listed, the following conditions must apply:
-
The name of the security group associated with the compute resource matches the pattern
ec2-rds-(wherenn -
The security group associated with the compute resource has an outbound rule with the port range set to the port that the DB cluster uses.
-
The security group associated with the compute resource has an outbound rule with the source set to a security group associated with the DB cluster.
-
The name of the security group associated with the DB cluster matches the pattern
rds-ec2-(wherenn -
The security group associated with the DB cluster has an inbound rule with the port range set to the port that the DB cluster uses.
-
The security group associated with the DB cluster has an inbound rule with the source set to a security group associated with the compute resource.
To view compute resources connected to an Aurora DB cluster
Sign in to the Amazon Web Services Management Console and open the Amazon RDS console at https://console.amazonaws.cn/rds/
. -
In the navigation pane, choose Databases, and then choose the name of the DB cluster.
-
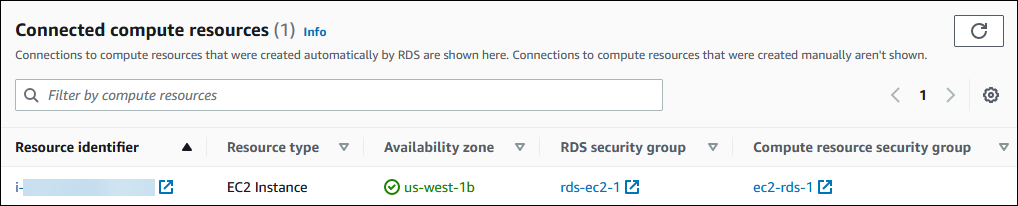
On the Connectivity & security tab, view the compute resources in the Connected compute resources.
Connecting to a DB instance that is running a specific DB engine
For information about connecting to a DB instance that is running a specific DB engine, follow the instructions for your DB engine: