Common Amazon Cognito scenarios
This topic describes six common scenarios for using Amazon Cognito.
The two main components of Amazon Cognito are user pools and identity pools. User pools are user directories that provide sign-up and sign-in options for your web and mobile app users. Identity pools provide temporary Amazon credentials to grant your users access to other Amazon Web Services services.
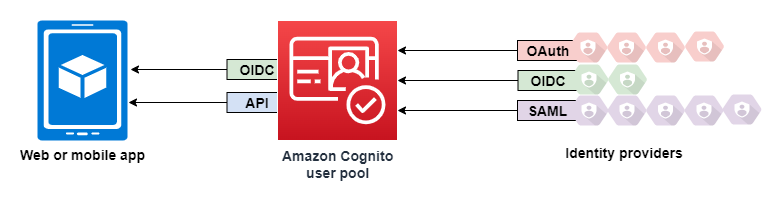
A user pool is a user directory in Amazon Cognito. Your app users can either sign in directly through a user pool, or they can federate through a third-party identity provider (IdP). The user pool manages the overhead of handling the tokens that are returned from social sign-in through Facebook, Google, Amazon, and Apple, and from OpenID Connect (OIDC) and SAML IdPs. Whether your users sign in directly or through a third party, all members of the user pool have a directory profile that you can access through an SDK.
With an identity pool, your users can obtain temporary Amazon credentials to access Amazon services, such as Amazon S3 and DynamoDB. Identity pools support anonymous guest users, as well as federation through third-party IdPs.
Topics
Authenticate with a user pool
You can enable your users to authenticate with a user pool. Your app users can either sign in directly through a user pool, or they can federate through a third-party identity provider (IdP). The user pool manages the overhead of handling the tokens that are returned from social sign-in through Facebook, Google, Amazon, and Apple, and from OpenID Connect (OIDC) and SAML IdPs.
After a successful authentication, your web or mobile app will receive user pool tokens from Amazon Cognito. You can use those tokens to retrieve Amazon credentials that allow your app to access other Amazon services, or you might choose to use them to control access to your server-side resources, or to the Amazon API Gateway.
For more information, see An example authentication session and Understanding user pool JSON web tokens (JWTs).
Access back-end resources with user pool tokens
After a successful user pool sign-in, your web or mobile app will receive user pool tokens from Amazon Cognito. You can use those tokens to control access to your server-side resources. You can also create user pool groups to manage permissions, and to represent different types of users. For more information on using groups to control access to your resources, see Adding groups to a user pool.

After you configure a domain for your user pool, Amazon Cognito provisions a hosted web UI that allows you to add sign-up and sign-in pages to your app. Using this OAuth 2.0 foundation, you can create your own resource server to enable your users to access protected resources. For more information, see Scopes, M2M, and resource servers.
For more information about user pool authentication, see An example authentication session and Understanding user pool JSON web tokens (JWTs).
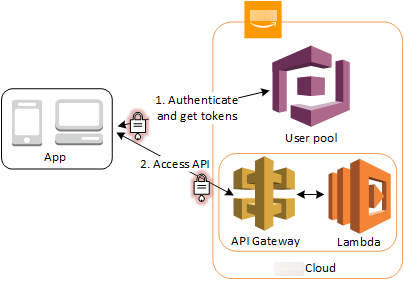
Access resources with API Gateway and Lambda with a user pool
You can enable your users to access your API through API Gateway. API Gateway validates the tokens from a successful user pool authentication, and uses them to grant your users access to resources including Lambda functions, or your own API.
You can use groups in a user pool to control permissions with API Gateway by mapping group membership to IAM roles. The groups that a user is a member of are included in the ID token provided by a user pool when your app user signs in. For more information on user pool groups See Adding groups to a user pool.
You can submit your user pool tokens with a request to API Gateway for verification by an Amazon Cognito authorizer Lambda function. For more information on API Gateway, see Using API Gateway with Amazon Cognito user pools.
Access Amazon services with a user pool and an identity pool
After a successful user pool authentication, your app will receive user pool tokens from Amazon Cognito. You can exchange them for temporary access to other Amazon services with an identity pool. For more information, see Accessing Amazon Web Services services using an identity pool after sign-in and Getting started with Amazon Cognito identity pools.
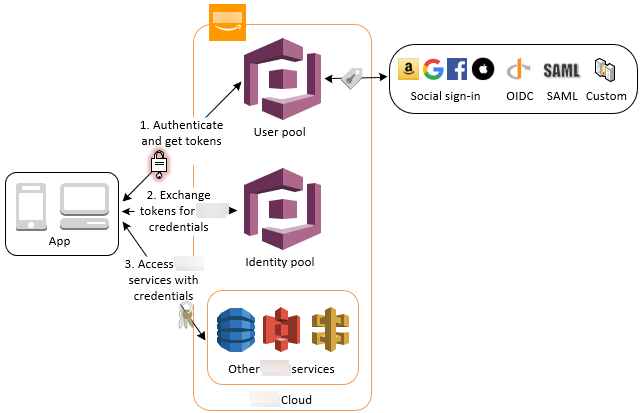
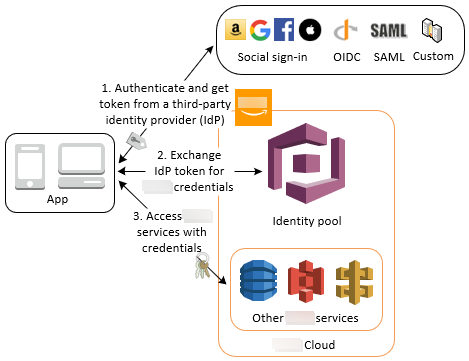
Authenticate with a third party and access Amazon services with an identity pool
You can enable your users access to Amazon services through an identity pool. An identity pool requires an IdP token from a user that's authenticated by a third-party identity provider (or nothing if it's an anonymous guest). In exchange, the identity pool grants temporary Amazon credentials that you can use to access other Amazon services. For more information, see Getting started with Amazon Cognito identity pools.
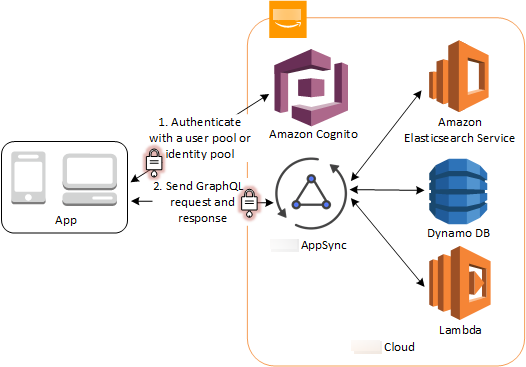
Access Amazon AppSync resources with Amazon Cognito
You can grant your users access to Amazon AppSync resources with tokens from a successful Amazon Cognito user pool authentication. For more information, see AMAZON_COGNITO_USER_POOLS authorization in the Amazon AppSync Developer Guide.
You can also sign requests to the Amazon AppSync GraphQL API with the IAM credentials that you receive from an identity pool. See AWS_IAM authorization.