Signing out SAML users with single sign-out
Amazon Cognito supports SAML 2.0 single logout
When you configure your SAML IdP to support Sign-out flow,
Amazon Cognito redirects your user with a signed SAML logout request to your IdP. Amazon Cognito
determines the redirect location from the SingleLogoutService URL in
your IdP metadata. Amazon Cognito signs the sign-out request with your user pool signing
certificate.
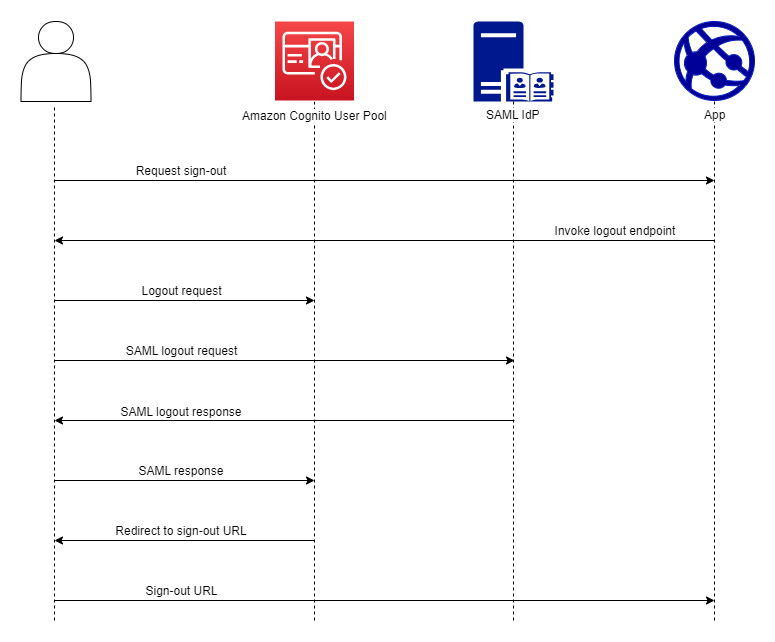
When you direct a user with a SAML session to your user pool /logout
endpoint, Amazon Cognito redirects your SAML user with the following request to the SLO
endpoint that's specified in the IdP metadata.
https://[SingleLogoutService endpoint]? SAMLRequest=[encoded SAML request]& RelayState=[RelayState]& SigAlg=http://www.w3.org/2001/04/xmldsig-more#rsa-sha256& Signature=[User pool RSA signature]
Your user then returns to your saml2/logout endpoint with a
LogoutResponse from their IdP. Your IdP must send the
LogoutResponse in an HTTP POST request. Amazon Cognito then
redirects them to the redirect destination from their initial sign-out
request.
Your SAML provider might send a LogoutResponse with more than one
AuthnStatement in it. The sessionIndex in the first
AuthnStatement in a response of this type must match the
sessionIndex in the SAML response that originally authenticated the
user. If the sessionIndex is in any other AuthnStatement,
Amazon Cognito won’t recognize the session and your user won’t be signed out.