Server certificate configuration for OCSP stapling
Amazon IoT Core supports Online
Certificate Status Protocol (OCSP)
You can enable server certificate OCSP stapling in Amazon IoT Core to check the validity of the certificate by querying the OCSP responder periodically. The OCSP stapling setting is part of the process to create or update a domain configuration with a custom domain. OCSP stapling checks for revocation status on the server certificate continuously. This helps verify that any certificates that have been revoked by the CA are no longer trusted by the clients connecting to your custom domains. For more information, see Enabling server certificate OCSP in Amazon IoT Core.
Server certificate OCSP stapling provides real-time revocation status check, reduces the latency associated with checking the revocation status, and improves privacy and reliability of secure connections. For more information about the benefits of using OCSP stapling, see Benefits of using OCSP stapling compared to client-side OCSP checks.
Note
This feature is not available in Amazon GovCloud (US) Regions.
In this topic:
What is OCSP?
The Online Certificate Status Protocol (OCSP) aids in providing a server certificate's revocation status for a Transport Layer Security (TLS) handshake.
Key concepts
The following key concepts provide details about the Online Certificate Status Protocol (OCSP).
OCSP
OCSP
OCSP responder
An OCSP responder (also known as OCSP server) receives and responds to OCSP requests from clients that seek to verify the revocation status of certificates.
Client-side OCSP
In client-side OCSP, the client uses OCSP to contact an OCSP responder to check the certificate's revocation status during the TLS handshake.
Server-side OCSP
In server-side OCSP (also known as OCSP stapling), the server is enabled (rather than the client) to make the request to the OCSP responder. The server staples the OCSP response to the certificate and returns it to the client during the TLS handshake.
OCSP diagrams
The following diagram illustrates how client-side OCSP and server-side OCSP work.
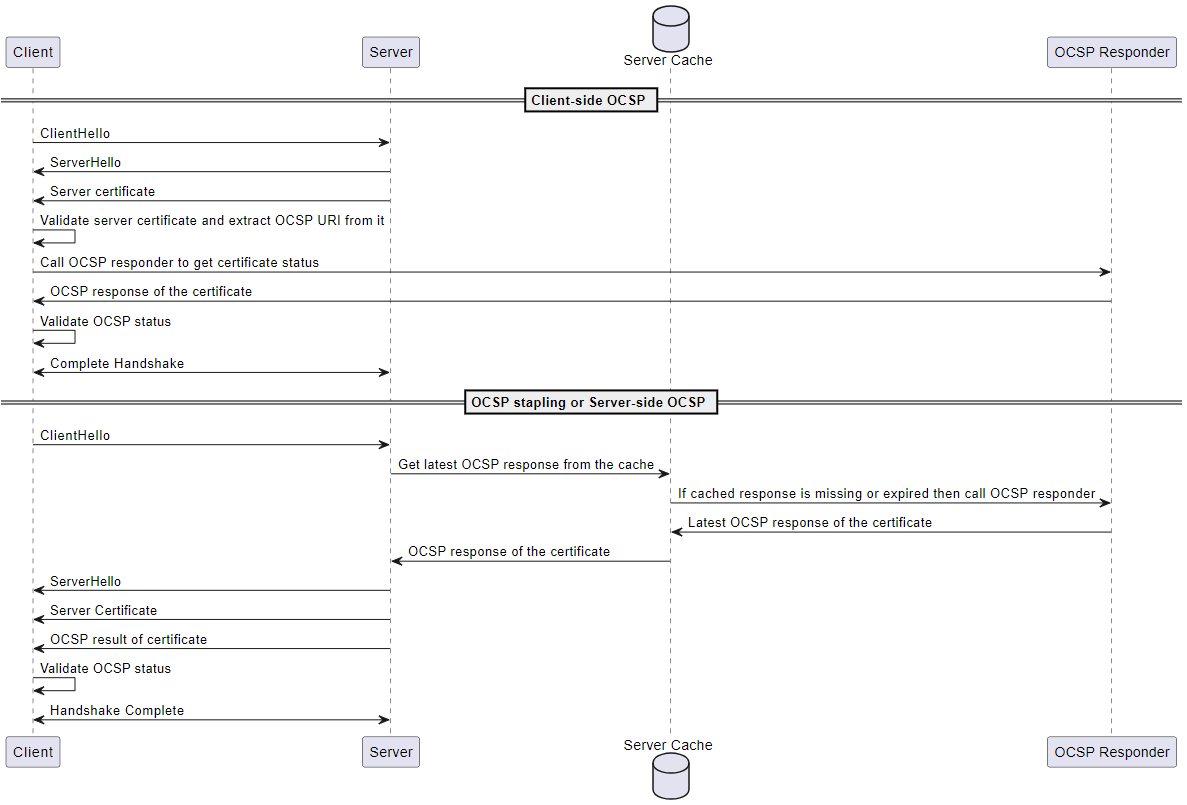
Client-side OCSP
The client sends a
ClientHellomessage to initiate the TLS handshake with the server.The server receives the message and responds with a
ServerHellomessage. The server also sends the server certificate to the client.The client validates the server certificate and extracts an OCSP URI from it.
The client sends a certificate revocation check request to the OCSP responder.
The OCSP responder sends an OCSP response.
The client validates the certificate status from the OCSP response.
The TLS handshake is completed.
Server-side OCSP
-
The client sends a
ClientHellomessage to initiate the TLS handshake with the server. The server receives the message and gets the latest cached OCSP response. If the cached response is missing or expired, the server will call the OCSP responder for certificate status.
The OCSP responder sends an OCSP response to the server.
The server sends a
ServerHellomessage. The server also sends the server certificate and the certificate status to the client.The client validates the OCSP certificate status.
The TLS handshake is completed.
How OCSP stapling works
OCSP stapling is used during the TLS handshake between the client and the server to check the server certificate revocation status. The server makes the OCSP request to the OCSP responder and staples the OCSP responses to the certificates returned to the client. By having the server make the request to the OCSP responder, the responses can be cached and then used multiple times for many clients.
How OCSP stapling works in Amazon IoT Core
The following diagram shows how server-side OCSP stapling works in Amazon IoT Core.
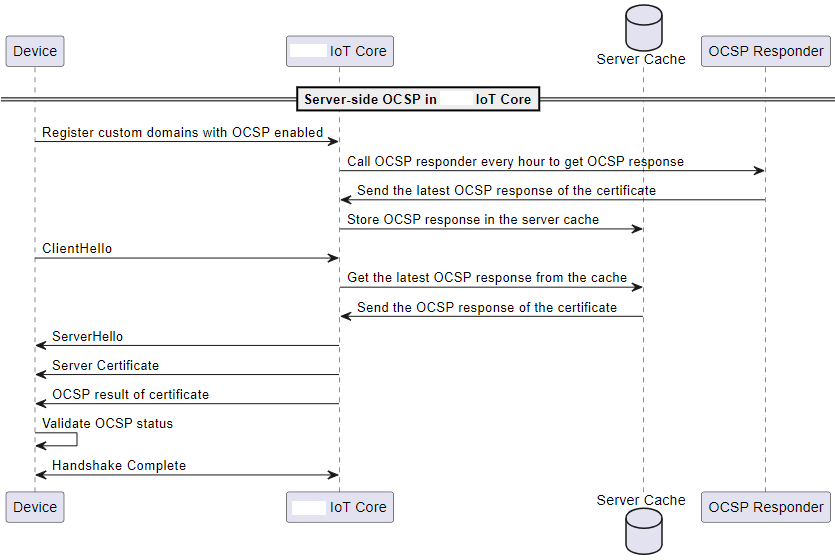
-
The device needs to be registered with custom domains with OCSP stapling enabled.
-
Amazon IoT Core calls OCSP responder every hour to get the certificate status.
-
The OCSP responder receives the request, sends the latest OCSP response, and stores the cached OCSP response.
-
The device sends a
ClientHellomessage to initiate the TLS handshake with Amazon IoT Core. -
Amazon IoT Core gets the latest OCSP response from the server cache, which responds with an OCSP response of the certificate.
-
The server sends a
ServerHellomessage to the device. The server also sends the server certificate and the certificate status to the client. -
The device validates the OCSP certificate status.
-
The TLS handshake is completed.
Benefits of using OCSP stapling compared to client-side OCSP checks
A few advantages of using server certificate OCSP stapling include the following:
Improved privacy
Without OCSP stapling, the client's device can expose information to third-party OCSP responders, potentially compromising user privacy. OCSP stapling mitigates this issue by having the server obtain the OCSP response and deliver it directly to the client.
Improved reliability
OCSP stapling can improve the reliability of secure connections because it reduces the risk of OCSP server outages. When OCSP responses are stapled, the server includes the most recent response with the certificate. This is so that clients have access to the revocation status even if the OCSP responder is temporarily unavailable. OCSP stapling helps mitigate these problems because the server fetches OCSP responses periodically and includes the cached responses in the TLS handshake. This reduces reliance on the real-time availability of OCSP responders.
Reduced server load
OCSP stapling offloads the burden of responding to OCSP requests from OCSP responders to the server. This can help distribute the load more evenly, making the certificate validation process more efficient and scalable.
Reduced latency
OCSP stapling reduces the latency associated with checking the revocation status of a certificate during the TLS handshake. Instead of the client having to query an OCSP server separately, the server sends the request and attaches the OCSP response with the server certificate during the handshake.
Enabling server certificate OCSP in Amazon IoT Core
To enable server certificate OCSP stapling in Amazon IoT Core, create a domain configuration for a custom domain or update an existing custom domain configuration. For general information about creating a domain configuration with a custom domain, see Creating and configuring customer managed domains.
Use the following instructions to enable OCSP server stapling using Amazon Web Services Management Console or Amazon CLI.
To enable server certificate OCSP stapling using the Amazon IoT console:
In the navigation menu, choose Settings, and then choose Create domain configuration, or choose an existing domain configuration for a custom domain.
If you choose to create a new domain configuration in the previous step, you will see the Create domain configuration page. In the Domain configuration properties section, choose Custom domain. Enter the information to create a domain configuration.
If you choose to update an existing domain configuration for a custom domain, you will see the Domain configuration details page. Choose Edit.
To enable OCSP server stapling, choose Enable server certificate OCSP stapling in the Server certificate configurations subsection.
-
Choose Create domain configuration or Update domain configuration.
To enable server certificate OCSP stapling using Amazon CLI:
If you create a new domain configuration for a custom domain, the command to enable the OCSP server stapling can look like the following:
aws iot create-domain-configuration --domain-configuration-name "myDomainConfigurationName" \ --server-certificate-arns arn:aws:iot:us-east-1:123456789012:cert/f8c1e5480266caef0fdb1bf97dc1c82d7ba2d3e2642c5f25f5ba364fc6b79ba3\ --server-certificate-config "enableOCSPCheck=true|false"If you update an existing domain configuration for a custom domain, the command to enable the OCSP server stapling can look like the following:
aws iot update-domain-configuration --domain-configuration-name "myDomainConfigurationName" \ --server-certificate-arns arn:aws:iot:us-east-1:123456789012:cert/f8c1e5480266caef0fdb1bf97dc1c82d7ba2d3e2642c5f25f5ba364fc6b79ba3\ --server-certificate-config "enableOCSPCheck=true|false"
For more information, see CreateDomainConfiguration and UpdateDomainConfiguration from the Amazon IoT API Reference.
Configuring server certificate OCSP for private endpoints in Amazon IoT Core
OCSP for private endpoints lets you use your private OCSP resources within your Amazon Virtual Private Cloud (Amazon VPC) for Amazon IoT Core operations. The process involves setting up a Lambda function that acts as an OCSP responder. The Lambda function might use your private OCSP resources to craft OCSP responses that Amazon IoT Core will use.
Lambda function
Before you configure server OCSP for a private endpoint, create a Lambda function that acts as a Request for Comments (RFC) 6960-compliant Online Certificate Status Protocol (OCSP) responder, supporting basic OCSP responses. The Lambda function accepts a base64-encoding of the OCSP request in the Distinguished Encoding Rules (DER) format. The Lambda function's response is also a base64-encoded OCSP response in the DER format. The response size must not exceed 4 kilobytes (KiB). The Lambda function must be in the same Amazon Web Services account and Amazon Web Services Region as the domain configuration. The following are example Lambda functions.
Example Lambda functions
Authorizing Amazon IoT to invoke your Lambda function
In the process of creating the domain configuration with a Lambda OCSP responder, you must grant Amazon IoT permission to invoke the Lambda function after the function is created. To grant the permission, you can use the add-permission CLI command.
Grant permission to your Lambda function using the Amazon CLI
-
After inserting your values, enter the following command. Note that the
statement-idvalue must be unique. ReplaceId-1234ResourceConflictExceptionerror.aws lambda add-permission \ --function-name "ocsp-function" \ --principal "iot.amazonaws.com" \ --action "lambda:InvokeFunction" \ --statement-id "Id-1234" \ --source-arnarn:aws:iot:us-east-1:123456789012:domainconfiguration/<domain-config-name>/*--source-account123456789012IoT domain configuration ARNs will follow the following pattern. The service-generated suffix will not be known prior to creation time, thus you must replace the suffix with a
*. You can update the permission once the domain configuration has been created and the exact ARN is known.arn:aws:iot:use-east-1:123456789012:domainconfiguration/domain-config-name/service-generated-suffix -
If the command succeeds, it returns a permission statement, such as this example. You can continue to the next section to configure OCSP stapling for private endpoints.
{ "Statement": "{\"Sid\":\"Id-1234\",\"Effect\":\"Allow\",\"Principal\":{\"Service\":\"iot.amazonaws.com\"},\"Action\":\"lambda:InvokeFunction\",\"Resource\":\"arn:aws:lambda:us-east-1:123456789012:function:ocsp-function\",\"Condition\":{\"ArnLike\":{\"AWS:SourceArn\":\"arn:aws:iot:us-east-1:123456789012:domainconfiguration/domain-config-name/*\"}}}" }If the command doesn't succeed, it returns an error, such as this example. You'll need to review and correct the error before you continue.
An error occurred (AccessDeniedException) when calling the AddPermission operation: User: arn:aws:iam::57EXAMPLE833:user/EXAMPLE-1 is not authorized to perform: lambda:AddPer mission on resource: arn:aws:lambda:us-east-1:123456789012:function:ocsp-function
Configuring server OCSP stapling for private endpoints
To configure server certificate OCSP stapling using the Amazon IoT console:
From the navigation menu, choose Settings, and then choose Create domain configuration, or choose an existing domain configuration for a custom domain.
If you choose to create a new domain configuration in the previous step, you will see the Create domain configuration page. In the Domain configuration properties section, choose Custom domain. Enter the information to create a domain configuration.
If you choose to update an existing domain configuration for a custom domain, you will see the Domain configuration details page. Choose Edit.
To enable OCSP server stapling, choose Enable server certificate OCSP stapling in the Server certificate configurations subsection.
-
Choose Create domain configuration or Update domain configuration.
To configure server certificate OCSP stapling using Amazon CLI:
If you create a new domain configuration for a custom domain, the command to configure server certificate OCSP for private endpoints can look like the following:
aws iot create-domain-configuration --domain-configuration-name "myDomainConfigurationName" \ --server-certificate-arns arn:aws:iot:us-east-1:123456789012:cert/f8c1e5480266caef0fdb1bf97dc1c82d7ba2d3e2642c5f25f5ba364fc6b79ba3\ --server-certificate-config "enableOCSPCheck=true, ocspAuthorizedResponderArn=arn:aws:acm:us-east-1:123456789012:certificate/certificate_ID, ocspLambdaArn=arn:aws:lambda:us-east-1:123456789012:function:my-function"If you update an existing domain configuration for a custom domain, the command to configure server certificate OCSP for private endpoints can look like the following:
aws iot update-domain-configuration --domain-configuration-name "myDomainConfigurationName" \ --server-certificate-arns arn:aws:iot:us-east-1:123456789012:cert/f8c1e5480266caef0fdb1bf97dc1c82d7ba2d3e2642c5f25f5ba364fc6b79ba3\ --server-certificate-config "enableOCSPCheck=true, ocspAuthorizedResponderArn=arn:aws:acm:us-east-1:123456789012:certificate/certificate_ID, ocspLambdaArn=arn:aws:lambda:us-east-1:123456789012:function:my-function"
- enableOCSPCheck
-
This is a Boolean value that indicates whether server OCSP stapling check is enabled or not. To enable server certificate OCSP stapling, this value must be true.
- ocspAuthorizedResponderArn
-
This is a string value of the Amazon Resource Name (ARN) for an X.509 certificate stored in Amazon Certificate Manager (ACM). If provided, Amazon IoT Core will use this certificate to validate the signature of the received OCSP response. If not provided, Amazon IoT Core will use the issuing certificate to validate the responses. The certificate must be in the same Amazon Web Services account and Amazon Web Services Region as the domain configuration. For more information about how to register your authorized responder certificate, see Import certificates into Amazon Certificate Manager.
- ocspLambdaArn
-
This is a string value of the Amazon Resource Name (ARN) for a Lambda function that acts as a Request for Comments (RFC) 6960-compliant (OCSP) responder, supporting basic OCSP responses. The Lambda function accepts a base64-encoding of the OCSP request which is encoded using the DER format. The Lambda function's response is also a base64-encoded OCSP response in the DER format. The response size must not exceed 4 kilobytes (KiB). The Lambda function must be in the same Amazon Web Services account and Amazon Web Services Region as the domain configuration.
For more information, see CreateDomainConfiguration and UpdateDomainConfiguration from the Amazon IoT API Reference.
Important notes for using server certificate OCSP stapling in Amazon IoT Core
When you use server certificate OCSP in Amazon IoT Core, keep the following in mind:
-
Amazon IoT Core supports only those OCSP responders that are reachable over public IPv4 addresses.
-
The OCSP stapling feature in Amazon IoT Core doesn't support authorized responder. All OCSP responses must be signed by the CA that signed the certificate, and the CA must be part of the certificate chain of the custom domain.
-
The OCSP stapling feature in Amazon IoT Core doesn't support custom domains that are created using self-signed certificates.
-
Amazon IoT Core calls an OCSP responder every hour and caches the response. If the call to the responder fails, Amazon IoT Core will staple the most recent valid response.
-
If
nextUpdateTimeis no longer valid, Amazon IoT Core will remove the response from the cache, and TLS handshake will not include the OCSP response data until the next successful call to the OCSP responder. This can happen when the cached response has expired before the server gets a valid response from the OCSP responder. The value ofnextUpdateTimesuggests that the OCSP response will be valid until this time. For more information aboutnextUpdateTime, see Server certificate OCSP log entries. -
Sometimes, Amazon IoT Core fails to receive the OCSP response or removes the existing OCSP response because it's expired. If situations like these happen, Amazon IoT Core will continue to use the server certificate provided by the custom domain without the OCSP response.
-
The size of the OCSP response cannot exceed 4 KiB.
Troubleshooting server certificate OCSP stapling in Amazon IoT Core
Amazon IoT Core emits the RetrieveOCSPStapleData.Success metric and the
RetrieveOCSPStapleData log entries to CloudWatch. The metric and the log
entries can help detect issues related to retrieving OCSP responses. For more
information, see Server certificate OCSP stapling metrics and Server certificate OCSP log entries.