Tutorial: Configuring private network access using a Linux Bastion Host
This tutorial walks you through the steps to create an SSH tunnel from your computer to the to the Apache Airflow webserver for your Amazon Managed Workflows for Apache Airflow environment. It assumes you've already created an Amazon MWAA environment. Once set up, a Linux Bastion Host acts as a jump server allowing a secure connection from your computer to the resources in your VPC. You'll then use a SOCKS proxy management add-on to control the proxy settings in your browser to access your Apache Airflow UI.
Private network
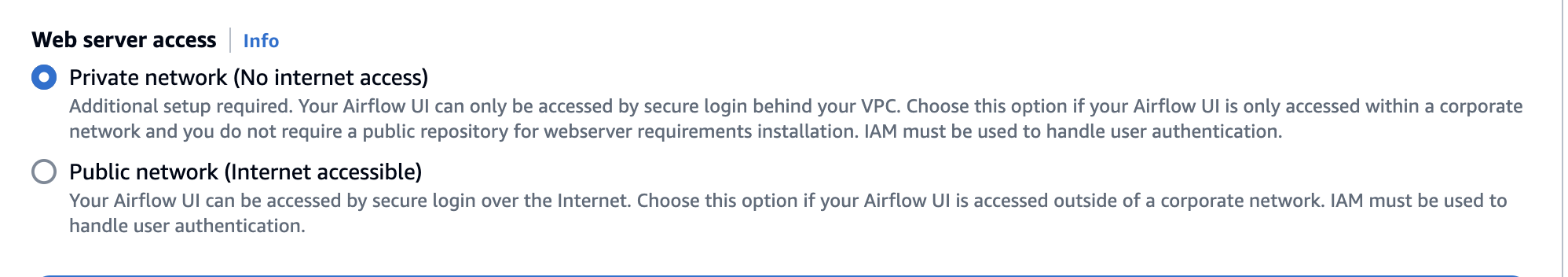
This tutorial assumes you've chosen the Private network access mode for your Apache Airflow webserver.
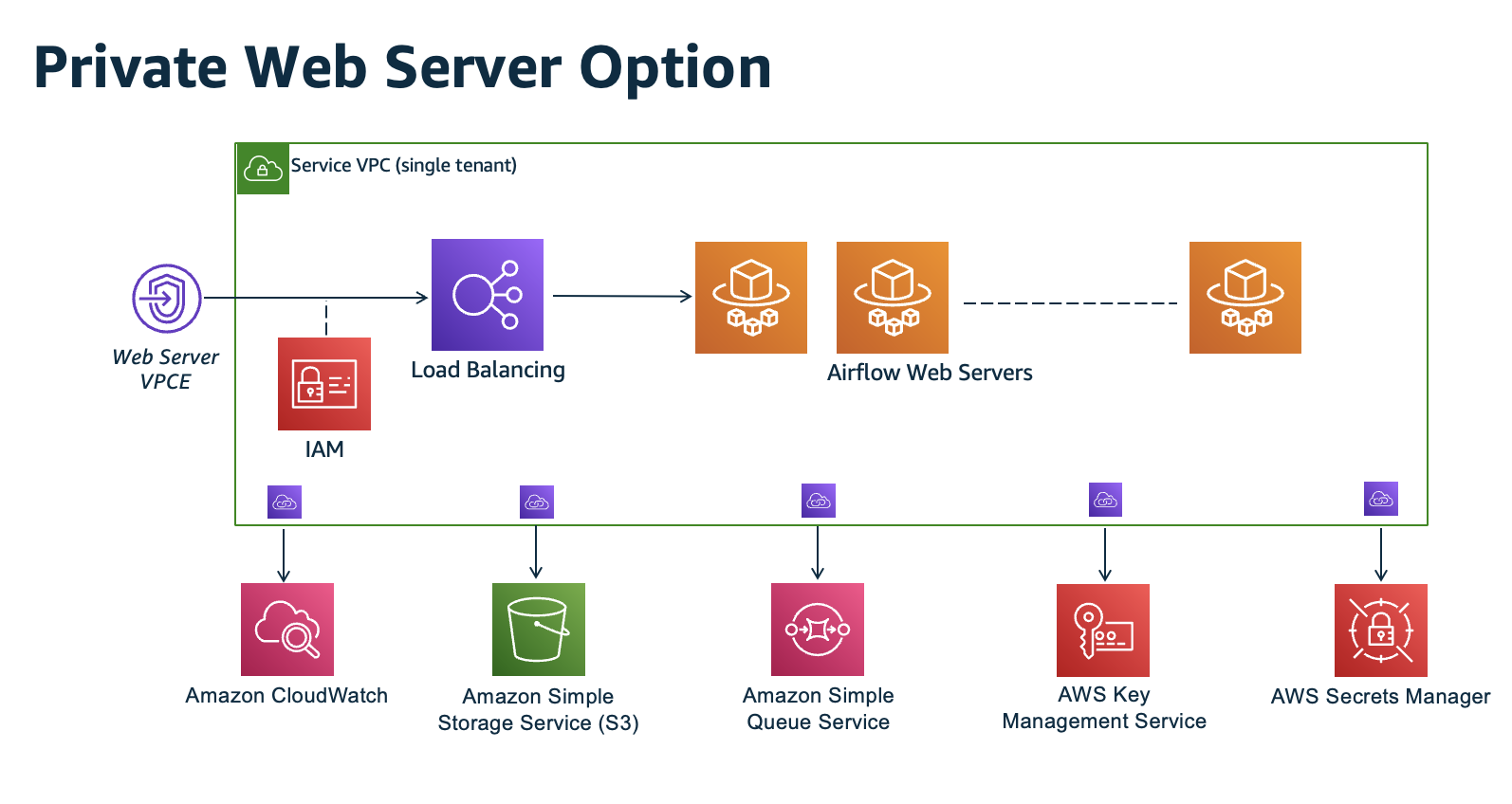
The private network access mode limits access to the Apache Airflow UI to users within your Amazon VPC who have been granted access to the IAM policy for your environment.
When you create an environment with private webserver access, you must package all of your dependencies in a Python wheel archive (.whl), then
reference the .whl in your requirements.txt. For instructions on packaging and installing your dependencies
using wheel, refer to Managing dependencies using Python wheel.
The following image depicts where to find the Private network option on the Amazon MWAA console.
Use cases
You can use this tutorial after you've created an Amazon MWAA environment. You must use the same Amazon VPC, VPC security groups, and public subnets as your environment.
Before you begin
-
Check for user permissions. Be sure that your account in Amazon Identity and Access Management (IAM) has sufficient permissions to create and manage VPC resources.
-
Use your Amazon MWAA VPC. This tutorial assumes that you are associating the bastion host to an existing VPC. The Amazon VPC must be in the same region as your Amazon MWAA environment and have two private subnets, as defined in Create the VPC network.
-
Create an SSH key. You need to create an Amazon EC2 SSH key (.pem) in the same Region as your Amazon MWAA environment to connect to the virtual servers. If you don't have an SSH key, refer to Create or import a key pair in the Amazon EC2 User Guide.
Objectives
In this tutorial, you'll do the following:
-
Create a Linux Bastion Host instance using a Amazon CloudFormation template for an existing VPC
. -
Authorize inbound traffic to the bastion instance's security group using an ingress rule on port
22. -
Authorize inbound traffic from an Amazon MWAA environment's security group to the bastion instance's security group.
-
Create an SSH tunnel to the bastion instance.
-
Install and configure the FoxyProxy add-on for the Firefox browser to access the Apache Airflow UI.
Step one: Create the bastion instance
The following section describes the steps to create the linux bastion instance using a Amazon CloudFormation template for an existing VPC
To create the Linux Bastion Host
-
Open the Deploy Quick Start
page on the Amazon CloudFormation console. -
Use the region selector in the navigation bar to choose the same Amazon Web Services Region as your Amazon MWAA environment.
-
Choose Next.
-
Enter a name in the Stack name text field, such as
mwaa-linux-bastion. -
On the Parameters, Network configuration pane, choose the following options:
-
Choose your Amazon MWAA environment's VPC ID.
-
Choose your Amazon MWAA environment's Public subnet 1 ID.
-
Choose your Amazon MWAA environment's Public subnet 2 ID.
-
Enter the narrowest possible address range (for example, an internal CIDR range) in Allowed bastion external access CIDR.
Note
The simplest way to identify a range is to use the same CIDR range as your public subnets. For example, the public subnets in the Amazon CloudFormation template on the Create the VPC network page are
10.192.10.0/24and10.192.11.0/24.
-
-
On the Amazon EC2 configuration pane, choose the following:
-
Choose your SSH key in the dropdown list in Key pair name.
-
Enter a name in Bastion Host Name.
-
Choose true for TCP forwarding.
Warning
TCP forwarding must be set to true in this step. Otherwise, you won't be able to create an SSH tunnel in the next step.
-
-
Choose Next, Next.
-
Select the acknowledgement, and then choose Create stack.
To learn more about the architecture of your Linux Bastion Host, refer to Linux Bastion Hosts on the Amazon Cloud: Architecture.
Step two: Create the ssh tunnel
The following steps describe how to create the ssh tunnel to your linux bastion. An SSH tunnel recieves the request from your local IP address to the linux bastion, which is why TCP forwarding for the linux bastion was set to true in previous steps.
Note
If you receive a Permission denied (publickey) error, we recommend using the AWSSupport-TroubleshootSSH tool, and choose Run this Automation (console) to troubleshoot your SSH setup.
Step three: Configure the bastion security group as an inbound rule
Access to the servers and regular internet access from the servers is allowed with a special maintenance security group attached to those servers. The following steps describe how to configure the bastion security group as an inbound source of traffic to an environment's VPC security group.
-
Open the Environments
page on the Amazon MWAA console. -
Choose an environment.
-
On the Networking pane, choose VPC security group.
-
Choose Edit inbound rules.
-
Choose Add rule.
-
Choose your VPC security group ID in the Source dropdown list.
-
Leave the remaining options blank, or set to their default values.
-
Choose Save rules.
Step four: Copy the Apache Airflow URL
The following steps describe how to open the Amazon MWAA console and copy the URL to the Apache Airflow UI.
-
Open the Environments
page on the Amazon MWAA console. -
Choose an environment.
-
Copy the URL in Airflow UI for subsequent steps.
Step five: Configure proxy settings
If you use an SSH tunnel with dynamic port forwarding, you must use a SOCKS proxy management add-on to control the proxy settings in your browser. For example, you can use the --proxy-server feature of Chromium to kick off a browser session, or use the FoxyProxy extension in the Mozilla FireFox browser.
Option one: Setup an SSH Tunnel using local port forwarding
If you do not wish to use a SOCKS proxy, you can set up an SSH tunnel using local port forwarding. The following example command accesses the Amazon EC2 ResourceManager web interface by forwarding traffic on local port 8157.
-
Open a new command prompt window.
-
Enter the following command to open an SSH tunnel.
ssh -imykeypair.pem-N -L 8157:YOUR_VPC_ENDPOINT_ID-vpce.us-east-1.airflow.amazonaws.com:443 ubuntu@YOUR_PUBLIC_IPV4_DNS.us-east-1.compute.amazonaws.com-Lsignifies the use of local port forwarding which you can use to specify a local port used to forward data to the identified remote port on the node's local webserver. -
Enter
http://localhost:8157/in your browser.Note
You might need to use
https://localhost:8157/.
Option two: Proxies using the command line
You can use most web browsers to configure proxies using a command line or configuration parameter. For example, with Chromium you can start the browser with the following command:
chromium --proxy-server="socks5://localhost:8157"
This starts a browser session which uses the ssh tunnel you created in previous steps to proxy its requests. You can open your Private Amazon MWAA environment URL (with https://) as follows:
https://YOUR_VPC_ENDPOINT_ID-vpce.us-east-1.airflow.amazonaws.com/home.
Option three: Proxies using FoxyProxy for Mozilla Firefox
The following example demonstrates a FoxyProxy Standard (version 7.5.1) configuration for Mozilla Firefox. FoxyProxy provides a set of proxy management tools. It lets you use a proxy server for URLs that match patterns corresponding to domains used by the Apache Airflow UI.
-
In Firefox, open the FoxyProxy Standard
extension page. -
Choose Add to Firefox.
-
Choose Add.
-
Choose the FoxyProxy icon in your browser's toolbar, choose Options.
-
Copy the following code and save locally as
mwaa-proxy.json. Substitute the sample value inYOUR_HOST_NAMEwith your Apache Airflow URL.{ "e0b7kh1606694837384": { "type": 3, "color": "#66cc66", "title": "airflow", "active": true, "address": "localhost", "port": 8157, "proxyDNS": false, "username": "", "password": "", "whitePatterns": [ { "title": "airflow-ui", "pattern": "YOUR_HOST_NAME", "type": 1, "protocols": 1, "active": true } ], "blackPatterns": [], "pacURL": "", "index": -1 }, "k20d21508277536715": { "active": true, "title": "Default", "notes": "These are the settings that are used when no patterns match a URL.", "color": "#0055E5", "type": 5, "whitePatterns": [ { "title": "all URLs", "active": true, "pattern": "*", "type": 1, "protocols": 1 } ], "blackPatterns": [], "index": 9007199254740991 }, "logging": { "active": true, "maxSize": 500 }, "mode": "patterns", "browserVersion": "82.0.3", "foxyProxyVersion": "7.5.1", "foxyProxyEdition": "standard" } -
On the Import Settings from FoxyProxy 6.0+ pane, choose Import Settings and select the
mwaa-proxy.jsonfile. -
Choose OK.
Step six: Open the Apache Airflow UI
The following steps describe how to open your Apache Airflow UI.
-
Open the Environments
page on the Amazon MWAA console. -
Choose Open Airflow UI.
What's next?
-
Learn how to run Airflow CLI commands on an SSH tunnel to a bastion host in Apache Airflow CLI command reference.
-
Learn how to upload DAG code to your Amazon S3 bucket in Adding or updating DAGs.