Create single-account permissions for an IAM user
When the CA administrator (that is, the owner of the CA) and the certificate issuer reside in a single Amazon account, a best practice is to separate the issuer and administrator roles by creating an Amazon Identity and Access Management (IAM) user with limited permissions. For information about using IAM with Amazon Private CA, along with example permissions, see Identity and Access Management (IAM) for Amazon Private Certificate Authority.
Single-account case 1: Issuing an unmanaged certificate
In this case, the account owner creates a private CA and then creates an IAM
user with permission to issue certificates signed by the private CA. The IAM
user issues a certificate by calling the Amazon Private CA
IssueCertificate API.
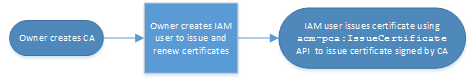
Certificates issued in this manner are unmanaged, which means that an
administrator must export them and install them on devices where they are intended
to be used. They also must be manually renewed when they expire. Issuing a
certificate using this API requires a certificate signing request (CSR) and key pair
that is generated outside of Amazon Private CA by OpenSSLIssueCertificate
documentation.
Single-account case 2: Issuing a managed certificate through ACM
This second case involves API operations from both ACM and PCA. The account
owner creates a private CA and IAM user as before. The account owner then
grants permission to the ACM
service principal to renew automatically any certificates that are signed by
this CA. The IAM user again issues the certificate, but this time by calling
the ACM RequestCertificate API, which handles CSR and key
generation. When the certificate expires, ACM automates the renewal
workflow.
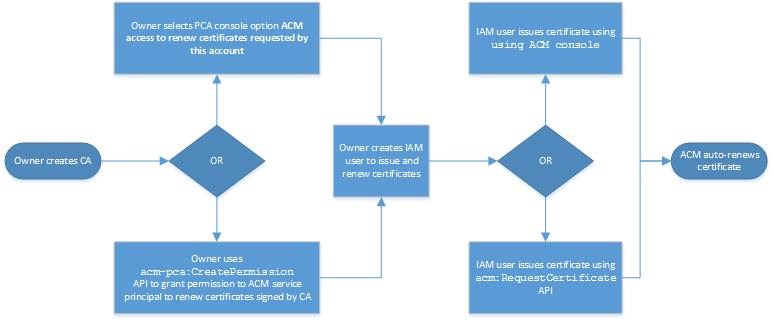
The account owner has the option of granting renewal permission through the
management console during or after CA creation or using the PCA
CreatePermission API. The managed certificates created from this
workflow are available for use on with Amazon services that are integrated with
ACM.
The following section contains procedures for granting renewal permissions.
Assign certificate renewal permissions to ACM
With managed renewal in Amazon Certificate Manager (ACM), you can automate the certificate renewal process for both public and private certificates. In order for ACM to automatically renew the certificates generated by a private CA, the ACM service principal must be given all possible permissions by the CA itself. If these renewal permissions are not present for ACM, the CA's owner (or an authorized representative) must manually reissue each private certificate when it expires.
Important
These procedures for assigning renewal permissions apply only when the CA owner and the certificate issuer reside in the same Amazon account. For cross-account scenarios, see Attach a policy for cross-account access.
Renewal permissions can be delegated during private
CA creation or altered anytime after as long as the CA is in the
ACTIVE state.
You can manage private CA permissions from the Amazon Private CA Console
To assign private CA permissions to ACM (console)
-
Sign in to your Amazon account and open the Amazon Private CA console at https://console.amazonaws.cn/acm-pca/home
. -
On the Private certificate authorities page, choose your private CA from the list.
-
Choose Actions, Configure CA permissions.
-
Select Authorize ACM access to renew certificates requested by this account.
-
Choose Save.
To manage ACM permissions in Amazon Private CA (Amazon CLI)
Use the create-permission command to assign permissions to ACM. You
must assign the necessary permissions (IssueCertificate,
GetCertificate, and ListPermissions) in order
for ACM to automatically renew your certificates.
$aws acm-pca create-permission \ --certificate-authority-arn arn:aws:acm-pca:region:account:certificate-authority/CA_ID\ --actionsIssueCertificateGetCertificateListPermissions\ --principal acm.amazonaws.com
Use the list-permissions command to list the permissions delegated by a CA.
$aws acm-pca list-permissions \ --certificate-authority-arn arn:aws:acm-pca:region:account:certificate-authority/CA_ID
Use the delete-permission command to revoke permissions assigned by a CA to an Amazon service principal.
$aws acm-pca delete-permission \ --certificate-authority-arn arn:aws:acm-pca:region:account:certificate-authority/CA_ID\ --principal acm.amazonaws.com