Customize OCSP URL for Amazon Private CA
Note
This topic is for customers who want to customize the public URL of the Online Certificate Status Protocol (OCSP) responder endpoint for branding or other purposes. If you plan to use the default configuration of Amazon Private CA managed OCSP, you can skip this topic and follow the configuration instructions in Configure revocation.
By default, when you enable OCSP for Amazon Private CA, each certificate that you issue contains the URL for the Amazon OCSP responder. This allows clients requesting a cryptographically secure connection to send OCSP validation queries directly to Amazon. However, in some cases it might be preferable to state a different URL in your certificates while still ultimately submitting OCSP queries to Amazon.
Note
For information about using a certificate revocation list (CRL) as an alternative or a supplement to OCSP, see Configure revocation and Planning a certificate revocation list (CRL).
Three elements are involved in configuring a custom URL for OCSP.
-
CA configuration – Specify a custom OCSP URL in the
RevocationConfigurationfor your CA as described in Example 2: Create a CA with OCSP and a custom CNAME enabled in Create a private CA in Amazon Private CA. -
DNS – Add a CNAME record to your domain configuration to map the URL appearing in the certificates to a proxy server URL. For more information, see Example 2: Create a CA with OCSP and a custom CNAME enabled in Create a private CA in Amazon Private CA.
-
Forwarding proxy server – Set up a proxy server that can transparently forward OCSP traffic that it receives to the Amazon OCSP responder.
The following diagram illustrates how these elements work together.
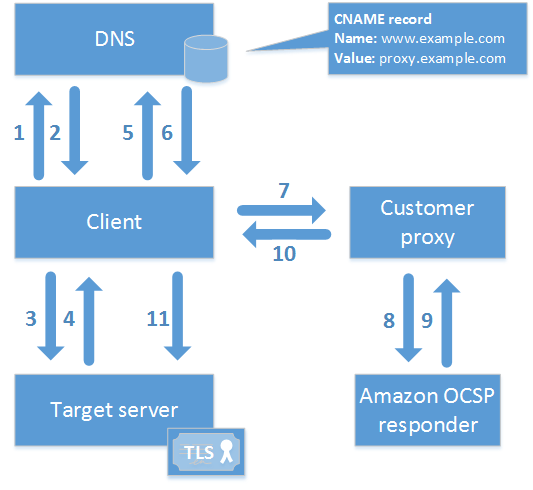
As shown in the diagram, the customized OCSP validation process involves the following steps:
-
Client queries DNS for the target domain.
-
Client receives the target IP.
-
Client opens a TCP connection with target.
-
Client receives target TLS certificate.
-
Client queries DNS for the OCSP domain listed in the certificate.
-
Client receives proxy IP.
-
Client sends OCSP query to proxy.
-
Proxy forwards query to the OCSP responder.
-
Responder returns certificate status to the proxy.
-
Proxy forwards certificate status to the client.
-
If certificate is valid, client begins TLS handshake.
Tip
This example can be implemented using Amazon CloudFront and Amazon Route 53 after you have configured a CA as described above.
-
In CloudFront, create a distribution and configure it as follows:
-
Create an alternate name that matches your custom CNAME.
-
Bind your certificate to it.
-
Set
ocsp.acm-pca.as the origin.<region>.amazonaws.com-
To use IPv6 connections, use the dualstack endpoint
acm-pca-ocsp.<region>.api.aws
-
-
Apply the
Managed-CachingDisabledpolicy. -
Set Viewer protocol policy to HTTP and HTTPS.
-
Set Allowed HTTP methods to GET, HEAD, OPTIONS, PUT, POST, PATCH, DELETE.
-
-
In Route 53, create a DNS record that maps your custom CNAME to the URL of the CloudFront distribution.
Using OCSP over IPv6
The default Amazon Private CA OCSP responder URL is IPv4-only. To use OCSP over IPv6, configure a custom OCSP URL for your CA. The URL can be either:
-
The FQDN of the dualstack PCA OCSP responder, which takes the form
acm-pca-ocsp.region-name.api.aws -
A CNAME record that you have configured to point at the dualstack OCSP responder, as explained above.