Trusted identity propagation overview
Trusted identity propagation is a feature of IAM Identity Center that enables administrators of Amazon Web Services services to grant permissions based on user attributes such as group associations. With trusted identity propagation, identity context is added to an IAM role to identify the user requesting access to Amazon resources. This context is propagated to other Amazon Web Services services.
Identity context comprises information that Amazon Web Services services use to make authorization decisions when they receive access requests. This information includes metadata that identifies the requester (for example, an IAM Identity Center user), the Amazon Web Services service to which access is requested (for example, Amazon Redshift), and the scope of access (for example, read only access). The receiving Amazon Web Services service uses this context, and any permissions assigned to the user, to authorize access to its resources.
Benefits of trusted identity propagation
Trusted identity propagation allows the administrators of Amazon Web Services services to grant permissions to resources, such as data, using the corporate identities of your workforce. In addition, they can audit who accessed what data by looking at service logs or Amazon CloudTrail. If you are an IAM Identity Center administrator, you may be asked by other Amazon Web Services service administrators to enable trusted identity propagation.
Enabling trusted identity propagation
The process of enabling trusted identity propagation involves the following two steps:
-
Enable IAM Identity Center and connect your existing source of identities to IAM Identity Center - You'll continue to manage your workforce identities in your existing source of identities; connecting it to IAM Identity Center creates a reference to your workforce that all Amazon Web Services services in your use case can share. It's also available for data owners to use in future use cases.
-
Connect the Amazon Web Services services in your use case to IAM Identity Center - The administrator of each Amazon Web Services service in the trusted identity propagation use case follows the guidance in the respective service documentation to connect the service to IAM Identity Center.
Note
If your use case involves a third-party or customer developed application, you enable trusted identity propagation by configuring a trust relationship between the identity provider that authenticates the application users and IAM Identity Center. This allows your application to take advantage of the trusted identity propagation flow previously described.
For more information, see Using applications with a trusted token issuer.
How trusted identity propagation works
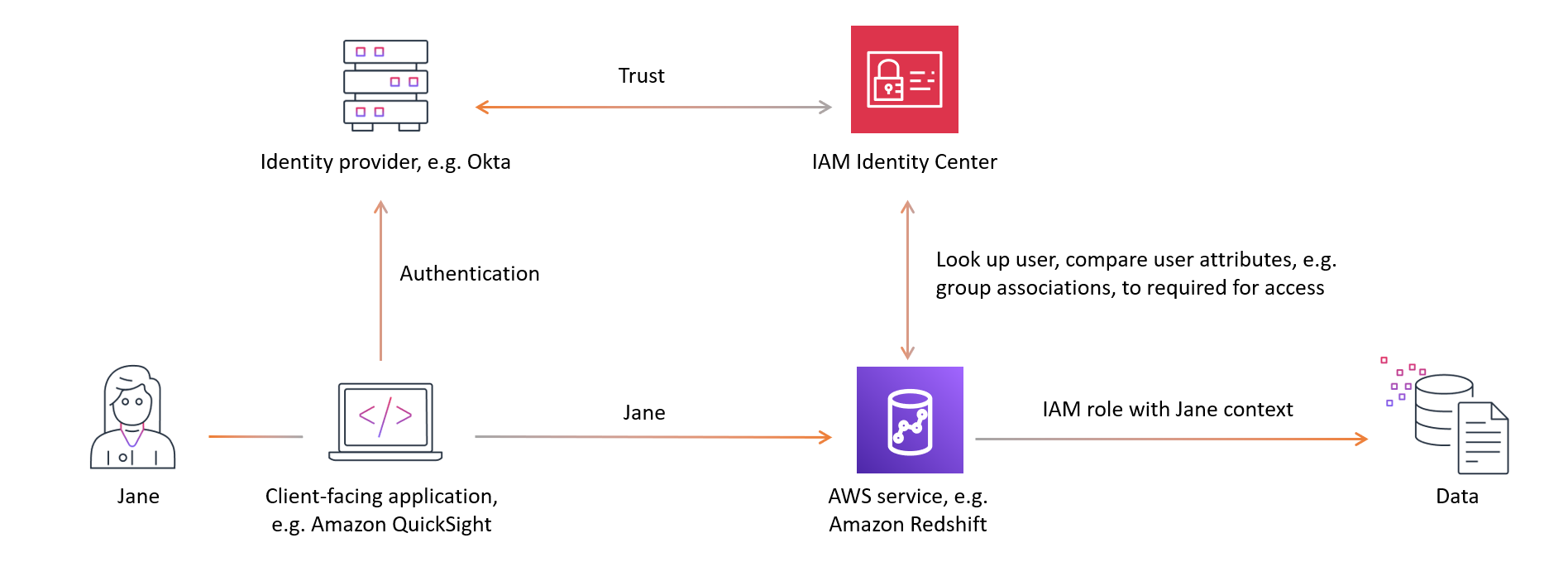
The following diagram shows the high-level workflow for trusted identity propagation:

-
Users authenticate with a client-facing application, for example Quick Suite.
-
The client-facing application requests access to use an Amazon Web Services service to query data and includes information on the user.
Note
Some trusted identity propagation use cases involve tools that interact with Amazon Web Services services using service drivers. You can find out if this applies to your use case in the use case guidance.
-
The Amazon Web Services service verifies the user identity with IAM Identity Center and compares the user attributes, like their group associations, with those required for access. The Amazon Web Services service authorizes the access so long as the user or their group has the necessary permissions.
-
Amazon Web Services services may log the user identifier in Amazon CloudTrail and in their service logs. Check the service documentation for details.
The following image provides an overview of the previously described steps in the trusted identity propagation workflow: