Get started with Amazon PrivateLink
This tutorial demonstrates how to send a request from an EC2 instance in a private subnet to Amazon CloudWatch using Amazon PrivateLink.
The following diagram provides an overview of this scenario. To connect from your computer
to the instance in the private subnet, you'll first connect to a bastion host in a public
subnet. Both the bastion host and the instance must use the same key pair. Because the
.pem file for the private key is on your computer, not the bastion host,
you'll use SSH key forwarding. Then, you can connect to the instance from the bastion host
without specifying the .pem file in the ssh command.
After you set up a VPC endpoint for CloudWatch, traffic from the instance that's destined for CloudWatch is
resolved to the endpoint network interface and then sent to CloudWatch using the VPC endpoint.
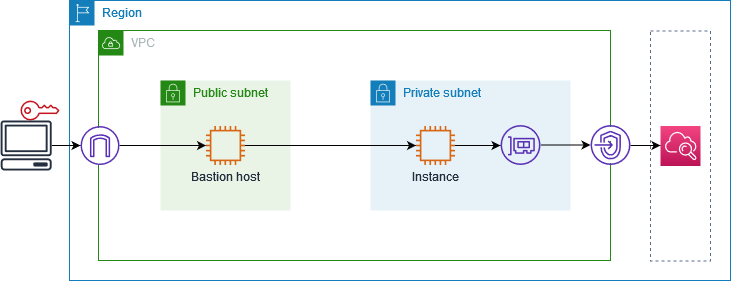
For testing purposes, you can use a single Availability Zone. In production, we recommend that you use at least two Availability Zones for low latency and high availability.
Tasks
Step 1: Create a VPC with subnets
Use the following procedure to create a VPC with a public subnet and a private subnet.
To create the VPC
-
Open the Amazon VPC console at https://console.amazonaws.cn/vpc/
. -
Choose Create VPC.
-
For Resources to create, choose VPC and more.
-
For Name tag auto-generation, enter a name for the VPC.
-
To configure the subnets, do the following:
-
For Number of Availability Zones, choose 1 or 2, depending on your needs.
-
For Number of public subnets, ensure that you have one public subnet per Availability Zone.
-
For Number of private subnets, ensure that you have one private subnet per Availability Zone.
-
-
Choose Create VPC.
Step 2: Launch the instances
Using the VPC that you created in the previous step, launch the bastion host in the public subnet and the instance in the private subnet.
Prerequisites
Create a key pair using the .pem format. You must choose this key pair when you launch both the bastion host and the instance.
Create a security group for the bastion host that allows inbound SSH traffic from the CIDR block for your computer.
Create a security group for the instance that allows inbound SSH traffic from the security group for the bastion host.
Create an IAM instance profile and attach the CloudWatchReadOnlyAccess policy.
To launch the bastion host
-
Open the Amazon EC2 console at https://console.amazonaws.cn/ec2/
. -
Choose Launch instance.
-
For Name, enter a name for your bastion host.
-
Keep the default image and instance type.
-
For Key pair, select your key pair.
-
For Network settings, do the following:
-
For VPC, choose your VPC.
-
For Subnet, choose the public subnet.
-
For Auto-assign public IP, choose Enable.
-
For Firewall, choose Select existing security group and then choose the security group for the bastion host.
-
-
Choose Launch instance.
To launch the instance
-
Open the Amazon EC2 console at https://console.amazonaws.cn/ec2/
. -
Choose Launch instance.
-
For Name, enter a name for your instance.
-
Keep the default image and instance type.
-
For Key pair, select your key pair.
-
For Network settings, do the following:
-
For VPC, choose your VPC.
-
For Subnet, choose the private subnet.
-
For Auto-assign public IP, choose Disable.
-
For Firewall, choose Select existing security group and then choose the security group for the instance.
-
-
Expand Advanced details. For IAM instance profile, choose your IAM instance profile.
-
Choose Launch instance.
Step 3: Test CloudWatch access
Use the following procedure to confirm that the instance can't access CloudWatch. You'll do so using a read-only Amazon CLI command for CloudWatch.
To test CloudWatch access
-
From your computer, add the key pair to the SSH agent using the following command, where
key.pemis the name of your .pem file.ssh-add ./key.pemIf you receive an error that permissions for your key pair are too open, run the following command, and then retry the previous command.
chmod 400 ./key.pem -
Connect to the bastion host from your computer. You must specify the
-Aoption, the instance user name (for example,ec2-user), and the public IP address of the bastion host.ssh -Aec2-user@bastion-public-ip-address -
Connect to the instance from the bastion host. You must specify the instance user name (for example,
ec2-user) and the private IP address of the instance.sshec2-user@instance-private-ip-address -
Run the CloudWatch list-metrics command on the instance as follows. For the
--regionoption, specify the Region where you created the VPC.aws cloudwatch list-metrics --namespace AWS/EC2 --regionus-east-1 -
After a few minutes, the command times out. This demonstrates that you can't access CloudWatch from the instance with the current VPC configuration.
Connect timeout on endpoint URL: https://monitoring.us-east-1.amazonaws.com/ -
Stay connected to your instance. After you create the VPC endpoint, you'll try this list-metrics command again.
Step 4: Create a VPC endpoint to access CloudWatch
Use the following procedure to create a VPC endpoint that connects to CloudWatch.
Prerequisite
Create a security group for the VPC endpoint that allows traffic to CloudWatch. For example, add a rule that allows HTTPS traffic from the VPC CIDR block.
To create a VPC endpoint for CloudWatch
Open the Amazon VPC console at https://console.amazonaws.cn/vpc/
. -
In the navigation pane, choose Endpoints.
-
Choose Create endpoint.
-
For Name tag, enter a name for the endpoint.
-
For Service category, choose Amazon Web Services services.
-
For Service, select com.amazonaws.
region.monitoring. -
For VPC, select your VPC.
-
For Subnets, select the Availability Zone and then select the private subnet.
-
For Security group, select the security group for the VPC endpoint.
-
For Policy, select Full access to allow all operations by all principals on all resources over the VPC endpoint.
-
(Optional) To add a tag, choose Add new tag and enter the tag key and the tag value.
-
Choose Create endpoint. The initial status is Pending. Before you go to the next step, wait until the status is Available. This can take a few minutes.
Step 5: Test the VPC endpoint
Verify that the VPC endpoint is sending requests from your instance to CloudWatch.
To test the VPC endpoint
Run the following command on your instance. For the --region option,
specify the Region where you created the VPC endpoint.
aws cloudwatch list-metrics --namespace AWS/EC2 --regionus-east-1
If you get a response, even a response with empty results, then you are connected to CloudWatch using Amazon PrivateLink.
If you get an UnauthorizedOperation error, ensure that the instance
has an IAM role that allows access to CloudWatch.
If the request times out, verify the following:
The security group for the endpoint allows traffic to CloudWatch.
The
--regionoption specifies the Region in which you created the VPC endpoint.
Step 6: Clean up
If you no longer need the bastion host and instance that you created for this tutorial, you can terminate them.
To terminate the instances
-
Open the Amazon EC2 console at https://console.amazonaws.cn/ec2/
. -
In the navigation pane, choose Instances.
-
Select both test instances and choose Instance state, Terminate instance.
-
When prompted for confirmation, choose Terminate.
If you no longer need the VPC endpoint, you can delete it.
To delete the VPC endpoint
Open the Amazon VPC console at https://console.amazonaws.cn/vpc/
. -
In the navigation pane, choose Endpoints.
-
Select the VPC endpoint.
-
Choose Actions, Delete VPC endpoints.
-
When prompted for confirmation, enter
deleteand then choose Delete.