本文属于机器翻译版本。若本译文内容与英语原文存在差异,则一律以英文原文为准。
为本地 Jupyter 环境安装策略和权限
您需要设置必要的权限和策略,以便在本地 Jupyter 环境中安排笔记本作业。IAM 用户需要权限才能向 A SageMaker I 提交作业,而笔记本作业本身承担的 IAM 角色需要访问资源的权限,具体视任务而定。下面将说明如何设置必要的权限和策略。
您需要安装两套权限。下图显示了在本地 Jupyter 环境中安排笔记本作业的权限结构。IAM 用户需要设置 IAM 权限才能向 A SageMaker I 提交任务。用户提交笔记本作业后,作业本身将代入一个 IAM 角色,该角色需要根据作业任务获得资源访问权限。
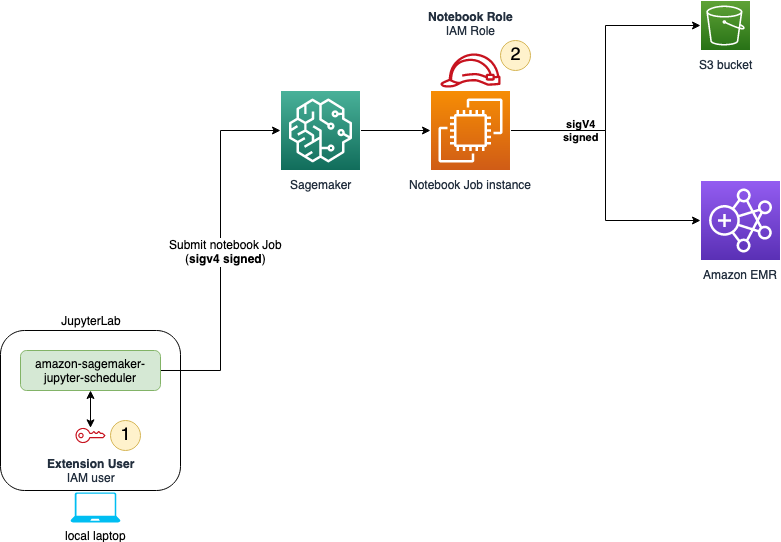
以下几节将帮助您为 IAM 用户和作业执行角色安装必要的策略和权限。
IAM 用户权限
向 SageMaker AI 提交任务的权限
要添加提交作业的权限,请完成以下步骤:
-
打开 IAM 控制台
。 -
在左侧面板中选择用户。
-
找到您的笔记本作业的 IAM 用户并选择用户名。
-
选择添加权限,然后从下拉菜单中选择创建内联策略。
-
选择 JSON 选项卡。
-
复制并粘贴以下策略:
Amazon KMS 权限策略(可选)
默认情况下,输入和输出 Amazon S3 存储桶使用服务器端加密进行加密,但您可以指定自定义 KMS 密钥来加密输出 Amazon S3 存储桶和附加到笔记本作业的存储卷中的数据。
如果要使用自定义 KMS 密钥,请重复前面的说明,附加以下策略,并提供自己的 KMS 密钥 ARN。
作业执行角色权限
信任关系
要修改作业执行角色信任关系,请完成以下步骤:
-
打开 IAM 控制台
。 -
在左侧面板中选择角色。
-
找到笔记本作业的作业执行角色并选择角色名称。
-
选择信任关系选项卡。
-
选择编辑信任策略。
-
复制并粘贴以下策略:
其他权限
提交后,笔记本作业需要访问资源的权限。以下说明向您介绍如何添加一组最低限度的权限。如果需要,您可根据笔记本作业的需求添加更多权限。要为作业执行角色添加权限,请完成以下步骤:
-
打开 IAM 控制台
。 -
在左侧面板中选择角色。
-
找到笔记本作业的作业执行角色并选择角色名称。
-
选择添加权限,然后从下拉菜单中选择创建内联策略。
-
选择 JSON 选项卡。
-
复制并粘贴以下策略:
-
添加对笔记本作业访问的其他资源的权限。
-
选择查看策略。
-
输入策略的名称。
-
选择创建策略。