本文属于机器翻译版本。若本译文内容与英语原文存在差异,则一律以英文原文为准。
多云环境的连接模式
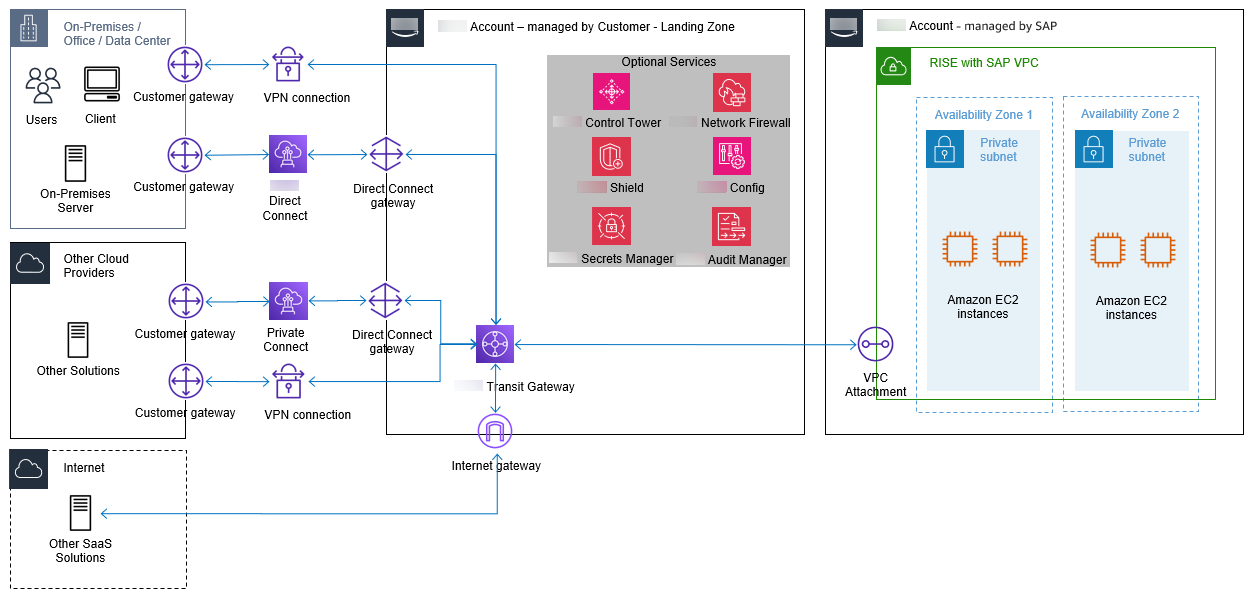
在复杂的连接场景中,您可能需要将 Amazon RISE 与 SAP 设置与本地、托管系统、各种 SaaS 解决方案和其他云服务提供商集成。
直接从 Amazon 环境中管理连接,使依赖关系与本地网络基础设施脱钩,从而提高整体环境的可用性和弹性。
您可以使用公有连接或私有连接将多云环境与 RISE 相连。
公有连接
连接通过公共互联网进行路由。此模式通常用于 RISE with SAP 与跨多个云运行的 SaaS 解决方案之间的连接。在建立通过公共互联网路由的连接时,请注意以下事项:
-
确保所有通信均已加密
-
使用弹性负载均衡器和 Shield 等 Amazon 服务保护端点 Amazon
-
使用 Amazon 监控终端节点 CloudWatch
-
确保托管的两个公有 IP 地址之间的流量通过网络路由 Amazon Amazon
私有连接
可使用以下三种方案,在不同的云服务提供商之间建立私有连接:
-
Site-to-site 通过公共互联网路由的 VPN 加密隧道
-
在托管基础架构中使用 Amazon Direct Connect 进行私有互连(使用 ExpressRoute 适用于 Azure 的 Azure 和谷歌云平台的谷歌专用互连)
-
在与多云连接提供商的设施中使用 Amazon Direct Connect 进行私有互连
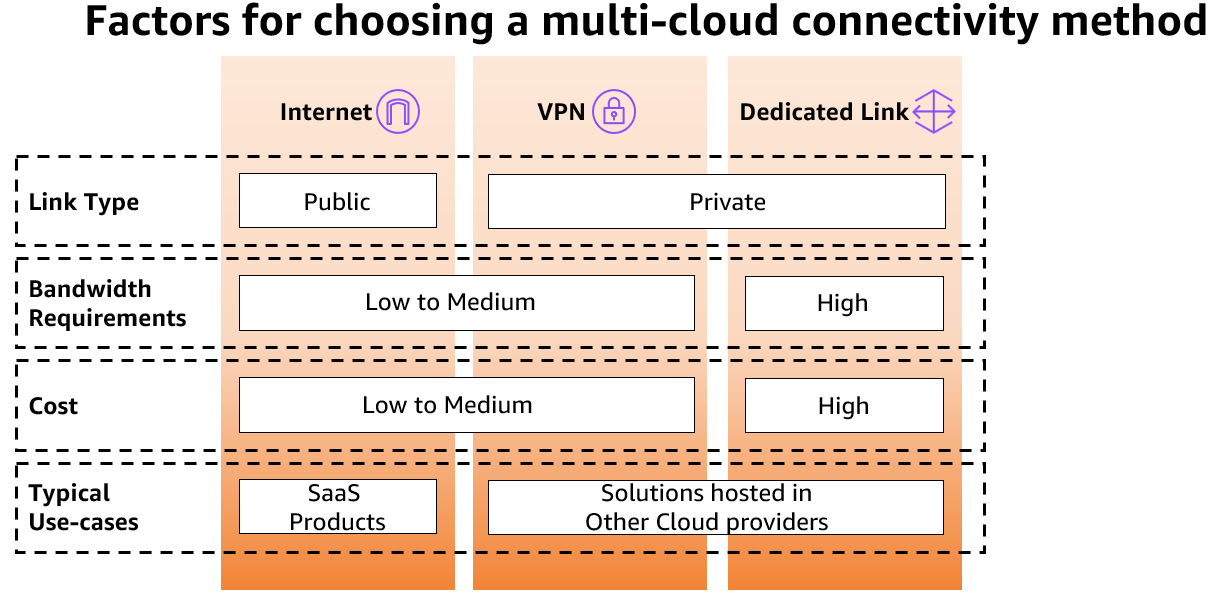
下图描述了选择多云连接方式时需考虑的因素。
有关更多信息,请参阅设计与 Microsoft Azure Amazon 之间的私有网络连接