Access Patterns for Accessing an ElastiCache Cache in an Amazon VPC
Amazon ElastiCache supports the following scenarios for accessing a cache in an Amazon VPC:
Contents
Accessing an ElastiCache Cache when it and the Amazon EC2 Instance are in the Same Amazon VPC
The most common use case is when an application deployed on an EC2 instance needs to connect to a cache in the same VPC.
The following diagram illustrates this scenario.
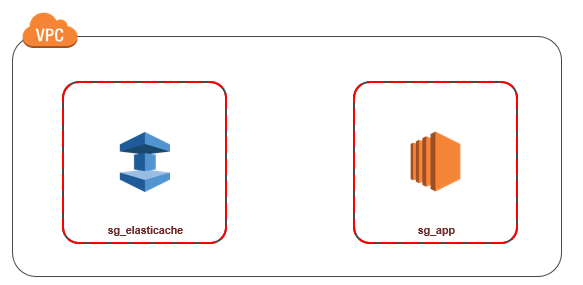
The simplest way to manage access between EC2 instances and caches in the same VPC is to do the following:
-
Create a VPC security group for your cache. This security group can be used to restrict access to the cache. For example, you can create a custom rule for this security group that allows TCP access using the port you assigned to the cache when you created it and an IP address you will use to access the cache.
The default port for Memcached caches is
11211.The default port for Valkey and Redis OSS caches is
6379. -
Create a VPC security group for your EC2 instances (web and application servers). This security group can, if needed, allow access to the EC2 instance from the Internet via the VPC's routing table. For example, you can set rules on this security group to allow TCP access to the EC2 instance over port 22.
-
Create custom rules in the security group for your cache that allow connections from the security group you created for your EC2 instances. This would allow any member of the security group to access the caches.
Note
If you are planning to use Local Zones, ensure that you have enabled them. When you create a subnet group in that local zone, your VPC is extended to that Local Zone and your VPC will treat the subnet as any subnet in any other Availability Zone. All relevant gateways and route tables will be automatically adjusted.
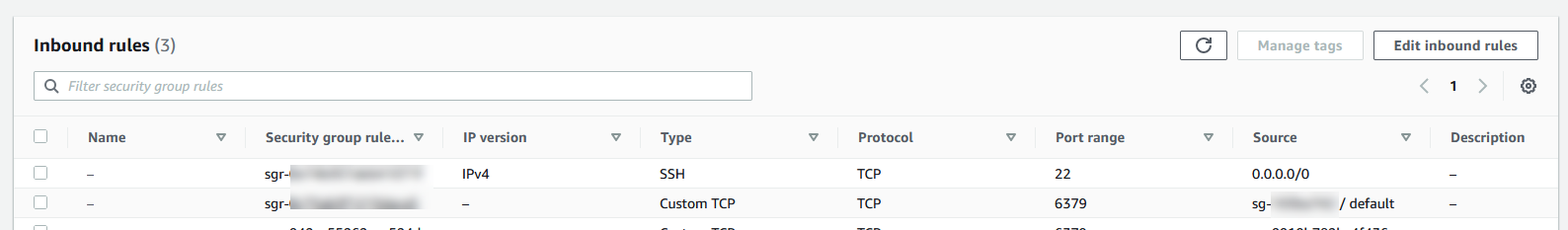
To create a rule in a VPC security group that allows connections from another security group
-
Sign in to the Amazon Management Console and open the Amazon VPC console at https://console.aws.amazon.com/vpc
. -
In the navigation pane, choose Security Groups.
-
Select or create a security group that you will use for your cache. Under Inbound Rules, select Edit Inbound Rules and then select Add Rule. This security group will allow access to members of another security group.
-
From Type choose Custom TCP Rule.
-
For Port Range, specify the port you used when you created your cache.
The default port for Memcached caches is
11211.The default port for Valkey and Redis OSS caches and replication groups is
6379. -
In the Source box, start typing the ID of the security group. From the list select the security group you will use for your Amazon EC2 instances.
-
-
Choose Save when you finish.
Accessing an ElastiCache Cache when it and the Amazon EC2 Instance are in Different Amazon VPCs
When your cache is in a different VPC from the EC2 instance you are using to access it, there are several ways to access the cache. If the cache and EC2 instance are in different VPCs but in the same region, you can use VPC peering. If the cache and the EC2 instance are in different regions, you can create VPN connectivity between regions.
Accessing an ElastiCache Cache when it and the Amazon EC2 Instance are in Different Amazon VPCs in the Same Region
The following diagram illustrates accessing a cache by an Amazon EC2 instance in a different Amazon VPC in the same region using an Amazon VPC peering connection.
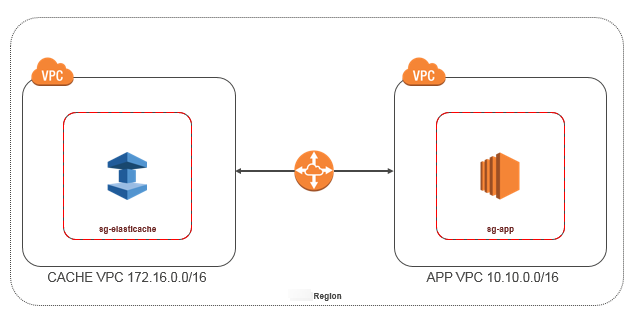
Cache accessed by an Amazon EC2 instance in a different Amazon VPC within the same Region - VPC Peering Connection
A VPC peering connection is a networking connection between two VPCs that enables you to route traffic between them using private IP addresses.
Instances in either VPC can communicate with each other as if they are within the same network.
You can create a VPC peering connection between your own Amazon VPCs, or with an Amazon VPC in another Amazon account within a single region.
To learn more about Amazon VPC peering, see the VPC documentation
Note
DNS name resolution may fail for peered VPCs, depending on the configurations applied to the ElastiCache VPC. To resolve this, both VPCs must be enabled for DNS hostnames and DNS resolution. For more information, see Enable DNS resolution for a VPC peering connection.
To access a cache in a different Amazon VPC over peering
-
Make sure that the two VPCs do not have an overlapping IP range or you will not be able to peer them.
-
Peer the two VPCs. For more information, see Creating and Accepting an Amazon VPC Peering Connection.
-
Update your routing table. For more information, see Updating Your Route Tables for a VPC Peering Connection
Following is what the route tables look like for the example in the preceeding diagram. Note that pcx-a894f1c1 is the peering connection.
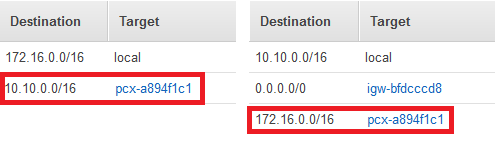
VPC Routing Table
-
Modify the Security Group of your ElastiCache cache to allow inbound connection from the Application security group in the peered VPC. For more information, see Reference Peer VPC Security Groups.
Accessing a cache over a peering connection will incur additional data transfer costs.
Using Transit Gateway
A transit gateway enables you to attach VPCs and VPN connections in the same Amazon Region and route traffic between them. A transit gateway works across Amazon accounts, and you can use Amazon Resource Access Manager to share your transit gateway with other accounts. After you share a transit gateway with another Amazon account, the account owner can attach their VPCs to your transit gateway. A user from either account can delete the attachment at any time.
You can enable multicast on a transit gateway, and then create a transit gateway multicast domain that allows multicast traffic to be sent from your multicast source to multicast group members over VPC attachments that you associate with the domain.
You can also create a peering connection attachment between transit gateways in different Amazon Regions. This enables you to route traffic between the transit gateways' attachments across different Regions.
For more information, see Transit gateways.
Accessing an ElastiCache Cache when it and the Amazon EC2 Instance are in Different Amazon VPCs in Different Regions
Using Transit VPC
An alternative to using VPC peering, another common strategy for connecting multiple, geographically disperse VPCs and remote networks is to create a transit VPC that serves as a global network transit center. A transit VPC simplifies network management and minimizes the number of connections required to connect multiple VPCs and remote networks. This design can save time and effort and also reduce costs, as it is implemented virtually without the traditional expense of establishing a physical presence in a colocation transit hub or deploying physical network gear.
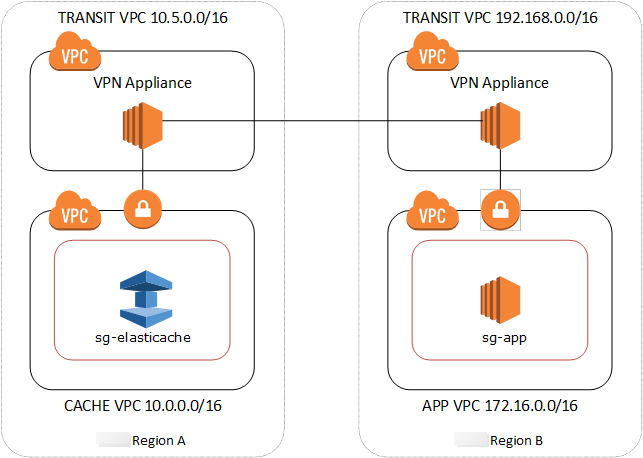
Connecting across different VPCs in different regions
Once the Transit Amazon VPC is established, an application deployed in a “spoke” VPC in one region can connect to an ElastiCache cache in a “spoke” VPC within another region.
To access a cache in a different VPC within a different Amazon Region
-
Deploy a Transit VPC Solution. For more information, see, Amazon Transit Gateway
. -
Update the VPC routing tables in the App and Cache VPCs to route traffic through the VGW (Virtual Private Gateway) and the VPN Appliance. In case of Dynamic Routing with Border Gateway Protocol (BGP) your routes may be automatically propagated.
-
Modify the Security Group of your ElastiCache cache to allow inbound connection from the Application instances IP range. Note that you will not be able to reference the application server Security Group in this scenario.
Accessing a cache across regions will introduce networking latencies and additional cross-region data transfer costs.
Accessing an ElastiCache Cache from an Application Running in a Customer's Data Center
Another possible scenario is a Hybrid architecture where clients or applications in the customer’s data center may need to access an ElastiCache cache in the VPC. This scenario is also supported providing there is connectivity between the customers’ VPC and the data center either through VPN or Direct Connect.
Accessing an ElastiCache Cache from an Application Running in a Customer's Data Center Using VPN Connectivity
The following diagram illustrates accessing an ElastiCache cache from an application running in your corporate network using VPN connections.
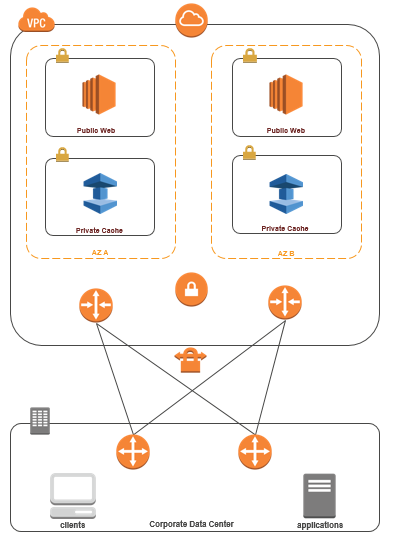
Connecting to ElastiCache from your data center via a VPN
To access a cache in a VPC from on-prem application over VPN connection
-
Establish VPN Connectivity by adding a hardware Virtual Private Gateway to your VPC. For more information, see Adding a Hardware Virtual Private Gateway to Your VPC
. -
Update the VPC routing table for the subnet where your ElastiCache cache is deployed to allow traffic from your on-premises application server. In case of Dynamic Routing with BGP your routes may be automatically propagated.
-
Modify the Security Group of your ElastiCache cache to allow inbound connection from the on-premises application servers.
Accessing a cache over a VPN connection will introduce networking latencies and additional data transfer costs.
Accessing an ElastiCache Cache from an Application Running in a Customer's Data Center Using Direct Connect
The following diagram illustrates accessing an ElastiCache cache from an application running on your corporate network using Direct Connect.
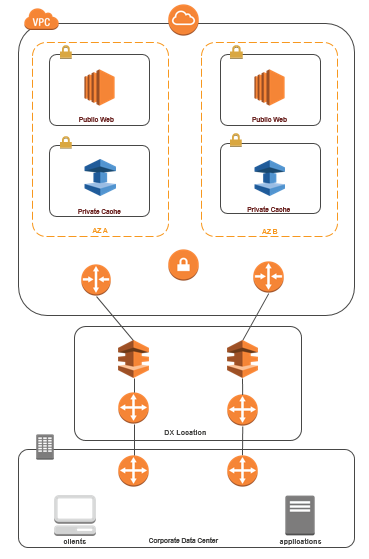
Connecting to ElastiCache from your data center via Direct Connect
To access an ElastiCache cache from an application running in your network using Direct Connect
-
Establish Direct Connect connectivity. For more information, see, Getting Started with Amazon Direct Connect
. -
Modify the Security Group of your ElastiCache cache to allow inbound connection from the on-premises application servers.
Accessing a cache over DX connection may introduce networking latencies and additional data transfer charges.