Understanding PostgreSQL roles and permissions
When you create an Aurora PostgreSQL DB cluster
using the Amazon Web Services Management Console, an
administrator account is created at the same time. By default, its name is
postgres, as shown in the following screenshot:
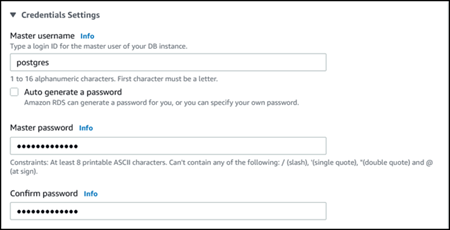
You can choose another name rather than accept the default (postgres). If you
do, the name you choose must start with a letter and be between 1 and 16 alphanumeric
characters. For simplicity's sake, we refer to this main user account by its default value
(postgres) throughout this guide.
If you use the create-db-cluster Amazon CLI rather than the
Amazon Web Services Management Console, you create the user name by passing it with the master-username
parameter. For more information, see Step 2: Create an
Aurora PostgreSQL DB cluster.
Whether you use the Amazon Web Services Management Console, the Amazon CLI, or the Amazon RDS API, and whether you use the default
postgres name or choose a different name, this first database user account is a
member of the rds_superuser group and has rds_superuser
privileges.