Amazon Key Management Service
Amazon Key Management Service (Amazon KMS) is an Amazon managed service that makes it easy for you to create and
control the keys used to encrypt and sign your data. The Amazon KMS keys that you
create in Amazon KMS are protected by FIPS 140-3 Security Level 3
validated hardware security modules (HSM)
Why use Amazon KMS?
When you encrypt data, you need to protect your encryption key. If you encrypt your key, you need to protect its encryption key. Eventually, you must protect the highest level encryption key (known as a root key) in the hierarchy that protects your data. That's where Amazon KMS comes in.

Amazon KMS protects your root keys. KMS keys are created, managed, used, and deleted entirely within Amazon KMS. They never leave the service unencrypted. To use or manage your KMS keys, you call Amazon KMS.
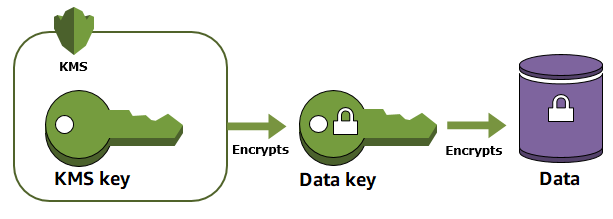
Additionally, you can create and manage key policies in Amazon KMS, ensuring that only trusted users have access to KMS keys.
Amazon KMS in Amazon Web Services Regions
The Amazon Web Services Regions in which Amazon KMS is supported are listed in Amazon Key Management Service Endpoints and Quotas. If an Amazon KMS feature is not supported in an Amazon Web Services Region that Amazon KMS supports, the regional difference is described in the topic about the feature.
Amazon KMS pricing
As with other Amazon products, using Amazon KMS does not require contracts or minimum purchases.
For more information about Amazon KMS pricing, see Amazon Key Management Service
Pricing
Amazon KMS service level agreement
Amazon Key Management Service is backed by a service level
agreement