Amazon KMS keys
The KMS keys that you create and manage for use in your own cryptographic applications
are of a type known as customer managed keys. Customer managed keys can also be used in
conjunction with Amazon services that use KMS keys to encrypt the data the service stores on
your behalf. Customer managed keys are recommended for customers who want full control over the
lifecycle and usage of their keys. There is a monthly cost to have a customer managed key in your
account. In addition, requests use and/or manage the key incur a usage cost. See Amazon Key Management Service Pricing
There are cases where a customer might want an Amazon service to encrypt their data, but
they don’t want the overhead of managing keys and don’t want to pay for a key. An
Amazon managed key is a KMS key that exists in your account, but can
only be used under certain circumstances. Specifically, it can only be used in the context of
the Amazon service you’re operating in and it can only be used by principals within the account
that the key exists. You cannot manage anything about the lifecycle or permissions of these
keys. As you use encryption features in Amazon services, you may see Amazon managed keys; they
use an alias of the form “aws<service code>”. For example, an aws/ebs key
can only be used to encrypt EBS volumes and only for volumes used by IAM principals in the
same account as the key. Think of an Amazon managed key that is scoped down for use only by
users in your account for resources in your account. You cannot share resources encrypted
under an Amazon managed key with other accounts. While an Amazon managed key is free to exist in
your account, you are charged for any use of this key type by the Amazon service that is
assigned to the key.
Amazon managed keys are a legacy key type that is no longer being created for new Amazon services as of 2021. Instead, new (and legacy) Amazon services are using what’s known as an Amazon owned key to encrypt customer data by default. An Amazon owned key is a KMS key that is in an account managed by the Amazon service, so the service operators have the ability to manage its lifecycle and usage permissions. By using Amazon owned keys, Amazon services can transparently encrypt your data and allow for easy cross-account or cross-region sharing of data without you needing to worry about key permissions. Use Amazon owned keys for encryption-by-default workloads that provide easier, more automated data protection. Because these keys are owned and managed by Amazon, you are not charged for their existence or their usage, you cannot change their policies, you cannot audit activities on these keys, and you cannot delete them. Use customer managed keys when control is important, but use Amazon owned keys when convenience is most important.
| Customer managed keys | Amazon managed keys | Amazon owned keys | |
| Key policy | Exclusively controlled by the customer | Controlled by service; viewable by customer | Exclusively controlled and only viewable by the Amazon service that encrypts your data |
| Logging | CloudTrail customer trail or event data store | CloudTrail customer trail or event data store | Not viewable by the customer |
| Lifecycle management | Customer manages rotation, deletion and Regional location | Amazon KMS manages rotation (annual), deletion, and Regional location | Amazon Web Services service manages rotation, deletion, and Regional location |
| Pricing |
Monthly fee for existence of keys (pro-rated hourly). Also charged for key usage |
No monthly fee; but the caller is charged for API usage on these keys | No charges to customer |
The KMS keys that you create are customer managed keys. Amazon Web Services services that use KMS keys to encrypt your service resources often create keys for you. KMS keys that Amazon Web Services services create in your Amazon account are Amazon managed keys. KMS keys that Amazon Web Services services create in a service account are Amazon owned keys.
| Type of KMS key | Can view KMS key metadata | Can manage KMS key | Used only for my Amazon Web Services account | Automatic rotation | Pricing |
|---|---|---|---|---|---|
| Customer managed key | Yes | Yes | Yes | Optional. | Monthly fee (pro-rated hourly) Per-use fee |
| Amazon managed key | Yes | No | Yes | Required. Every year (approximately 365 days). | No monthly fee Per-use fee (some Amazon Web Services services pay this fee for you) |
| Amazon owned key | No | No | No | The Amazon Web Services service manages the rotation strategy | No fees |
Amazon services that integrate with Amazon KMS differ in their support for KMS keys. Some Amazon services encrypt your data by default with an Amazon owned key or an Amazon managed key. Some Amazon services support customer managed keys. Other Amazon services support all types of KMS keys to allow you the ease of an Amazon owned key, the visibility of an Amazon managed key, or the control of a customer managed key. For detailed information about the encryption options that an Amazon service offers, see the Encryption at Rest topic in the user guide or the developer guide for the service.
Customer managed keys
The KMS keys that you create are customer managed keys. Customer managed keys are KMS keys in your Amazon Web Services account that you create, own, and manage. You have full control over these KMS keys, including establishing and maintaining their key policies, IAM policies, and grants, enabling and disabling them, rotating their cryptographic material, adding tags, creating aliases that refer to the KMS keys, and scheduling the KMS keys for deletion.
Customer managed keys appear on the Customer managed keys page of the Amazon Web Services Management Console
for Amazon KMS. To definitively identify a customer managed key, use the DescribeKey operation. For customer managed keys,
the value of the KeyManager field of the DescribeKey response is
CUSTOMER.
You can use your customer managed key in cryptographic operations and audit usage in Amazon CloudTrail logs. In addition, many Amazon services that integrate with Amazon KMS let you specify a customer managed key to protect the data stored and managed for you.
Customer managed keys incur a monthly fee and a fee for use in excess of the free tier. They
are counted against the Amazon KMS quotas for your account. For
details, see Amazon Key Management Service Pricing
Amazon managed keys
Amazon managed keys are KMS keys in your account
that are created, managed, and used on your behalf by an Amazon service integrated with Amazon KMS
Some Amazon services let you choose an Amazon managed key or a customer managed key to protect your resources in that service. In general, unless you are required to control the encryption key that protects your resources, an Amazon managed key is a good choice. You don't have to create or maintain the key or its key policy, and there's never a monthly fee for an Amazon managed key.
You have permission to view the Amazon managed keys in your account, view their key policies, and audit their use in Amazon CloudTrail logs. However, you cannot change any properties of Amazon managed keys, rotate them, change their key policies, or schedule them for deletion. And, you cannot use Amazon managed keys in cryptographic operations directly; the service that creates them uses them on your behalf.
Resource control policies in your organization do not apply to Amazon managed keys.
Amazon managed keys appear on the Amazon managed keys page of the
Amazon Web Services Management Console for Amazon KMS. You can also identify Amazon managed keys by their aliases, which have
the format aws/, such as
service-nameaws/redshift. To definitively identify an Amazon managed keys, use the DescribeKey operation. For
Amazon managed keys, the value of the KeyManager field of the
DescribeKey response is Amazon.
All Amazon managed keys are automatically rotated every year. You cannot change this rotation schedule.
Note
In May 2022, Amazon KMS changed the rotation schedule for Amazon managed keys from every three years (approximately 1,095 days) to every year (approximately 365 days).
There is no monthly fee for Amazon managed keys. They can be subject to fees for use in
excess of the free tier, but some Amazon services cover these costs for you. For details, see
the Encryption at Rest topic in the user guide or
developer guide for the service. For details, see Amazon Key Management Service
Pricing
Amazon managed keys do not count against resource quotas on the number of KMS keys in each Region of your account. But when used on behalf of a principal in your account, the KMS keys count against request quotas. For details, see Quotas.
Amazon owned keys
Amazon owned keys are a collection of KMS keys that an Amazon service owns and manages for use in multiple Amazon Web Services accounts. Although Amazon owned keys are not in your Amazon Web Services account, an Amazon service can use an Amazon owned key to protect the resources in your account.
Some Amazon services let you choose an Amazon owned key or a customer managed key. In general, unless you are required to audit or control the encryption key that protects your resources, an Amazon owned key is a good choice. Amazon owned keys are completely free of charge (no monthly fees or usage fees), they do not count against the Amazon KMS quotas for your account, and they're easy to use. You don't need to create or maintain the key or its key policy.
The rotation of Amazon owned keys varies across services. For information about the rotation of a particular Amazon owned key, see the Encryption at Rest topic in the user guide or developer guide for the service.
Amazon KMS key hierarchy
Your key hierarchy starts with a top-level logical key, an Amazon KMS key. A KMS key represents a container for top-level key material and is uniquely defined within the Amazon service namespace with an Amazon Resource Name (ARN). The ARN includes a uniquely generated key identifier, a key ID. A KMS key is created based on a user-initiated request through Amazon KMS. Upon reception, Amazon KMS requests the creation of an initial HSM backing key (HBK) to be placed into the KMS key container. The HBK is generated on an HSM in the domain and is designed never to be exported from the HSM in plaintext. Instead, the HBK is exported encrypted under HSM-managed domain keys. These exported HBKs are referred to as exported key tokens (EKTs).
The EKT is exported to a highly durable, low-latency storage. For example, suppose you receive an ARN to the logical KMS key. This represents the top of a key hierarchy, or cryptographic context, for you. You can create multiple KMS keys within your account and set policies on your KMS keys like any other Amazon named resource.
Within the hierarchy of a specific KMS key, the HBK can be thought of as a version of the KMS key. When you want to rotate the KMS key through Amazon KMS, a new HBK is created and associated with the KMS key as the active HBK for the KMS key. The older HBKs are preserved and can be used to decrypt and verify previously protected data. But only the active cryptographic key can be used to protect new information.
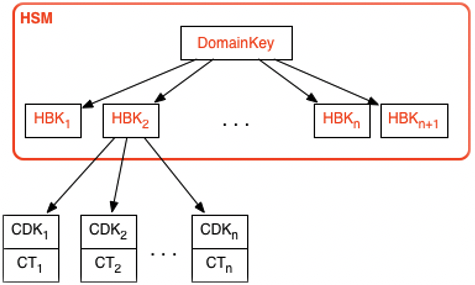
You can make requests through Amazon KMS to use your KMS keys to directly protect information or request additional HSM-generated keys that are protected under your KMS key. These keys are called customer data keys, or CDKs. CDKs can be returned encrypted as ciphertext (CT), in plaintext, or both. All objects encrypted under a KMS key (either customer-supplied data or HSM-generated keys) can be decrypted only on an HSM via a call through Amazon KMS.
The returned ciphertext, or the decrypted payload, is never stored within Amazon KMS. The information is returned to you over your TLS connection to Amazon KMS. This also applies to calls made by Amazon services on your behalf.
The key hierarchy and the specific key properties appear in the following table.
| Key | Description | Lifecycle |
|---|---|---|
|
Domain key |
A 256-bit AES-GCM key only in memory of an HSM used to wrap versions of the KMS keys, the HSM backing keys. |
Rotated daily1 |
|
HSM backing key |
A 256-bit symmetric key or RSA or elliptic curve private key, used to protect customer data and keys and stored encrypted under domain keys. One or more HSM backing keys comprise the KMS key, represented by the keyId. |
Rotated yearly2 (optional config.) |
|
Derived encryption key |
A 256-bit AES-GCM key only in memory of an HSM used to encrypt customer data and keys. Derived from an HBK for each encryption. |
Used once per encrypt and regenerated on decrypt |
|
Customer data key |
User-defined symmetric or asymmetric key exported from HSM in plaintext and ciphertext. Encrypted under an HSM backing key and returned to authorized users over TLS channel. |
Rotation and use controlled by application |
1 Amazon KMS might from time to time relax domain key rotation to at most weekly to account for domain administration and configuration tasks.
2 Default Amazon managed keys created and managed by Amazon KMS on your behalf are automatically rotated annually.
Key identifiers (KeyId)
Key identifiers act like names for your KMS keys. They help you to recognize your KMS keys in the console. You use them to indicate which KMS keys you want to use in Amazon KMS API operations, key policies, IAM policies, and grants. The key identifier values are completely unrelated to the key material associated with the KMS key.
Amazon KMS defines several key identifiers. When you create a KMS key, Amazon KMS generates a key ARN and key ID, which are properties of the KMS key. When you create an alias, Amazon KMS generates an alias ARN based on the alias name that you define. You can view the key and alias identifiers in the Amazon Web Services Management Console and in the Amazon KMS API.
In the Amazon KMS console, you can view and filter KMS keys by their key ARN, key ID, or alias name, and sort by key ID and alias name. For help finding the key identifiers in the console, see Find the key ID and key ARN.
In the Amazon KMS API, the parameters you use to identify a KMS key are named
KeyId or a variation, such as TargetKeyId or
DestinationKeyId. However, the values of those parameters are not limited to
key IDs. Some can take any valid key identifier. For information about the values for each
parameter, see the parameter description in the Amazon Key Management Service API Reference.
Note
When using the Amazon KMS API, be careful about the key identifier that you use. Different APIs require different key identifiers. In general, use the most complete and practical key identifier for your task.
Amazon KMS supports the following key identifiers.
- Key ARN
-
The key ARN is the Amazon Resource Name (ARN) of a KMS key. It is a unique, fully qualified identifier for the KMS key. A key ARN includes the Amazon Web Services account, Region, and the key ID. For help finding the key ARN of a KMS key, see Find the key ID and key ARN.
The format of a key ARN is as follows:
arn:<partition>:kms:<region>:<account-id>:key/<key-id>The following is an example key ARN for a single-Region KMS key.
arn:aws:kms:us-west-2:111122223333:key/1234abcd-12ab-34cd-56ef-1234567890abThe
key-idelement of the key ARNs of multi-Region keys begin with themrk-prefix. The following is an example key ARN for a multi-Region key.arn:aws:kms:us-west-2:111122223333:key/mrk-1234abcd12ab34cd56ef1234567890ab
- Key ID
-
The key ID uniquely identifies a KMS key within an account and Region. For help finding the key ID of a KMS key, see Find the key ID and key ARN.
The following is an example key ID for a single-Region KMS key.
1234abcd-12ab-34cd-56ef-1234567890abThe key IDs of multi-Region keys begin with the
mrk-prefix. The following is an example key ID for a multi-Region key.mrk-1234abcd12ab34cd56ef1234567890ab - Alias ARN
-
The alias ARN is the Amazon Resource Name (ARN) of an Amazon KMS alias. It is a unique, fully qualified identifier for the alias, and for the KMS key it represents. An alias ARN includes the Amazon Web Services account, Region, and the alias name.
At any given time, an alias ARN identifies one particular KMS key. However, because you can change the KMS key associated with the alias, the alias ARN can identify different KMS keys at different times. For help finding the alias ARN of a KMS key, see Find the alias name and alias ARN for a KMS key.
The format of an alias ARN is as follows:
arn:<partition>:kms:<region>:<account-id>:alias/<alias-name>The following is the alias ARN for a fictitious
ExampleAlias.arn:aws:kms:us-west-2:111122223333:alias/ExampleAlias - Alias name
-
The alias name is a string of up to 256 characters. It uniquely identifies an associated KMS key within an account and Region. In the Amazon KMS API, alias names always begin with
alias/. For help finding the alias name of a KMS key, see Find the alias name and alias ARN for a KMS key.The format of an alias name is as follows:
alias/<alias-name>For example:
alias/ExampleAliasThe
aws/prefix for an alias name is reserved for Amazon managed keys. You cannot create an alias with this prefix. For example, the alias name of the Amazon managed key for Amazon Simple Storage Service (Amazon S3) is the following.alias/aws/s3